CAS-003 | The Most Up-to-date Guide To CAS-003 Exam Topics
Cause all that matters here is passing the CompTIA CAS-003 exam. Cause all that you need is a high score of CAS-003 CompTIA Advanced Security Practitioner (CASP) exam. The only one thing you need to do is downloading Passleader CAS-003 exam study guides now. We will not let you down with our money-back guarantee.
Check CAS-003 free dumps before getting the full version:
NEW QUESTION 1
A company is developing requirements for a customized OS build that will be used in an embedded environment. The company procured hardware that is capable of reducing the likelihood of successful buffer overruns while executables are processing. Which of the following capabilities must be included for the OS to take advantage of this critical hardware-based countermeasure?
- A. Application whitelisting
- B. NX/XN bit
- C. ASLR
- D. TrustZone
- E. SCP
Answer: B
NEW QUESTION 2
A threat advisory alert was just emailed to the IT security staff. The alert references specific types of host operating systems that can allow an unauthorized person to access files on a system remotely. A fix was recently published, but it requires a recent endpoint protection engine to be installed prior to running the fix.
Which of the following MOST likely need to be configured to ensure the system are mitigated accordingly? (Select two.)
- A. Antivirus
- B. HIPS
- C. Application whitelisting
- D. Patch management
- E. Group policy implementation
- F. Firmware updates
Answer: DF
NEW QUESTION 3
The latest independent research shows that cyber attacks involving SCADA systems grew an average of 15% per year in each of the last four years, but that this year’s growth has slowed to around 7%. Over the same time period, the number of attacks against applications has decreased or stayed flat each year. At the start of the measure period, the incidence of PC boot loader or BIOS based attacks was negligible. Starting two years ago, the growth in the number of PC boot loader attacks has grown exponentially. Analysis of these trends would seem to suggest which of the following strategies should be employed?
- A. Spending on SCADA protections should stay steady; application control spending should increase substantially and spending on PC boot loader controls should increase substantially.
- B. Spending on SCADA security controls should stay steady; application control spending should decrease slightly and spending on PC boot loader protections should increase substantially.
- C. Spending all controls should increase by 15% to start; spending on application controls should be suspended, and PC boot loader protection research should increase by 100%.
- D. Spending on SCADA security controls should increase by 15%; application control spending should increase slightly, and spending on PC boot loader protections should remain steady.
Answer: B
Explanation:
Spending on the security controls should stay steady because the attacks are still ongoing albeit reduced in occurrence Due to the incidence of BIOS-based attacks growing exponentially as the application attacks being decreased or staying flat spending should increase in this field. Incorrect Answers:
A: The SCADA security control spending and not the SCADA protection spending should stay steady. There is no need to in spending on application control.
C: There is no n increase spending on all security controls.
D: This is partly correct, but the spending on application control does not have to increase and the BIOS protections should increase since these attacks are now more prevalent.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 343
https://en.wikipedia.org/wiki/SCADA
NEW QUESTION 4
After a large organization has completed the acquisition of a smaller company, the smaller company must implement new host-based security controls to connect its employees’ devices to the network. Given that the network requires 802.1X EAP-PEAP to identify and authenticate devices, which of the following should the security administrator do to integrate the new employees’ devices into the network securely?
- A. Distribute a NAC client and use the client to push the company’s private key to all the new devices.
- B. Distribute the device connection policy and a unique public/private key pair to each new employee’s device.
- C. Install a self-signed SSL certificate on the company’s RADIUS server and distribute the certificate’s public key to all new client devices.
- D. Install an 802.1X supplicant on all new devices and let each device generate a self-signed certificate to use for network access.
Answer: D
NEW QUESTION 5
A security administrator wants to allow external organizations to cryptographically validate the company’s domain name in email messages sent by employees. Which of the following should the security administrator implement?
- A. SPF
- B. S/MIME
- C. TLS
- D. DKIM
Answer: D
NEW QUESTION 6
A network engineer is upgrading the network perimeter and installing a new firewall, IDS, and external edge router. The IDS is reporting elevated UDP traffic, and the internal routers are reporting high utilization. Which of the following is the BEST solution?
- A. Reconfigure the firewall to block external UDP traffic.
- B. Establish a security baseline on the IDS.
- C. Block echo reply traffic at the firewall.
