CAS-003 | Improved CompTIA Advanced Security Practitioner (CASP) CAS-003 Free Practice Questions
It is more faster and easier to pass the CompTIA CAS-003 exam by using 100% Correct CompTIA CompTIA Advanced Security Practitioner (CASP) questuins and answers. Immediate access to the Up to the minute CAS-003 Exam and find the same core area CAS-003 questions with professionally verified answers, then PASS your exam with a high score now.
Online CompTIA CAS-003 free dumps demo Below:
NEW QUESTION 1
During a security event investigation, a junior analyst fails to create an image of a server’s hard drive before removing the drive and sending it to the forensics analyst. Later, the evidence from the analysis is not usable in the prosecution of the attackers due to the uncertainty of tampering. Which of the following should the junior analyst have followed?
- A. Continuity of operations
- B. Chain of custody
- C. Order of volatility
- D. Data recovery
Answer: C
NEW QUESTION 2
A managed service provider is designing a log aggregation service for customers who no longer want to manage an internal SIEM infrastructure. The provider expects that customers will send all types of logs to them, and that log files could contain very sensitive entries. Customers have indicated they want on-premises and cloud-based infrastructure logs to be stored in this new service. An engineer, who is designing the new service, is deciding how to segment customers. Which of the following is the BEST statement for the engineer to take into consideration?
- A. Single-tenancy is often more expensive and has less efficient resource utilizatio
- B. Multi-tenancy may increase the risk of cross-customer exposure in the event of service vulnerabilities.
- C. The managed service provider should outsource security of the platform to an existing cloud compan
- D. This will allow the new log service to be launched faster and with well-tested security controls.
- E. Due to the likelihood of large log volumes, the service provider should use a multi-tenancy model for the data storage tier, enable data deduplication for storage cost efficiencies, and encrypt data at rest.
- F. The most secure design approach would be to give customers on-premises appliances, install agents on endpoints, and then remotely manage the service via a VPN.
Answer: A
NEW QUESTION 3
A small company’s Chief Executive Officer (CEO) has asked its Chief Security Officer (CSO) to improve the company’s security posture quickly with regard to targeted attacks. Which of the following
should the CSO conduct FIRST?
- A. Survey threat feeds from services inside the same industry.
- B. Purchase multiple threat feeds to ensure diversity and implement blocks for malicious traffic.
- C. Conduct an internal audit against industry best practices to perform a qualitative analysis.
- D. Deploy a UTM solution that receives frequent updates from a trusted industry vendo
Answer: A
Explanation:
Security posture refers to the overall security plan from planning through to implementation and comprises technical and non-technical policies, procedures and controls to protect from both internal and external threats. From a security standpoint, one of the first questions that must be answered in improving the overall security posture of an organization is to identify where data
resides. All the advances that were made by technology make this very difficult. The best way then to improve your company’s security posture is to first survey threat feeds from services inside the same industry.
Incorrect Answers:
B: Purchasing multiple threat feeds will provide better security posture, but the first step is still to survey threats from services within the same industry.
C: Conducting an internal audit is not the first step in improving security posture of your company. D: Deploying a UTM solution to get frequent updates is not the first step to take when tasked with the job of improving security posture.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 99
NEW QUESTION 4
A security analyst is attempting to break into a client’s secure network. The analyst was not given prior information about the client, except for a block of public IP addresses that are currently in use. After network enumeration, the analyst’s NEXT step is to perform:
- A. a gray-box penetration test
- B. a risk analysis
- C. a vulnerability assessment
- D. an external security audit
- E. a red team exercise
Answer: A
NEW QUESTION 5
The DLP solution has been showing some unidentified encrypted data being sent using FTP to a remote server. A vulnerability scan found a collection of Linux servers that are missing OS level patches. Upon further investigation, a technician notices that there are a few unidentified processes running on a number of the servers. What would be a key FIRST step for the data security team to undertake at this point?
- A. Capture process ID data and submit to anti-virus vendor for review.
- B. Reboot the Linux servers, check running processes, and install needed patches.
- C. Remove a single Linux server from production and place in quarantine.
- D. Notify upper management of a security breach.
- E. Conduct a bit level image, including RAM, of one or more of the Linux server
Answer: E
Explanation:
Incident management (IM) is a necessary part of a security program. When effective, it mitigates business impact, identifies weaknesses in controls, and helps fine-tune response processes.
In this question, an attack has been identified and confirmed. When a server is compromised or used to commit a crime, it is often necessary to seize it for forensics analysis. Security teams often face two challenges when trying to remove a physical server from service: retention of potential evidence in volatile storage or removal of a device from a critical business process.
Evidence retention is a problem when the investigator wants to retain RAM content. For example, removing power from a server starts the process of mitigating business impact, but it also denies forensic analysis of data, processes, keys, and possible footprints left by an attacker.
A full a bit level image, including RAM should be taken of one or more of the Linux servers. In many cases, if your environment has been deliberately attacked, you may want to take legal action against the perpetrators. In order to preserve this option, you should gather evidence that can be used
against them, even if a decision is ultimately made not to pursue such action. It is extremely important to back up the compromised systems as soon as possible. Back up the systems prior to performing any actions that could affect data integrity on the original media.
