SY0-701 | All About Highest Quality SY0-701 Free Practice Test
Pass4sure offers free demo for SY0-701 exam. "CompTIA Security+ Exam", also known as SY0-701 exam, is a CompTIA Certification. This set of posts, Passing the CompTIA SY0-701 exam, will help you answer those questions. The SY0-701 Questions & Answers covers all the knowledge points of the real exam. 100% real CompTIA SY0-701 exams and revised by experts!
Check SY0-701 free dumps before getting the full version:
NEW QUESTION 1
A company has discovered unauthorized devices are using its WiFi network, and it wants to harden the access point to improve security. Which f the following configuration should an analysis enable
To improve security? (Select TWO.)
- A. RADIUS
- B. PEAP
- C. WPS
- D. WEP-EKIP
- E. SSL
- F. WPA2-PSK
Answer: AF
Explanation:
To improve the security of the WiFi network and prevent unauthorized devices from accessing the network, the configuration options of RADIUS and WPA2-PSK should be enabled. RADIUS (Remote Authentication Dial-In User Service) is an authentication protocol that can be used to control access to the WiFi network. It can provide stronger authentication and authorization than WEP and WPA. WPA2-PSK (WiFi Protected Access 2 with Pre-Shared Key) is a security protocol that uses stronger encryption than WEP and WPA. It requires a pre-shared key (PSK) to be entered on each device that wants to access the network. This helps prevent unauthorized devices from accessing the network.
NEW QUESTION 2
A security analyst receives an alert that indicates a user's device is displaying anomalous behavior The analyst suspects the device might be compromised Which of the following should the analyst to first?
- A. Reboot the device
- B. Set the host-based firewall to deny an incoming connection
- C. Update the antivirus definitions on the device
- D. Isolate the device
Answer: D
Explanation:
Isolating the device is the first thing that a security analyst should do if they suspect that a user’s device might be compromised. Isolating the device means disconnecting it from the network or placing it in a separate network segment to prevent further communication with potential attackers or malicious hosts. Isolating the device can help contain the incident, limit the damage or data loss, preserve the evidence, and facilitate the investigation and remediation.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://resources.infosecinstitute.com/topic/incident-response-process/
NEW QUESTION 3
The security team received a report of copyright infringement from the IP space of the corporate network. The report provided a precise time stamp for the incident as well as the name of the copyrighted files. The analyst has been tasked with determining the infringing source machine and instructed to implement measures to prevent such incidents from occurring again. Which of the following is MOST capable of accomplishing both tasks?
- A. HIDS
- B. Allow list
- C. TPM
- D. NGFW
Answer: D
Explanation:
Next-Generation Firewalls (NGFWs) are designed to provide advanced threat protection by combining traditional firewall capabilities with intrusion prevention, application control, and other security features. NGFWs can detect and block unauthorized access attempts, malware infections, and other suspicious activity. They can also be used to monitor file access and detect unauthorized copying or distribution of copyrighted material.
A next-generation firewall (NGFW) can be used to detect and prevent copyright infringement by analyzing network traffic and blocking unauthorized transfers of copyrighted material. Additionally, NGFWs can be configured to enforce access control policies that prevent unauthorized access to sensitive resources. References: CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 6
CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 6
NEW QUESTION 4
An organization wants to quickly assess how effectively the IT team hardened new laptops Which of the following would be the best solution to perform this assessment?
- A. Install a SIEM tool and properly configure it to read the OS configuration files.
- B. Load current baselines into the existing vulnerability scanner.
- C. Maintain a risk register with each security control marked as compliant or non-compliant.
- D. Manually review the secure configuration guide checklists.
Answer: B
Explanation:
A vulnerability scanner is a tool that can scan devices and systems for known vulnerabilities, misconfigurations, and compliance issues. By loading the current baselines into the scanner, the organization can compare the actual state of the new laptops with the desired state and identify any deviations or weaknesses. This is a quick and automated way to assess the hardening of the new laptops.
NEW QUESTION 5
A user received an SMS on a mobile phone that asked for bank details. Which of the following social engineering techniques was used in this case?
- A. SPIM
- B. Vishing
- C. Spear phishing
- D. Smishing
Answer: D
Explanation:
Smishing is a type of social engineering technique that involves sending fraudulent or malicious text messages (SMS) to a user’s mobile phone. It can trick the user into providing personal or financial information, clicking on malicious links, downloading malware, etc., by impersonating a legitimate entity or creating a sense of urgency or curiosity.
NEW QUESTION 6
A company wants to deploy decoy systems alongside production systems in order to entice threat actors and to learn more about attackers. Which of the follow r 3 best describes these systems?
