CAS-003 | Top Tips Of Up To Date CAS-003 Practice Exam
Your success in CompTIA CAS-003 is our sole target and we develop all our CAS-003 braindumps in a way that facilitates the attainment of this target. Not only is our CAS-003 study material the best you can find, it is also the most detailed and the most updated. CAS-003 Practice Exams for CompTIA CAS-003 are written to the highest standards of technical accuracy.
Also have CAS-003 free dumps questions for you:
NEW QUESTION 1
Which of the following BEST represents a risk associated with merging two enterprises during an acquisition?
- A. The consolidation of two different IT enterprises increases the likelihood of the data loss because there are now two backup systems
- B. Integrating two different IT systems might result in a successful data breach if threat intelligence is not shared between the two enterprises
- C. Merging two enterprise networks could result in an expanded attack surface and could cause outages if trust and permission issues are not handled carefully
- D. Expanding the set of data owners requires an in-depth review of all data classification decisions, impacting availability during the review
Answer: C
NEW QUESTION 2
A security engineer is embedded with a development team to ensure security is built into products being developed. The security engineer wants to ensure developers are not blocked by a large number of security requirements applied at specific schedule points. Which of the following solutions BEST meets the engineer’s goal?
- A. Schedule weekly reviews of al unit test results with the entire development team and follow up between meetings with surprise code inspections.
- B. Develop and implement a set of automated security tests to be installed on each development team leader’s workstation.
- C. Enforce code quality and reuse standards into the requirements definition phase of the waterfall development process.
- D. Deploy an integrated software tool that builds and tests each portion of code committed by developers and provides feedback.
Answer: C
NEW QUESTION 3
A recent penetration test identified that a web server has a major vulnerability. The web server hosts a critical shipping application for the company and requires 99.99% availability. Attempts to fix the vulnerability would likely break the application. The shipping application is due to be replaced in the next three months. Which of the following would BEST secure the web server until the replacement web server is ready?
- A. Patch management
- B. Antivirus
- C. Application firewall
- D. Spam filters
- E. HIDS
Answer: E
NEW QUESTION 4
An insurance company is looking to purchase a smaller company in another country. Which of the following tasks would the security administrator perform as part of the security due diligence?
- A. Review switch and router configurations
- B. Review the security policies and standards
- C. Perform a network penetration test
- D. Review the firewall rule set and IPS logs
Answer: B
Explanation:
IT security professionals should have a chance to review the security controls and practices of a company targeted for acquisition. Any irregularities that are found should be reported to management so that expenses and concerns are properly identified.
Incorrect Answers:
A: Due diligence entails ensuring controls implemented by an organization continues to provide the required level of protection. Reviewing switch and router configurations are not part of this process. C: Due diligence entails ensuring controls implemented by an organization continues to provide the required level of protection. Performing a network penetration test is not part of this process.
D: Due diligence entails ensuring controls implemented by an organization continues to provide the required level of protection. Reviewing the firewall rule set and IPS logs are not part of this process. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 270, 332
NEW QUESTION 5
The security configuration management policy states that all patches must undergo testing procedures before being moved into production. The sec… analyst notices a single web application server has been downloading and applying patches during non-business hours without testing. There are no apparent adverse reaction, server functionality does not seem to be affected, and no malware was found after a scan. Which of the following action should the analyst take?
- A. Reschedule the automated patching to occur during business hours.
- B. Monitor the web application service for abnormal bandwidth consumption.
- C. Create an incident ticket for anomalous activity.
- D. Monitor the web application for service interruptions caused from the patchin
Answer: C
NEW QUESTION 6
A cybersecurity analyst is hired to review the security the posture of a company. The cybersecurity analyst notice a very high network bandwidth consumption due to SYN floods from a small number of IP addresses. Which of the following would be the BEST action to take to support incident response?
- A. Increase the company's bandwidth.
- B. Apply ingress filters at the routers.
- C. Install a packet capturing tool.
