CAS-003 | The Most Up-to-date Guide To CAS-003 Exams
we provide 100% Guarantee CompTIA CAS-003 test question which are the best for clearing CAS-003 test, and to get certified by CompTIA CompTIA Advanced Security Practitioner (CASP). The CAS-003 Questions & Answers covers all the knowledge points of the real CAS-003 exam. Crack your CompTIA CAS-003 Exam with latest dumps, guaranteed!
CompTIA CAS-003 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
An organization has established the following controls matrix: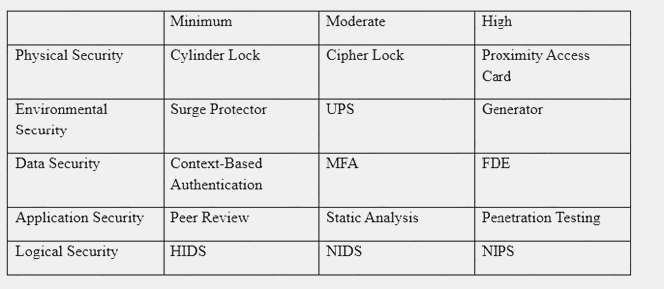
The following control sets have been defined by the organization and are applied in aggregate fashion:
Systems containing PII are protected with the minimum control set. Systems containing medical data are protected at the moderate level. Systems containing cardholder data are protected at the high level.
The organization is preparing to deploy a system that protects the confidentially of a database containing PII and medical data from clients. Based on the controls classification, which of the following controls would BEST meet these requirements?
- A. Proximity card access to the server room, context-based authentication, UPS, and full-disk encryption for the database server.
- B. Cipher lock on the server room door, FDE, surge protector, and static analysis of all application code.
- C. Peer review of all application changes, static analysis of application code, UPS, and penetration testing of the complete system.
- D. Intrusion detection capabilities, network-based IPS, generator, and context-based authenticatio
Answer: D
NEW QUESTION 2
Given the following output from a security tool in Kali:
- A. Log reduction
- B. Network enumerator
- C. Fuzzer
- D. SCAP scanner
Answer: D
NEW QUESTION 3
An engineer maintains a corporate-owned mobility infrastructure, and the organization requires that all web browsing using corporate-owned resources be monitored. Which of the following would allow the organization to meet its requirement? (Choose two.)
- A. Exempt mobile devices from the requirement, as this will lead to privacy violations
- B. Configure the devices to use an always-on IPSec VPN
- C. Configure all management traffic to be tunneled into the enterprise via TLS
- D. Implement a VDI solution and deploy supporting client apps to devices
- E. Restrict application permissions to establish only HTTPS connections outside of the enterprise boundary
Answer: BE
NEW QUESTION 4
A security engineer is performing an assessment again for a company. The security engineer examines the following output from the review:
Which of the following tools is the engineer utilizing to perform this assessment?
- A. Vulnerability scanner
- B. SCAP scanner
- C. Port scanner
- D. Interception proxy
Answer: B
NEW QUESTION 5
An analyst connects to a company web conference hosted on www.webconference.com/meetingID#01234 and observes that numerous guests have been allowed to join, without providing identifying information. The topics covered during the web conference are considered proprietary to the company. Which of the following security concerns does the analyst present to management?
- A. Guest users could present a risk to the integrity of the company’s information.
- B. Authenticated users could sponsor guest access that was previously approved by management.
- C. Unauthenticated users could present a risk to the confidentiality of the company’s information.
- D. Meeting owners could sponsor guest access if they have passed a background chec
Answer: C
Explanation:
The issue at stake in this question is confidentiality of information. Topics covered during the web conference are considered proprietary and should remain confidential, which means it should not be shared with unauthorized users.
Incorrect Answers:
A: Integrity of information is centered on the modification or alternation of information. Information remains unchanged and is in its true original form during transmission and storage. The issue of guests at a Web conference is related to confidentiality of information.
B: The issue at stake in this question is confidentiality of information. Topics covered during the web conference are considered proprietary and should remain confidential, which means it should not be shared with guests.