- D. Modify the edge router to not forward broadcast traffi
Answer: B
NEW QUESTION 7
To prepare for an upcoming audit, the Chief Information Security Officer (CISO) asks for all 1200 vulnerabilities on production servers to be remediated. The security engineer must determine which vulnerabilities represent real threats that can be explogted so resources can be prioritized to migrate the most dangerous risks. The CISO wants the security engineer to act in the same manner as would an external threat, while using vulnerability scan results to prioritize any actions. Which of the following approaches is described?
- A. Blue team
- B. Red team
- C. Black box
- D. White team
Answer: C
NEW QUESTION 8
During a security assessment, activities were divided into two phases; internal and external explogtation. The security assessment team set a hard time limit on external activities before moving to a compromised box within the enterprise perimeter.
Which of the following methods is the assessment team most likely to employ NEXT?
- A. Pivoting from the compromised, moving laterally through the enterprise, and trying to exfiltrate data and compromise devices.
- B. Conducting a social engineering attack attempt with the goal of accessing the compromised box physically.
- C. Exfiltrating network scans from the compromised box as a precursor to social media reconnaissance
- D. Open-source intelligence gathering to identify the network perimeter and scope to enable further system compromises.
Answer: A
NEW QUESTION 9
Given the code snippet below: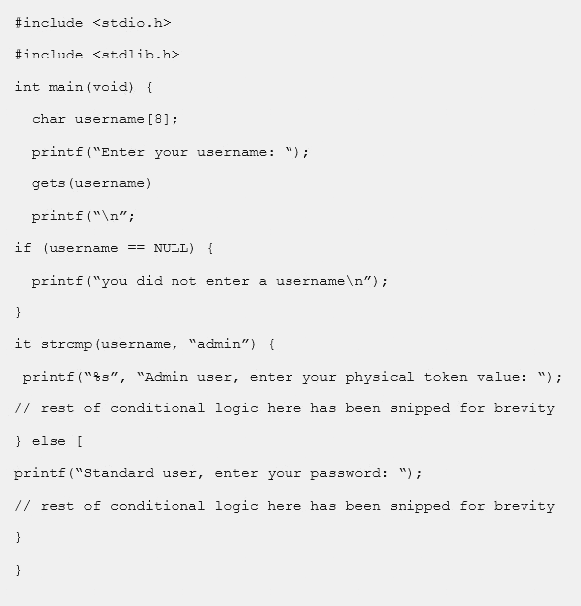
Which of the following vulnerability types in the MOST concerning?
- A. Only short usernames are supported, which could result in brute forcing of credentials.
- B. Buffer overflow in the username parameter could lead to a memory corruption vulnerability.
- C. Hardcoded usernames with different code paths taken depend on which user is entered.
- D. Format string vulnerability is present for admin users but not for standard user
Answer: B
NEW QUESTION 10
An administrator wants to install a patch to an application. INSTRUCTIONS
Given the scenario, download, verify, and install the patch in the most secure manner. The last install that is completed will be the final submission.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
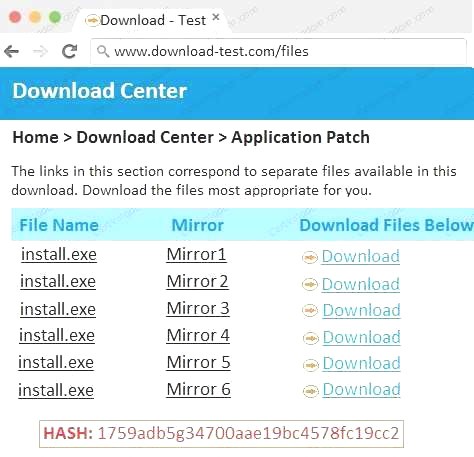
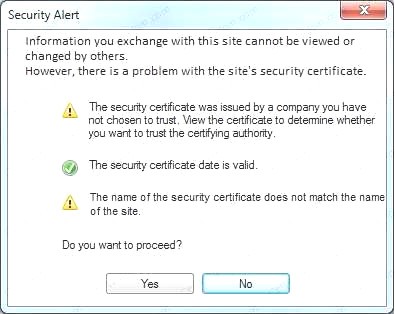
- A. In this case the second link should be used (This may vary in actual exam). The first link showed the following error so it should not be used.