- D. Block all SYN packet
Answer: B
NEW QUESTION 7
DRAG DROP
A security consultant is considering authentication options for a financial institution. The following authentication options are available security mechanism to the appropriate use case. Options may be used once.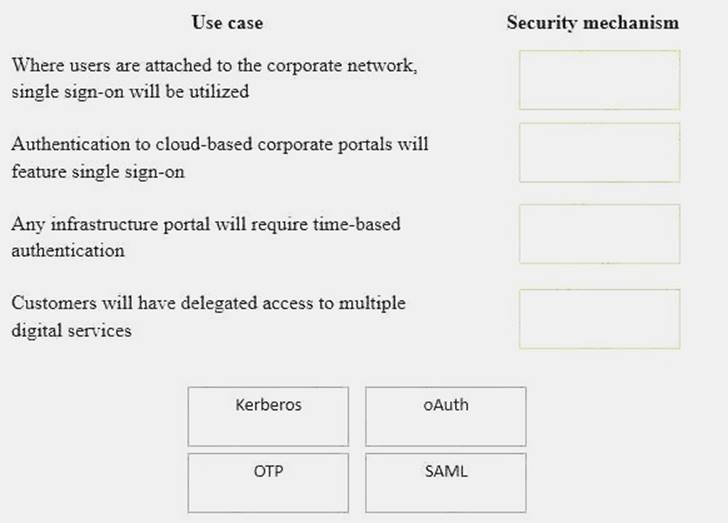
Solution:
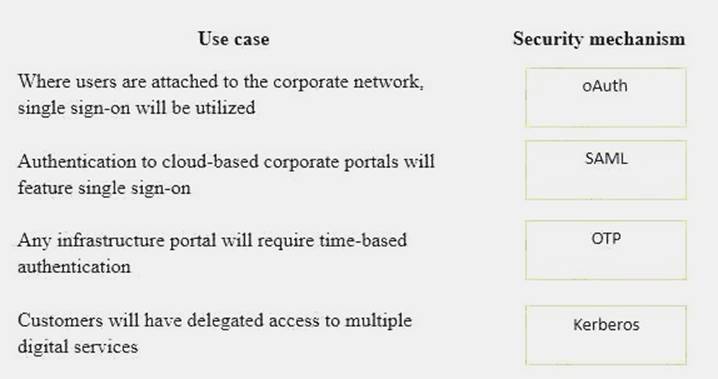
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
An organization uses IP address block 203.0.113.0/24 on its internal network. At the border router, the network administrator sets up rules to deny packets with a source address in this subnet from entering the network, and to deny packets with a destination address in this subnet from leaving the network. Which of the following is the administrator attempting to prevent?
- A. BGP route hijacking attacks
- B. Bogon IP network traffic
- C. IP spoofing attacks
- D. Man-in-the-middle attacks
- E. Amplified DDoS attacks
Answer: C
Explanation:
The IP address block 203.0.113.0/24 is used on the internal network. Therefore, there should be no traffic coming into the network claiming to be from an address in the 203.0.113.0/24 range. Similarly, there should be no outbound traffic destined for an address in the 203.0.113.0/24 range. So this has been blocked at the firewall. This is to protect against IP spoofing attacks where an attacker external to the network sends data claiming to be from an internal computer with an address in the 203.0.113.0/24 range.
IP spoofing, also known as IP address forgery or a host file hijack, is a hijacking technique in which a cracker masquerades as a trusted host to conceal his identity, spoof a Web site, hijack browsers, or
gain access to a network. Here's how it works: The hijacker obtains the IP address of a legitimate host and alters packet headers so that the legitimate host appears to be the source.
When IP spoofing is used to hijack a browser, a visitor who types in the URL (Uniform Resource Locator) of a legitimate site is taken to a fraudulent Web page created by the hijacker. For example, if the hijacker spoofed the Library of Congress Web site, then any Internet user who typed in the URL www.loc.gov would see spoofed content created by the hijacker.
If a user interacts with dynamic content on a spoofed page, the hijacker can gain access to sensitive information or computer or network resources. He could steal or alter sensitive data, such as a credit card number or password, or install malware. The hijacker would also be able to take control of a compromised computer to use it as part of a zombie army in order to send out spam.
Incorrect Answers:
A: BGP is a protocol used to exchange routing information between networks on the Internet. BGP route hijacking is the process of using BGP to manipulate Internet routing paths. The firewall configuration in this question will not protect against BGP route hijacking attacks.
B: Bogon is an informal name for an IP packet on the public Internet that claims to be from an area of the IP address space reserved, but not yet allocated or delegated by the Internet Assigned Numbers Authority (IANA) or a delegated Regional Internet Registry (RIR). The firewall configuration in this question will not protect against Bogon IP network traffic.
D: A man-in-the-middle attack is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other. The firewall configuration in this question will not protect against a man-in-the-middle attack.
E: A distributed denial-of-service (DDoS) attack occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. Amplified DDoS attacks use more systems to ‘amplify’ the attack. The firewall configuration in this question will not protect against a DDoS attack.