D: The issue at stake in this question is confidentiality of information. Topics covered during the web conference are considered proprietary and should remain confidential, which means it should not be shared with guests, whether they have passed background checks or not.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 3
NEW QUESTION 6
The Chief Executive Officer (CEO) of a small start-up company wants to set up offices around the country for the sales staff to generate business. The company needs an effective communication solution to remain in constant contact with each other, while maintaining a secure business environment. A junior-level administrator suggests that the company and the sales staff stay connected via free social medi
- A. Which of the following decisions is BEST for the CEO to make?
- B. Social media is an effective solution because it is easily adaptable to new situations.
- C. Social media is an ineffective solution because the policy may not align with the business.
- D. Social media is an effective solution because it implements SSL encryption.
- E. Social media is an ineffective solution because it is not primarily intended for business applications.
Answer: B
Explanation:
Social media networks are designed to draw people’s attention quickly and to connect people is thus the main focus; security is not the main concern. Thus the CEO should decide that it would be ineffective to use social media in the company as it does not align with the company business. Incorrect Answers:
A: Social media is not designed to be easily adaptable to new situations in a workplace.
C: Social media does not necessarily make use of SSL encryption since it is designed to draw people’s attention and connect them quickly.
D: Social media, though a great channel for communication is not intended for business applications. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 290-293
NEW QUESTION 7
An external penetration tester compromised one of the client organization’s authentication servers and retrieved the password database. Which of the following methods allows the penetration tester to MOST efficiently use any obtained administrative credentials on the client organization’s other systems, without impacting the integrity of any of the systems?
- A. Use the pass the hash technique
- B. Use rainbow tables to crack the passwords
- C. Use the existing access to change the password
- D. Use social engineering to obtain the actual password
Answer: A
Explanation:
With passing the hash you can grab NTLM credentials and you can manipulate the Windows logon sessions maintained by the LSA component. This will allow you to operate as an administrative user and not impact the integrity of any of the systems when running your tests.
Incorrect Answers:
B: Making use of rainbow tables and cracking passwords will have a definite impact on the integrity of the other systems that are to be penetration tested.
C: Changing passwords will impact the integrity of the other systems and is not a preferable method to conduct penetration testing.
D: Social engineering is not the preferred way to accomplish the goal of penetration testing and
gaining administrative credentials on the client’s network. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 17, 351
NEW QUESTION 8
Company.org has requested a black-box security assessment be performed on key cyber terrain. On area of concern is the company’s SMTP services. The security assessor wants to run reconnaissance before taking any additional action and wishes to determine which SMTP server is Internet-facing. Which of the following commands should the assessor use to determine this information?
- A. dnsrecon –d company.org –t SOA
- B. dig company.org mx
- C. nc –v company.org
- D. whois company.org
Answer: A
NEW QUESTION 9
There have been some failures of the company’s internal facing website. A security engineer has found the WAF to be the root cause of the failures. System logs show that the WAF has been unavailable for 14 hours over the past month, in four separate situations. One of these situations was a two hour scheduled maintenance time, aimed at improving the stability of the WAF. Using the MTTR based on the last month’s performance figures, which of the following calculations is the percentage of uptime assuming there were 722 hours in the month?
- A. 92.24 percent
- B. 98.06 percent
- C. 98.34 percent
- D. 99.72 percent
Answer: B
Explanation:
A web application firewall (WAF) is an appliance, server plugin, or filter that applies a set of rules to an HTTP conversation. Generally, these rules cover common attacks such as cross-site scripting (XSS) and SQL injection. By customizing the rules to your application, many attacks can be identified and blocked.
14h of down time in a period of 772 supposed uptime = 14/772 x 100 = 1.939 % Thus the % of uptime = 100% - 1.939% = 98.06%
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 43, 116
NEW QUESTION 10
A new web based application has been developed and deployed in production. A security engineer decides to use an HTTP interceptor for testing the application. Which of the following problems would MOST likely be uncovered by this tool?