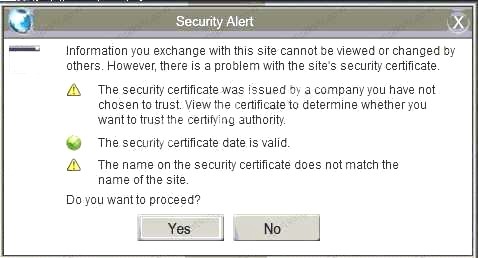 Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown:
Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown: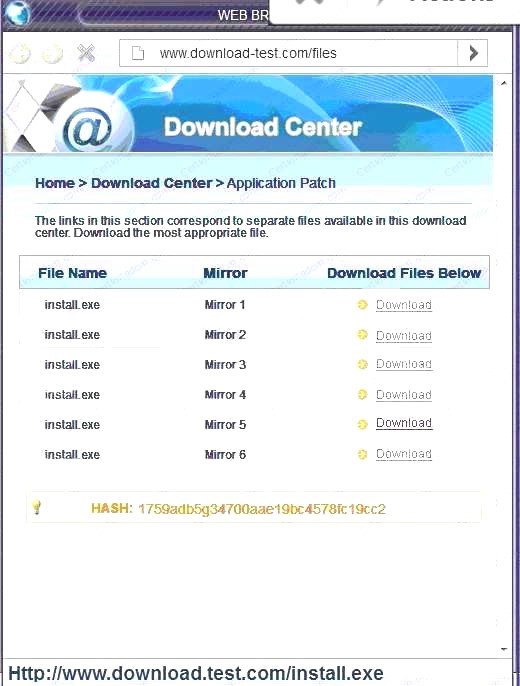 Since we need to do this in the most secure manner possible, they should not be used.Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as show
Since we need to do this in the most secure manner possible, they should not be used.Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as show - B. Make sure that the hash matches.
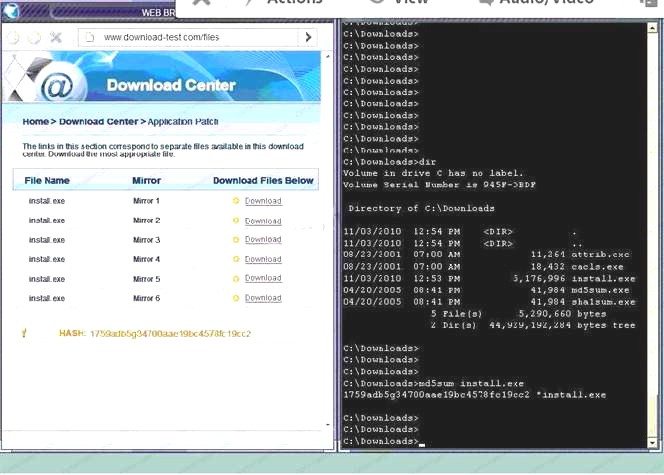 Finally, type in install.exe to install it and make sure there are no signature verification errors.
Finally, type in install.exe to install it and make sure there are no signature verification errors. - C. In this case the second link should be used (This may vary in actual exam). The first link showed the following error so it should not be used.
 Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown.Since we need to do this in the most secure manner possible, they should not be used.Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as show
Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown.Since we need to do this in the most secure manner possible, they should not be used.Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as show - D. Make sure that the hash matches.Finally, type in install.exe to install it and make sure there are no signature verification error
Answer: A
NEW QUESTION 11
A forensics analyst suspects that a breach has occurred. Security logs show the company’s OS patch system may be compromised, and it is serving patches that contain a zero-day explogt and backdoor. The analyst extracts an executable file from a packet capture of communication between a client computer and the patch server. Which of the following should the analyst use to confirm this suspicion?
- A. File size
- B. Digital signature
- C. Checksums
- D. Anti-malware software
- E. Sandboxing
Answer: B
NEW QUESTION 12
An attacker attempts to create a DoS event against the VoIP system of a company. The attacker uses a tool to flood the network with a large number of SIP INVITE traffic. Which of the following would be LEAST likely to thwart such an attack?