Incorrect Answers:
A: Capturing process ID data and submitting it to anti-virus vendor for review would not be the first step. Furthermore, it is unlikely that a virus is the cause of the problem on the LINUX servers. It is much more likely that the missing OS level patches left the systems vulnerable.
B: Rebooting the Linux servers would lose the contents of the running RAM. This may be needed for litigation so a full backup including RAM should be taken first. Then the servers can be cleaned and patched.
C: Removing a single Linux server from production and placing it in quarantine would probably involve powering off the server. Powering off the server would lose the contents of the running RAM. This may be needed for litigation so a full backup including RAM should be taken first.
D: Notifying upper management of a security breach probably should be done after the security breach is contained. You should follow standard incident management procedures first. Reporting on the incident is one of the later steps in the process.
References:
http://whatis.techtarget.com/reference/FiHYPERLINK "http://whatis.techtarget.com/reference/Five- Steps-to-Incident-Management-in-a-Virtualized-Environment"ve-Steps-to-Incident-Management-ina-
Virtualized-Environment
https://technet.miHYPERLINK "https://technet.microsoft.com/enhttps:// certkingdom.com
us/library/cc700825.aspx"crosoft.com/en-us/library/cc700825.aspx
NEW QUESTION 6
Which of the following system would be at the GREATEST risk of compromise if found to have an open vulnerability associated with perfect ... secrecy?
- A. Endpoints
- B. VPN concentrators
- C. Virtual hosts
- D. SIEM
- E. Layer 2 switches
Answer: B
NEW QUESTION 7
Wireless users are reporting issues with the company’s video conferencing and VoIP systems. The security administrator notices internal DoS attacks from infected PCs on the network causing the VoIP system to drop calls. The security administrator also notices that the SIP servers are unavailable
during these attacks. Which of the following security controls will MOST likely mitigate the VoIP DoS attacks on the network? (Select TWO).
- A. Install a HIPS on the SIP servers
- B. Configure 802.1X on the network
- C. Update the corporate firewall to block attacking addresses
- D. Configure 802.11e on the network
- E. Configure 802.1q on the network
Answer: AD
Explanation:
Host-based intrusion prevention system (HIPS) is an installed software package that will monitor a single host for suspicious activity by analyzing events taking place within that host.
IEEE 802.11e is deemed to be of significant consequence for delay-sensitive applications, such as Voice over Wireless LAN and streaming multimedia.
Incorrect Answers:
B: 802.1X is used by devices to attach to a LAN or WLAN.
C: Updating the corporate firewall will not work as the DoS attacks are from an internal source. E: 802.1q is used for VLAN tagging.
References: https:HYPERLINK
"https://en.wikipedia.org/wiki/Intrusion_prevention_system"//en.wikipedia.org/wiki/Intrusion_pre vention_system
https://en.wikipedia.orHYPERLINK "https://en.wikipedia.org/wiki/IEEE_802.11e- 2005"g/wiki/IEEE_802.11e-2005
https://en.wikipedia.org/wiki/IEEE_802.1X https://en.wikipedia.org/wiki/IEEE_802.1Q
NEW QUESTION 8
A security auditor suspects two employees of having devised a scheme to steal money from the company. While one employee submits purchase orders for personal items, the other employee approves these purchase orders. The auditor has contacted the human resources director with suggestions on how to detect such illegal activities. Which of the following should the human resource director implement to identify the employees involved in these activities and reduce the risk of this activity occurring in the future?
- A. Background checks
- B. Job rotation
- C. Least privilege
- D. Employee termination procedures
Answer: B
Explanation:
Job rotation can reduce fraud or misuse by preventing an individual from having too much control over an area.
Incorrect Answers:
A: To verify that a potential employee has a clean background and that any negative history is exposed prior to employment, a background check is used.
C: The principle of least privilege prevents employees from accessing levels not required to perform their everyday function.
D: The employee termination procedures will not identify the employees involved in these activities and reduce the risk of this activity occurring in the future.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 243, 245, 246
NEW QUESTION 9
After embracing a BYOD policy, a company is faced with new security challenges from unmanaged mobile devices and laptops. The company’s IT department has seen a large number of the following incidents:
Duplicate IP addresses Rogue network devices
Infected systems probing the company’s network
Which of the following should be implemented to remediate the above issues? (Choose two.)
- A. Port security
- B. Route protection
- C. NAC
- D. HIPS
- E. NIDS
Answer: BC
NEW QUESTION 10
Due to compliance regulations, a company requires a yearly penetration test. The Chief Information Security Officer (CISO) has asked that it be done under a black box methodology.
Which of the following would be the advantage of conducting this kind of penetration test?
- A. The risk of unplanned server outages is reduced.
- B. Using documentation provided to them, the pen-test organization can quickly determine areas to focus on.
- C. The results will show an in-depth view of the network and should help pin-point areas of internal weakness.
