CAS-003 | The Secret Of CompTIA CAS-003 Exams
Examcollection CAS-003 Questions are updated and all CAS-003 answers are verified by experts. Once you have completely prepared with our CAS-003 exam prep kits you will be ready for the real CAS-003 exam without a problem. We have Far out CompTIA CAS-003 dumps study guide. PASSED CAS-003 First attempt! Here What I Did.
Check CAS-003 free dumps before getting the full version:
NEW QUESTION 1
Two new technical SMB security settings have been enforced and have also become policies that increase secure communications.
Network Client: Digitally sign communication Network Server: Digitally sign communication
A storage administrator in a remote location with a legacy storage array, which contains timesensitive data, reports employees can no longer connect to their department shares. Which of the following mitigation strategies should an information security manager recommend to the data owner?
- A. Accept the risk, reverse the settings for the remote location, and have the remote location file a risk exception until the legacy storage device can be upgraded
- B. Accept the risk for the remote location, and reverse the settings indefinitely since the legacy storage device will not be upgraded
- C. Mitigate the risk for the remote location by suggesting a move to a cloud service provide
- D. Have the remote location request an indefinite risk exception for the use of cloud storage
- E. Avoid the risk, leave the settings alone, and decommission the legacy storage device
Answer: A
NEW QUESTION 2
A company has created a policy to allow employees to use their personally owned devices. The Chief Information Officer (CISO) is getting reports of company data appearing on unapproved forums and an increase in theft of personal electronic devices. Which of the following security controls would BEST reduce the risk of exposure?
- A. Disk encryption on the local drive
- B. Group policy to enforce failed login lockout
- C. Multifactor authentication
- D. Implementation of email digital signatures
Answer: A
NEW QUESTION 3
A multi-national company has a highly mobile workforce and minimal IT infrastructure. The company utilizes a BYOD and social media policy to integrate presence technology into global collaboration tools by individuals and teams. As a result of the dispersed employees and frequent international travel, the company is concerned about the safety of employees and their families when moving in and out of certain countries. Which of the following could the company view as a downside of using presence technology?
- A. Insider threat
- B. Network reconnaissance
- C. Physical security
- D. Industrial espionage
Answer: C
Explanation:
If all company users worked in the same office with one corporate network and using company supplied laptops, then it is easy to implement all sorts of physical security controls. Examples of physical security include intrusion detection systems, fire protection systems, surveillance cameras or simply a lock on the office door.
However, in this question we have dispersed employees using their own devices and frequently traveling internationally. This makes it extremely difficult to implement any kind of physical security. Physical security is the protection of personnel, hardware, programs, networks, and data from physical circumstances and events that could cause serious losses or damage to an enterprise,
agency, or institution. This includes protection from fire, natural disasters, burglary, theft, vandalism, and terrorism.
Incorrect Answers:
A: An insider threat is a malicious hacker (also called a cracker or a black hat) who is an employee or officer of a business, institution, or agency. Dispersed employees using presence technology does not increase the risk of insider threat when compared to employees working together in an office.
B: The risk of network reconnaissance is reduced by having dispersed employees using presence technology. The risk of network reconnaissance would be higher with employees working together in a single location such as an office.
D: Industrial espionage is a threat to any business whose livelihood depends on information. However, this threat is not increased by having dispersed employees using presence technology. The risk would be the same with dispersed employees using presence technology or employees working together in a single location such as an office.
References: http://searchsecurity.techtarget.com/deHYPERLINK
"http://searchsecurity.techtarget.com/definition/physical-security"finition/physical-security
NEW QUESTION 4
An internal staff member logs into an ERP platform and clicks on a record. The browser URL changes to:
URL: http://192.168.0.100/ERP/accountId=5&action=SELECT
Which of the following is the MOST likely vulnerability in this ERP platform?