- A. Install IDS/IPS systems on the network
- B. Force all SIP communication to be encrypted
- C. Create separate VLANs for voice and data traffic
- D. Implement QoS parameters on the switches
Answer: D
Explanation:
Quality of service (QoS) is a mechanism that is designed to give priority to different applications, users, or data to provide a specific level of performance. It is often used in networks to prioritize certain types of network traffic. It is not designed to block traffic, per se, but to give certain types of traffic a lower or higher priority than others. This is least likely to counter a denial of service (DoS) attack.
Incorrect Answers:
A: Denial of Service (DoS) attacks web-based attacks that explogt flaws in the operating system, applications, services, or protocols. These attacks can be mitigated by means of firewalls, routers,
and intrusion detection systems (IDSs) that detect DoS traffic, disabling echo replies on external systems, disabling broadcast features on border systems, blocking spoofed packets on the network, and proper patch management.
B: VoIP makes use of Session Initiation Protocol (SIP) and the attack is making use of SIP INVITE requests to initiate VoIP calls. Forcing SIP communication to be encrypted would reduce SIP INVITE requests.
C: Using virtual local area networks (VLANs), to segregate data traffic from voice traffic can drastically reduce the potential for attacks that utilize automated tools.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 135-138, 355-356, 357, 362, 378
NEW QUESTION 13
A forensic analyst suspects that a buffer overflow exists in a kernel module. The analyst executes the following command:
dd if=/dev/ram of=/tmp/mem/dmp
The analyst then reviews the associated output:
^34^#AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/bin/bash^21^03#45
However, the analyst is unable to find any evidence of the running shell. Which of the following of the MOST likely reason the analyst cannot find a process ID for the shell?
- A. The NX bit is enabled
- B. The system uses ASLR
- C. The shell is obfuscated
- D. The code uses dynamic libraries
Answer: B
NEW QUESTION 14
A medical device company is implementing a new COTS antivirus solution in its manufacturing plant.
All validated machines and instruments must be retested for interoperability with the new software. Which of the following would BEST ensure the software and instruments are working as designed?
- A. System design documentation
- B. User acceptance testing
- C. Peer review
- D. Static code analysis testing
- E. Change control documentation
Answer: A
NEW QUESTION 15
Company policy requires that all company laptops meet the following baseline requirements: Software requirements:
Antivirus
Anti-malware Anti-spyware Log monitoring
Full-disk encryption
Terminal services enabled for RDP Administrative access for local users Hardware restrictions:
Bluetooth disabled FireWire disabled WiFi adapter disabled
Ann, a web developer, reports performance issues with her laptop and is not able to access any network resources. After further investigation, a bootkit was discovered and it was trying to access external websites. Which of the following hardening techniques should be applied to mitigate this specific issue from reoccurring? (Select TWO).
- A. Group policy to limit web access
- B. Restrict VPN access for all mobile users
- C. Remove full-disk encryption
- D. Remove administrative access to local users
- E. Restrict/disable TELNET access to network resources
- F. Perform vulnerability scanning on a daily basis
- G. Restrict/disable USB access
Answer: DG
Explanation:
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or areas of its software that would not otherwise be allowed (for example, to an unauthorized user) while at the same time masking its existence or the existence of other software. A bootkit is similar to a rootkit except the malware infects the master boot record on a hard disk. Malicious software such as bootkits or rootkits typically require administrative privileges to be installed.
Therefore, one method of preventing such attacks is to remove administrative access for local users. A common source of malware infections is portable USB flash drives. The flash drives are often plugged into less secure computers such as a user’s home computer and then taken to work and plugged in to a work computer. We can prevent this from happening by restricting or disabling access to USB devices.
Incorrect Answers:
A: Using a group policy to limit web access is not a practical solution. Users in a company often require Web access so restricting it will affect their ability to do their jobs.
B: Rootkits or Bootkits would not be caught by connecting to the network over a VPN so disabling VPN access will not help.
C: Removing full-disk encryption will not prevent Bootkits.
E: Bootkits are not caught by connecting to network resources using Telnet connection so disabling Telnet access to resources will not help.
F: Performing vulnerability scanning on a daily basis might help you to quickly detect Bootkits. However, vulnerability scanning does nothing to actually prevent the Bootkits.
References: https://en.wikipedia.org/wiki/Rootkit
NEW QUESTION 16
......
P.S. Certshared now are offering 100% pass ensure CAS-003 dumps! All CAS-003 exam questions have been updated with correct answers: https://www.certshared.com/exam/CAS-003/ (555 New Questions)