References:
http://searchsecurity.techtargHYPERLINK "http://searchsecurity.techtarget.com/definition/IPspoofing" et.com/definition/IP-spoofing
NEW QUESTION 9
A small company is developing a new Internet-facing web application. The security requirements are: Users of the web application must be uniquely identified and authenticated.
Users of the web application will not be added to the company’s directory services. Passwords must not be stored in the code.
Which of the following meets these requirements?
- A. Use OpenID and allow a third party to authenticate users.
- B. Use TLS with a shared client certificate for all users.
- C. Use SAML with federated directory services.
- D. Use Kerberos and browsers that support SAM
Answer: A
Explanation:
Users create accounts by selecting an OpenID identity provider, and then use those accounts to sign onto any website which accepts OpenID authentication.
OpenID is an open standard and decentralized protocol by the non-profit OpenID Foundation that allows users to be authenticated by certain co-operating sites (known as Relying Parties or RP) using a third party service. This eliminates the need for webmasters to provide their own ad hoc systems and allowing users to consolidate their digital identities. In other words, users can log into multiple unrelated websites without having to register with their information over and over again.
Several large organizations either issue or accept OpenIDs on their websites according to the OpenID Foundation: AOL, Blogger, Flickr, France Telecom, Google, Hyves, LiveJournal, Microsoft (provider name Microsoft account), Mixi, Myspace, Novell, Orange, Sears, Sun, Telecom Italia, Universal Music Group, VeriSign, WordPress, and Yahoo!. Other providers include BBC, IBM, PayPal, and Steam. Incorrect Answers:
B: The question states that users of the web application must be uniquely identified and authenticated. A shared client certificate for all users does not meet this requirement.
C: The question states that users of the web application will not be added to the company’s directory services. SAML with federated directory services would require that the users are added to the directory services.
D: The question states that users of the web application must be uniquely identified and authenticated. Kerberos and browsers that support SAML provides no authentication mechanism. References:
https://en.wikipedia.org/wiki/OpenID
NEW QUESTION 10
Compliance with company policy requires a quarterly review of firewall rules. A new administrator is asked to conduct this review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more restrictive. Given the following information answer the questions below:
User Subnet: 192.168.1.0/24 Server Subnet: 192.168.2.0/24 Finance Subnet:192.168.3.0/24 Instructions: To perform the necessary tasks, please modify the DST port, Protocol, Action, and/or Rule Order columns. Firewall ACLs are read from the top down
Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this issue.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.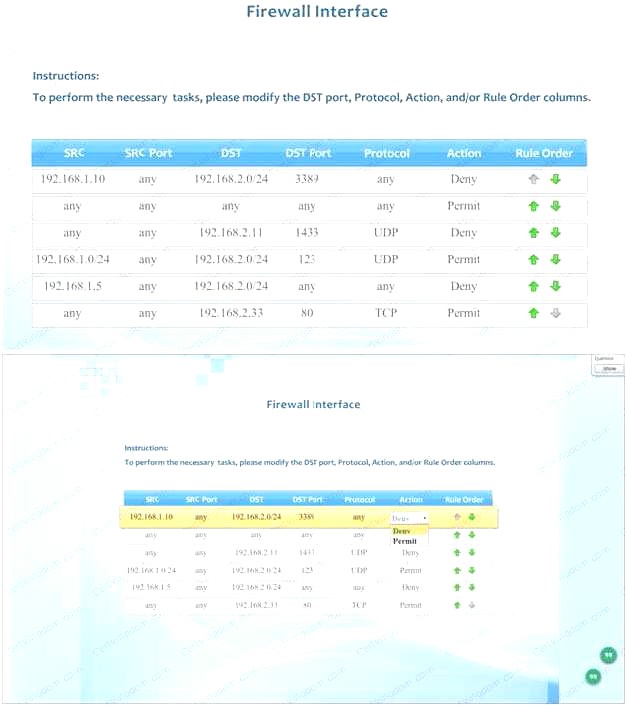
- A. Check the answer below
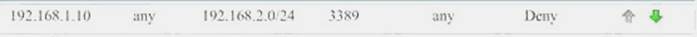
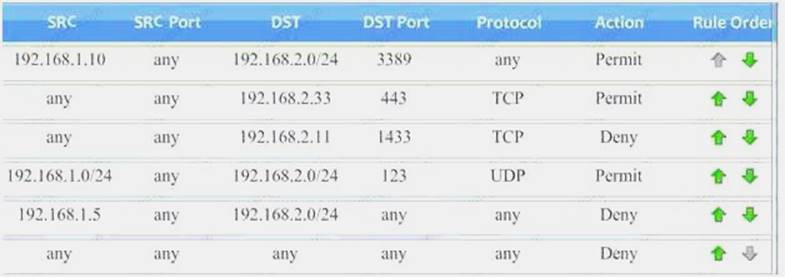 Task 1) An administrator added a rule to allow their machine terminal server access to the server subne
Task 1) An administrator added a rule to allow their machine terminal server access to the server subne - B. This rule is not workin
- C. Identify the rule and correct this issue.The rule shown in the image below is the rule in questio
- D. It is not working because the action is set to Den
- E. This needs to be set to Permit.