- A. Brute forcing of account credentials
- B. Plan-text credentials transmitted over the Internet
- C. Insecure direct object reference
- D. SQL injection of ERP back end
Answer: C
NEW QUESTION 5
A well-known retailer has experienced a massive credit card breach. The retailer had gone through an audit and had been presented with a potential problem on their network. Vendors were authenticating directly to the retailer’s AD servers, and an improper firewall rule allowed pivoting from the AD server to the DMZ where credit card servers were kept. The firewall rule was needed for an internal application that was developed, which presents risk. The retailer determined that
because the vendors were required to have site to site VPN’s no other security action was taken.
To prove to the retailer the monetary value of this risk, which of the following type of calculations is needed?
- A. Residual Risk calculation
- B. A cost/benefit analysis
- C. Quantitative Risk Analysis
- D. Qualitative Risk Analysis
Answer: C
Explanation:
Performing quantitative risk analysis focuses on assessing the probability of risk with a metric measurement which is usually a numerical value based on money or time.
Incorrect Answers:
A: A residual risk is one that still remains once the risk responses are applied. Thus a Residual risk calculation is not required.
B: Cost Benefit Analysis is used for Quality Planning. This is not what is required.
D: A qualitative risk analysis entails a subjective assessment of the probability of risks. The scenario warrants a quantitative risk.
References:
Project Management Institute, A Guide to the Project Management Body of Knowledge (PMBOK Guide), 5th Edition, Project Management Institute, Inc., Newtown Square, 2013, pp. 373, 585, 589 Schwalbe, Kathy, Managing Information Technology Projects, Revised 6th Edition, Course Technology, Andover, 2011, pp. 421-447
Whitaker, Sean, PMP Training Kit, O’Reilly Media, Sebastopol, 2013, pp. 335-375
NEW QUESTION 6
After a security incident, an administrator would like to implement policies that would help reduce fraud and the potential for collusion between employees. Which of the following would help meet these goals by having co-workers occasionally audit another worker's position?
- A. Least privilege
- B. Job rotation
- C. Mandatory vacation
- D. Separation of duties
Answer: B
Explanation:
Job rotation can reduce fraud or misuse by preventing an individual from having too much control over an area.
Incorrect Answers:
A: The principle of least privilege prevents employees from accessing levels not required to perform their everyday function.
C: Mandatory vacation is used to discover misuse and allow the organization time to audit a suspected employee while they are away from work.
D: Separation of duties requires more than one person to complete a task. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 245
NEW QUESTION 7
A popular commercial virtualization platform allows for the creation of virtual hardware. To virtual machines, this virtual hardware is indistinguishable from real hardware. By implementing virtualized TPMs, which of the following trusted system concepts can be implemented?
- A. Software-based root of trust
- B. Continuous chain of trust
- C. Chain of trust with a hardware root of trust
- D. Software-based trust anchor with no root of trust
Answer: C
Explanation:
A Trusted Platform Module (TPM) is a microchip designed to provide basic security-related functions, primarily involving encryption keys. The TPM is usually installed on the motherboard of a computer, and it communicates with the remainder of the system by using a hardware bus.
A vTPM is a virtual Trusted Platform Module; a virtual instance of the TPM.
IBM extended the current TPM V1.2 command set with virtual TPM management commands that allow us to create and delete instances of TPMs. Each created instance of a TPM holds an association with a virtual machine (VM) throughout its lifetime on the platform.
The TPM is the hardware root of trust.
Chain of trust means to extend the trust boundary from the root(s) of trust, in order to extend the collection of trustworthy functions. Implies/entails transitive trust.
Therefore a virtual TPM is a chain of trust from the hardware TPM (root of trust). Incorrect Answers:
A: A vTPM is a virtual instance of the hardware TPM. Therefore, the root of trust is a hardware root of trust, not a software-based root of trust.
B: The chain of trust needs a root. In this case, the TPM is a hardware root of trust. This answer has no root of trust.
D: There needs to be a root of trust. In this case, the TPM is a hardware root of trust. This answer has no root of trust.
References: https://www.cylab.cmu.edu/tiw/slides/martin-tiw101.pdf
NEW QUESTION 8
A security analyst is reviewing logs and discovers that a company-owned computer issued to an employee is generating many alerts and analyst continues to review the log events and discovers that a non-company-owned device from a different, unknown IP address is general same events. The analyst informs the manager of these finding, and the manager explains that these activities are already known and . . . ongoing simulation. Given this scenario, which of the following roles are the analyst, the employee, and the manager fillings?