- A. The tool could show that input validation was only enabled on the client side
- B. The tool could enumerate backend SQL database table and column names
- C. The tool could force HTTP methods such as DELETE that the server has denied
- D. The tool could fuzz the application to determine where memory leaks occur
Answer: A
Explanation:
A HTTP Interceptor is a program that is used to assess and analyze web traffic thus it can be used to indicate that input validation was only enabled on the client side.
Incorrect Answers:
B: Assessing and analyzing web traffic is not used to enumerate backend SQL database tables and column names.
C: HTTP methods such as Delete that the server has denied are not performed by the HTTP interceptor.
D: Application fuzzing is not performed by the HTTP interceptor tool. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 181
NEW QUESTION 11
An organization is selecting a SaaS provider to replace its legacy, in house Customer Resource Management (CRM) application. Which of the following ensures the organization mitigates the risk of managing separate user credentials?
- A. Ensure the SaaS provider supports dual factor authentication.
- B. Ensure the SaaS provider supports encrypted password transmission and storage.
- C. Ensure the SaaS provider supports secure hash file exchange.
- D. Ensure the SaaS provider supports role-based access control.
- E. Ensure the SaaS provider supports directory services federatio
Answer: E
Explanation:
A SaaS application that has a federation server within the customer's network that interfaces with the customer's own enterprise user-directory service can provide single sign-on authentication. This federation server has a trust relationship with a corresponding federation server located within the SaaS provider's network.
Single sign-on will mitigate the risk of managing separate user credentials. Incorrect Answers:
A: Dual factor authentication will provide identification of users via a combination of two different components. It will not, however, mitigate the risk of managing separate user credentials.
B: The transmission and storage of encrypted passwords will not mitigate the risk of managing separate user credentials.
C: A hash file is a file that has been converted into a numerical string by a mathematical algorithm, and has to be unencrypted with a hash key to be understood. It will not, however, mitigate the risk of managing separate user credentials.
D: Role-based access control (RBAC) refers to the restriction of system access to authorized users. It will not, however, mitigate the risk of managing separate user credentials.
References:
https://msdn.microsoft.com/en-us/library/aa905332.aspx https://en.wikipedia.org/wiki/Two-factor_authentication https://en.wikipedia.org/wiki/Encryption http://www.wisegeek.com/what-are-hash-files.htm https://en.wikipedia.org/wiki/Role-based_access_control
NEW QUESTION 12
An investigator wants to collect the most volatile data first in an incident to preserve the data that runs the highest risk of being lost. After memory, which of the following BEST represents the remaining order of volatility that the investigator should follow?
- A. File system information, swap files, network processes, system processes and raw disk blocks.
- B. Raw disk blocks, network processes, system processes, swap files and file system information.
- C. System processes, network processes, file system information, swap files and raw disk blocks.
- D. Raw disk blocks, swap files, network processes, system processes, and file system informatio
Answer: C
Explanation:
The order in which you should collect evidence is referred to as the Order of volatility. Generally, evidence should be collected from the most volatile to the least volatile. The order of volatility from most volatile to least volatile is as follows:
Data in RAM, including CPU cache and recently used data and applications Data in RAM, including system and network processes
Swap files (also known as paging files) stored on local disk drives Data stored on local disk drives
Logs stored on remote systems Archive media
Incorrect Answers:
A: System and network processes are more volatile than file system information and swap files. B: System and network processes are more volatile than raw disk blocks.
D: System and network processes are more volatile than raw disk blocks and swap files. References:
http://blogs.getcertifiedgetahead.com/security-forensic-performance-baseHYPERLINK "http://blogs.getcertifiedgetahead.com/security-forensic-performance-based-question/"d-question/
NEW QUESTION 13
The Chief Information Officer (CIO) has been asked to develop a security dashboard with the relevant metrics. The board of directors will use the dashboard to monitor and track the overall security posture of the organization. The CIO produces a basic report containing both KPI and KRI data in two separate sections for the board to review.
Which of the following BEST meets the needs of the board?