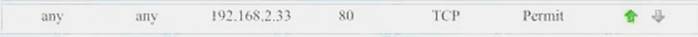
 Task 2) All web servers have been changed to communicate solely over SS
Task 2) All web servers have been changed to communicate solely over SS - F. Modify the appropriate rule to allow communications.The web servers rule is shown in the image belo
- G. Port 80 (HTTP) needs to be changed to port 443 for HTTPS (HTTP over SSL).
 Task 3) An administrator added a rule to block access to the SQL server from anywhere on the networ
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the networ - H. This rule is not workin
- I. Identify and correct this issue.The SQL Server rule is shown in the image belo
- J. It is not working because the protocol is wron
- K. It should be TCP, not UDP.
 Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.The network time rule is shown in the image below.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.The network time rule is shown in the image below. However, this rule is not being used because the ‘any’ rule shown below allows all traffic and the rule is placed above the network time rul
However, this rule is not being used because the ‘any’ rule shown below allows all traffic and the rule is placed above the network time rul - L. To block all other traffic, the ‘any’ rule needs to be set to Deny, not Permit and the rule needs to be placed below all the other rules (it needs to be placed atthe bottom of the list to the rule is enumerated last).

- M. Check the answer below
 Task 1) An administrator added a rule to allow their machine terminal server access to the server subne
Task 1) An administrator added a rule to allow their machine terminal server access to the server subne - N. This rule is not workin
- O. Identify the rule and correct this issue.The rule shown in the image below is the rule in questio
- P. It is not working because the action is set to Den
- Q. This needs to be set to Permit.
 Task 2) All web servers have been changed to communicate solely over SS
Task 2) All web servers have been changed to communicate solely over SS - R. Modify the appropriate rule to allow communications.The web servers rule is shown in the image belo
- S. Port 80 (HTTP) needs to be changed to port 443 for HTTPS (HTTP over SSL).Task 3) An administrator added a rule to block access to the SQL server from anywhere on the networ
- T. This rule is not workin
- . Identify and correct this issue.The SQL Server rule is shown in the image belo
- . It is not working because the protocol is wron
- . It should be TCP, not UDP.
 Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that noother traffic is allowed.The network time rule is shown in the image below.However, this rule is not being used because the ‘any’ rule shown below allows all traffic and the rule is placed above the network time rul
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that noother traffic is allowed.The network time rule is shown in the image below.However, this rule is not being used because the ‘any’ rule shown below allows all traffic and the rule is placed above the network time rul - . To block all other traffic, the ‘any’ rule needs to be set to Deny, not Permit and the rule needs to be placed below all the other rules (it needs to be placed atthe bottom of the list to the rule is enumerated last).

Answer: A
NEW QUESTION 11
The Chief Executive Officer (CEO) of a small startup company has an urgent need for a security policy and assessment to address governance, risk management, and compliance. The company has a resource-constrained IT department, but has no information security staff. The CEO has asked for this to be completed in three months.
Which of the following would be the MOST cost-effective solution to meet the company’s needs?
- A. Select one of the IT personnel to obtain information security training, and then develop all necessary policies and documents in-house.
- B. Accept all risks associated with information security, and then bring up the issue again at next year’s annual board meeting.
- C. Release an RFP to consultancy firms, and then select the most appropriate consultant who can fulfill the requirements.
- D. Hire an experienced, full-time information security team to run the startup company’s information security department.
Answer: C
NEW QUESTION 12
A company is facing penalties for failing to effectively comply with e-discovery requests. Which of the following could reduce the overall risk to the company from this issue?
- A. Establish a policy that only allows filesystem encryption and disallows the use of individual file encryption.
- B. Require each user to log passwords used for file encryption to a decentralized repository.
- C. Permit users to only encrypt individual files using their domain password and archive all old user passwords.