- A. The analyst is red team The employee is blue team The manager is white team
- B. The analyst is white team The employee is red team The manager is blue team
- C. The analyst is red team The employee is white team The manager is blue team
- D. The analyst is blue team The employee is red team The manager is white team
Answer: D
NEW QUESTION 9
A Chief Information Security Officer (CISO) has requested that a SIEM solution be implemented. The CISO wants to know upfront what the projected TCO would be before looking further into this concern. Two vendor proposals have been received:
Vendor A: product-based solution which can be purchased by the pharmaceutical company.
Capital expenses to cover central log collectors, correlators, storage and management consoles expected to be $150,000. Operational expenses are expected to be a 0.5 full time employee (FTE) to manage the solution, and 1 full time employee to respond to incidents per year.
Vendor B: managed service-based solution which can be the outsourcer for the pharmaceutical company’s needs.
Bundled offering expected to be $100,000 per year.
Operational expenses for the pharmaceutical company to partner with the vendor are expected to be a 0.5 FTE per year.
Internal employee costs are averaged to be $80,000 per year per FTE. Based on calculating TCO of the two vendor proposals over a 5 year period, which of the following options is MOST accurate?
- A. Based on cost alone, having an outsourced solution appears cheaper.
- B. Based on cost alone, having an outsourced solution appears to be more expensive.
- C. Based on cost alone, both outsourced an in-sourced solutions appear to be the same.
- D. Based on cost alone, having a purchased product solution appears cheape
Answer: A
Explanation:
The costs of making use of an outsources solution will actually be a savings for the company thus the outsourced solution is a cheaper option over a 5 year period because it amounts to 0,5 FTE per year for the company and at present the company expense if $80,000 per year per FTE.
For the company to go alone it will cost $80,000 per annum per FTE = $400,000 over 5 years. With Vendor a $150,000 + $200,000 (½ FTE) = $350,000
With Vendor B = $100,000 it will be more expensive. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 130
NEW QUESTION 10
Legal authorities notify a company that its network has been compromised for the second time in two years. The investigation shows the attackers were able to use the same vulnerability on different systems in both attacks. Which of the following would have allowed the security team to use historical information to protect against the second attack?
- A. Key risk indicators
- B. Lessons learned
- C. Recovery point objectives
- D. Tabletop exercise
Answer: A
NEW QUESTION 11
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website.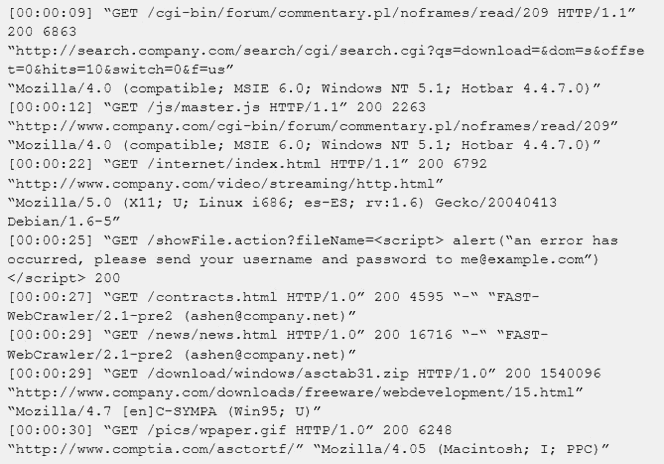
Which of the following types of attack vector did the penetration tester use?
- A. SQLi
- B. CSRF
- C. Brute force
- D. XSS
- E. TOC/TOU
Answer: B
NEW QUESTION 12
The government is concerned with remote military missions being negatively being impacted by the use of technology that may fail to protect operational security. To remediate this concern, a number of solutions have been implemented, including the following:
End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow soldiers to securely communicate with families.
Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications
A host-based whitelist of approved websites and applications that only allow mission-related tools and sites
The use of satellite communication to include multiple proxy servers to scramble the source IP address
Which of the following is of MOST concern in this scenario?