- D. The results should refilect what attackers may be able to learn about the compan
Answer: D
Explanation:
A black box penetration test is usually done when you do not have access to the code, much the same like an outsider/attacker. This is then the best way to run a penetration test that will also refilect what an attacker/outsider can learn about the company. A black box test simulates an outsiders attack.
Incorrect Answers:
A: Unplanned server outages are not the advantage of running black box penetration testing.
B: Making use of documentation is actually avoided since black box testing simulates the attack as done by an outsider.
C: An in-depth view of the company’s network and internal weak points is not an advantage of black box penetration tests.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 168
NEW QUESTION 11
A newly hired systems administrator is trying to connect a new and fully updated, but very customized, Android device to access corporate resources. However, the MDM enrollment process continually fails. The administrator asks a security team member to look into the issue. Which of the following is the MOST likely reason the MDM is not allowing enrollment?
- A. The OS version is not compatible
- B. The OEM is prohibited
- C. The device does not support FDE
- D. The device is rooted
Answer: D
NEW QUESTION 12
Given the following output from a local PC: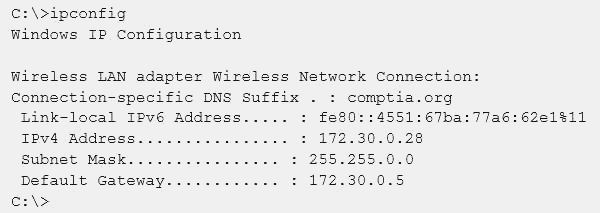
Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
- A. Allow 172.30.0.28:80 -> ANY
- B. Allow 172.30.0.28:80 -> 172.30.0.0/16
- C. Allow 172.30.0.28:80 -> 172.30.0.28:443
- D. Allow 172.30.0.28:80 -> 172.30.0.28:53
Answer: B
NEW QUESTION 13
A security engineer on a large enterprise network needs to schedule maintenance within a fixed window of time. A total outage period of four hours is permitted for servers. Workstations can undergo maintenance from 8:00 pm to 6:00 am daily. Which of the following can specify parameters for the maintenance work? (Select TWO).
- A. Managed security service
- B. Memorandum of understanding
- C. Quality of service
- D. Network service provider
- E. Operating level agreement
Answer: BE
Explanation:
B: A memorandum of understanding (MOU) documents conditions and applied terms for outsourcing partner organizations that must share data and information resources. It must be signed by a re presentative from each organization that has the legal authority to sign and are typically secured, as they are considered confidential.
E: An operating level agreement (O LA) defines the responsibilities of each partner's internal support group and what group and resources are used to meet the specified goal. It is used in conjunction with service level agreements (SLAs).
Incorrect Answers:
A: A managed security service (MSS) is a network security service that has been outsourced to a service provider, such as an Internet Service Provider (ISP). In the earlier days of the Internet, ISPs would sell customers a firewall appliance, as customer premises equipment (CPE), and for an additional fee would manage the customer-owned firewall over a dial-up connection.
C: Quality of service (QoS) is a mechanism that is designed to give priority to different applications, users, or data to provide a specific level of performance. It is often used in networks to prioritize certain types of network traffic.
D: A network service provider (NSP) provides bandwidth or network access via direct Internet backbone access to the Internet and usually access to its network access points (NAPs). They are sometimes referred to as backbone providers or internet providers.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 237, 362
httHYPERLINK "https://en.wikipedia.org/wiki/Managed_security_service"ps://en.wikipedHYPERLINK "https://en.wikipedia.org/wiki/Managed_security_service"ia.org/wiki/Managed_secuHYPERLINK "https://en.wikipedia.org/wiki/Managed_security_service"rity_service
https://en.wikipeHYPERLINK "https://en.wikipedia.org/wiki/Network_service_provider"dia.org/wiki/Network_service_provider
NEW QUESTION 14
A consultant is hired to perform a passive vulnerability assessment of a company to determine what information might be collected about the company and its employees. The assessment will be considered successful if the consultant can discover the name of one of the IT administrators. Which of the following is MOST likely to produce the needed information?
- A. Whois
- B. DNS enumeration
- C. Vulnerability scanner
- D. Fingerprinting
Answer: A
NEW QUESTION 15
A consulting firm was hired to conduct assessment for a company. During the first stage, a penetration tester used a tool that provided the following output:
TCP 80 open
TCP 443 open
TCP 1434 filtered
The penetration tester then used a different tool to make the following requests:
GET / script/login.php?token=45$MHT000MND876
GET / script/login.php?token=@#984DCSPQ%091DF
Which of the following tools did the penetration tester use?
- A. Protocol analyzer
- B. Port scanner
- C. Fuzzer
- D. Brute forcer
- E. Log analyzer
- F. HTTP interceptor
Answer: C
NEW QUESTION 16
......
P.S. Dumps-files.com now are offering 100% pass ensure CAS-003 dumps! All CAS-003 exam questions have been updated with correct answers: https://www.dumps-files.com/files/CAS-003/ (555 New Questions)