- D. Allow encryption only by tools that use public keys from the existing escrowed corporate PK
Answer: D
Explanation:
Electronic discovery (also called e-discovery) refers to any process in which electronic data is sought, located, secured, and searched with the intent of using it as evidence in a civil or criminal legal case. E-discovery can be carried out offline on a particular computer or it can be done in a network.
An e-discovery policy would define how data is archived and encrypted. If the data is archived in an insecure manor, a user could be able to delete data that the user does not want to be searched. Therefore, we need to find a way of securing the data in a way that only authorized people can access the data.
A public key infrastructure (PKI) supports the distribution and identification of public encryption keys for the encryption of dat
A. The data can only be decrypted by the private key.
In this question, we have an escrowed corporate PKI. Escrow is an independent and licensed third party that holds something (money, sensitive data etc.) and releases it only when predefined conditions have been met. In this case, Escrow is holding the private key of the PKI.
By encrypting the e-discovery data by using the PKI public key, we can ensure that the data can only be decrypted by the private key held in Escrow and this will only happen when the predefined conditions are met.
Incorrect Answers:
A: File encryption should be enabled to enable the archiving of the data.
B: Requiring each user to log passwords used for file encryption is not a good solution. Apart from there being no mechanism to enforce this, you should not need to know users’ passwords. You need a mechanism that ensures that the data can be decrypted by authorized personnel without the need to know user passwords.
C: You cannot and should not be able to archive old passwords. You need a mechanism that ensures that the data can be decrypted by authorized personnel without the need to know user passwords. References:
http://searchHYPERLINK "http://searchfinancialsecurity.techtarget.com/definition/electronicdiscovery" financialsecurity.techtarget.com/definitHYPERLINK "http://searchfinancialsecurity.techtarget.com/definition/electronic-discovery"ion/electronicdiscovery https://en.wikipedia.org/wiki/Escrow
NEW QUESTION 13
A security administrator is assessing a new application. The application uses an API that is supposed to encrypt text strings that are stored in memory. How might the administrator test that the strings are indeed encrypted in memory?
- A. Use fuzzing techniques to examine application inputs
- B. Run nmap to attach to application memory
- C. Use a packet analyzer to inspect the strings
- D. Initiate a core dump of the application
- E. Use an HTTP interceptor to capture the text strings
Answer: D
Explanation:
Applications store information in memory and this information include sensitive data, passwords, and usernames and encryption keys. Conducting memory/core dumping will allow you to analyze the memory content and then you can test that the strings are indeed encrypted.
Incorrect Answers:
A: Fuzzing is a type of black box testing that works by automatically feeding a program multiple input iterations that are specially constructed to trigger an internal error which would indicate that there is
a bug in the program and it could even crash your program that you are testing. B: Tools like NMAP is used mainly for scanning when running penetration tests.
C: Packet analyzers are used to troubleshoot network performance and not check that the strings in the memory are encrypted.
E: A HTTP interceptors are used to assess and analyze web traffic. References:
https://en.wikipedia.org/wHYPERLINK "https://en.wikipedia.org/wiki/Core_dump"iki/Core_dump
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 168-169, 174
NEW QUESTION 14
Given the following code snippet: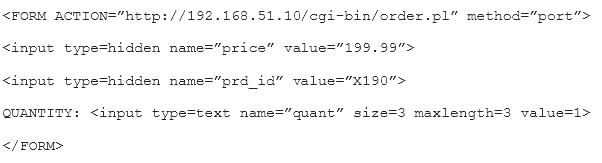
Of which of the following is this snippet an example?
- A. Data execution prevention
- B. Buffer overflow
- C. Failure to use standard libraries
- D. Improper filed usage
- E. Input validation
Answer: D
NEW QUESTION 15
A security analyst is reviewing the corporate MDM settings and notices some disabled settings, which consequently permit users to download programs from untrusted developers and manually install them. After some conversations, it is confirmed that these settings were disabled to support the internal development of mobile applications. The security analyst is now recommending that developers and testers have a separate device profile allowing this, and that the rest of the organization’s users do not have the ability to manually download and install untrusted applications. Which of the following settings should be toggled to achieve the goal? (Choose two.)
- A. OTA updates
- B. Remote wiping
- C. Side loading
- D. Sandboxing
- E. Containerization
- F. Signed applications
Answer: EF
NEW QUESTION 16
......
Thanks for reading the newest CAS-003 exam dumps! We recommend you to try the PREMIUM Dumps-hub.com CAS-003 dumps in VCE and PDF here: https://www.dumps-hub.com/CAS-003-dumps.html (555 Q&As Dumps)