- A. Malicious actors intercepting inbound and outbound communication to determine the scope of the mission
- B. Family members posting geotagged images on social media that were received via email from soldiers
- C. The effect of communication latency that may negatively impact real-time communication with mission control
- D. The use of centrally managed military network and computers by soldiers when communicating with external parties
Answer: A
NEW QUESTION 13
A security engineer is attempting to convey the importance of including job rotation in a company’s standard security policies. Which of the following would be the BEST justification?
- A. Making employees rotate through jobs ensures succession plans can be implemented and prevents single point of failure.
- B. Forcing different people to perform the same job minimizes the amount of time malicious actions go undetected by forcing malicious actors to attempt collusion between two or more people.
- C. Administrators and engineers who perform multiple job functions throughout the day benefit from being cross-trained in new job areas.
- D. It eliminates the need to share administrative account passwords because employees gain administrative rights as they rotate into a new job area.
Answer: B
NEW QUESTION 14
It has come to the IT administrator’s attention that the “post your comment” field on the company blog page has been explogted, resulting in cross-site scripting attacks against customers reading the blog. Which of the following would be the MOST effective at preventing the “post your comment” field from being explogted?
- A. Update the blog page to HTTPS
- B. Filter metacharacters
- C. Install HIDS on the server
- D. Patch the web application
- E. Perform client side input validation
Answer: B
Explanation:
A general rule of thumb with regards to XSS is to "Never trust user input and always filter metacharacters." Incorrect Answers:
A: Updating the blog page to HTTPS will not resolve this issue.
C: HIDS are designed to monitor a computer system, not the network. IT will, therefore, not resolve this issue.
D: Simply installing a web application patch will not work, as the patch may be susceptible to XSS. Testing of the patch has to take place first.
E: Performing client side input validation is a valid method, but it is not the MOST effective. References:
https://community.qualys.com/docs/DOC-1186
http://www.computerweHYPERLINK "http://www.computerweekly.com/tip/The-true-test-of-a-Webapplication- patch"ekly.com/tip/The-truHYPERLINK "http://www.computerweekly.com/tip/The-truetest-
of-a-Web-application-patch"e-test-of-a-Web-application-patch
httpHYPERLINK "http://www.techrepublic.com/blog/it-security/what-is-cross-sitehttps:// certkingdom.com
scripting/"://www.techreHYPERLINK "http://www.techrepublic.com/blog/it-security/what-is-crosssite- scripting/"pHYPERLINK "http://www.techrepublic.com/blog/it-security/what-is-cross-sitescripting/" ublic.com/blog/it-security/what-is-cross-site-scripting/
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 137
NEW QUESTION 15
A mature organization with legacy information systems has incorporated numerous new processes and dependencies to manage security as its networks and infrastructure are modernized. The Chief Information Office has become increasingly frustrated with frequent releases, stating that the organization needs everything to work completely, and the vendor should already have those desires built into the software product. The vendor has been in constant communication with personnel and groups within the organization to understand its business process and capture new software requirements from users. Which of the following methods of software development is this organization’s configuration management process using?
- A. Agile
- B. SDL
- C. Waterfall
- D. Joint application development
Answer: A
Explanation:
In agile software development, teams of programmers and business experts work closely together, using an iterative approach.
Incorrect Answers:
B: The Microsoft developed security development life cycle (SDL) is designed to minimize the security-related design and coding bugs in software. An organization that implements SDL has a central security team that performs security functions.
C: The waterfall model is a sequential software development processes, in which progress is seen as flowing steadily downwards through the phases of conception, initiation, analysis, design, construction, testing, production/implementation and maintenance.
D: The vendor is still responsible for developing the solution, Therefore this is not an example of joint application development.
References:
BOOK pp. 371, 374
https://en.wikipedia.org/wiki/Waterfall_model
NEW QUESTION 16
......
Thanks for reading the newest CAS-003 exam dumps! We recommend you to try the PREMIUM Dumps-hub.com CAS-003 dumps in VCE and PDF here: https://www.dumps-hub.com/CAS-003-dumps.html (555 Q&As Dumps)