- A. KRI:- Compliance with regulations- Backlog of unresolved security investigations- Severity ofthreats and vulnerabilities reported by sensors- Time to patch critical issues on a monthly basisKPI:- Time to resolve open security items- % of suppliers with approved security control frameworks- EDR coverage across the fileet- Threat landscape rating
- B. KRI:- EDR coverage across the fileet- Backlog of unresolved security investigations- Time to patch critical issues on a monthly basis- Threat landscape ratingKPI:- Time to resolve open security items- Compliance with regulations- % of suppliers with approved security control frameworks- Severity of threats and vulnerabilities reported by sensors
- C. KRI:- EDR coverage across the fileet- % of suppliers with approved security control framework- Backlog of unresolved security investigations- Threat landscape ratingKPI:- Time to resolve open security items- Compliance with regulations- Time to patch critical issues on a monthly basis- Severity of threats and vulnerabilities reported by sensors
- D. KPI:- Compliance with regulations- % of suppliers with approved security control frameworks- Severity of threats and vulnerabilities reported by sensors- Threat landscape ratingKRI:- Time to resolve open security items- Backlog of unresolved security investigations- EDR coverage across the fileet- Time to patch critical issues on a monthly basis
Answer: A
NEW QUESTION 14
The network administrator at an enterprise reported a large data leak. One compromised server was used to aggregate data from several critical application servers and send it out to the Internet using HTTPS. Upon investigation, there have been no user logins over the previous week and the endpoint protection software is not reporting any issues. Which of the following BEST provides insight into where the compromised server collected the information?
- A. Review the flow data against each server’s baseline communications profile.
- B. Configure the server logs to collect unusual activity including failed logins and restarted services.
- C. Correlate data loss prevention logs for anomalous communications from the server.
- D. Setup a packet capture on the firewall to collect all of the server communication
Answer: A
Explanation:
Network logging tools such as Syslog, DNS, NetFlow, behavior analytics, IP reputation, honeypots, and DLP solutions provide visibility into the entire infrastructure. This visibility is important because signature-based systems are no longer sufficient for identifying the advanced attacker that relies heavily on custom malware and zero-day explogts. Having knowledge of each host’s communications, protocols, and traffic volumes as well as the content of the data in question is key to identifying zeroday and APT (advance persistent threat) malware and agents. Data intelligence allows forensic
analysis to identify anomalous or suspicious communications by comparing suspected traffic patterns against normal data communication behavioral baselines. Automated network intelligence and next-generation live forensics provide insight into network events and rely on analytical decisions based on known vs. unknown behavior taking place within a corporate network. Incorrect Answers:
B: The attack has already happened; the server has already been compromised. Configuring the server logs to collect unusual activity including failed logins and restarted services might help against future attacks but it will not provide information on an attack that has already happened.
C: It is unlikely the DLP logs would contain anomalous communications from the server that would identify where the server collected the information.
D: The attack has already happened; the server has already been compromised. Setting up a packet capture on the firewall to collect all of the server communications might help against future attacks but it will not provide information on an attack that has already happened.
References:
https://www.sans.HYPERLINK "https://www.sans.org/reading-room/whitepapers/forensics/ids-fileforensics- 35952"org/reading-room/whitepapers/forensics/ids-fiHYPERLINK
"https://www.sans.org/reading-room/whitepapers/forensics/ids-file-forensics-35952"le-forensics- 35952, p. 6
NEW QUESTION 15
An administrator is working with management to develop policies related to the use of the cloudbased resources that contain corporate data. Management plans to require some control over
organizational data stored on personal devices, such as tablets. Which of the following controls would BEST support management’s policy?
- A. MDM
- B. Sandboxing
- C. Mobile tokenization
- D. FDE
- E. MFA
Answer: A
NEW QUESTION 16
......
P.S. Certshared now are offering 100% pass ensure CAS-003 dumps! All CAS-003 exam questions have been updated with correct answers: https://www.certshared.com/exam/CAS-003/ (555 New Questions)