- A. DNS sinkholes
- B. Honey pots
- C. Virtual machines
- D. Neural networks
Answer: B
Explanation:
Honey pots are decoy systems or resources that are designed to attract and deceive threat actors and to learn more about their motives, techniques, etc. They can be deployed alongside production systems to create an illusion of a vulnerable target and divert attacks away from the real systems. They can also collect valuable information and evidence about the attackers and their activities for further analysis or prosecution.
NEW QUESTION 7
While troubleshooting a firewall configuration, a technician determines that a "deny any" policy should be added to the bottom of the ACL. The technician updates the policy, but the new policy causes several company servers to become unreachable. Which of the following actions would prevent this issue?
- A. Documenting the new policy in a change request and submitting the request to change management
- B. Testing the policy in a non-production environment before enabling the policy in the production network
- C. Disabling any intrusion prevention signatures on the "deny any" policy prior to enabling the new policy
- D. Including an "allow any" policy above the "deny any" policy
Answer: B
Explanation:
Testing the policy in a non-production environment before enabling the policy in the production network would prevent the issue of making several company servers unreachable. A non-production environment is a replica of the production network that is used for testing, development, or training purposes. By testing the policy in a non-production environment, the technician can verify the functionality and impact of the policy without affecting the real network or users. This can help to identify and resolve any errors or conflicts before applying the policy to the production network. Testing the policy in a non-production environment can also help to ensure compliance with security standards and best practices.
NEW QUESTION 8
A major manufacturing company updated its internal infrastructure and just started to allow OAuth application to access corporate data Data leakage is being reported Which of following most likely caused the issue?
- A. Privilege creep
- B. Unmodified default
- C. TLS
- D. Improper patch management
Answer: A
Explanation:
Privilege creep is the gradual accumulation of access rights beyond what an individual needs to do his or her job. In information technology, a privilege is an identified right that a particular end user has to a particular system resource, such as a file folder or virtual machine. Privilege creep often occurs when an employee changes job responsibilities within an organization and is granted new privileges. While employees may need to retain their former privileges during a period of transition, those privileges are rarely revoked and result in an unnecessary accumulation of access privileges. Privilege creep creates a security risk by increasing the attack surface and exposing sensitive data or systems to unauthorized or malicious users.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://www.techtarget.com/searchsecurity/definition/privilege-creep
NEW QUESTION 9
The following are the logs of a successful attack.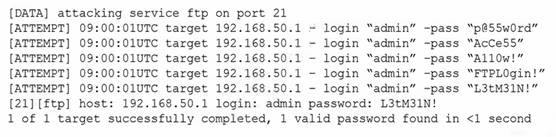
Which of the following controls would be BEST to use to prevent such a breach in the future?
- A. Password history
- B. Account expiration
- C. Password complexity
- D. Account lockout
Answer: C
Explanation:
To prevent such a breach in the future, the BEST control to use would be Password complexity.
Password complexity is a security measure that requires users to create strong passwords that are difficult to guess or crack. It can help prevent unauthorized access to systems and data by making it more difficult for attackers to guess or crack passwords.
The best control to use to prevent a breach like the one shown in the logs is password complexity. Password complexity requires users to create passwords that are harder to guess, by including a mix of upper and lowercase letters, numbers, and special characters. In the logs, the attacker was able to guess the user's password using a dictionary attack, which means that the password was not complex enough. References: CompTIA Security+ Certification Exam Objectives - Exam SY0-601
CompTIA Security+ Certification Exam Objectives - Exam SY0-601
NEW QUESTION 10
A software development manager wants to ensure the authenticity of the code created by the company. Which of the following options is the most appropriate?
- A. Testing input validation on the user input fields
- B. Performing code signing on company-developed software
- C. Performing static code analysis on the software
- D. Ensuring secure cookies are used
Answer: B
Explanation:
Code signing is a cryptographic process that allows software developers to digitally sign their code. This ensures that the code has not been tampered with since it was signed and that it came from a trusted source.
Testing input validation on the user input fields is important for preventing malicious code from being entered into a system. However, it does not address the authenticity of the code itself.
Performing static code analysis on the software can help to identify security vulnerabilities. However, it cannot guarantee that the code has not been tampered with.
Ensuring secure cookies are used is important for preventing unauthorized access to user data. However, it does not address the authenticity of the code itself.
Therefore, the most appropriate option to ensure the authenticity of the code created by the company is to perform code signing on the software.
Here are some additional benefits of code signing: It can help to prevent malware from being installed on users' computers.
It can help to prevent malware from being installed on users' computers.  It can help to protect intellectual property.
It can help to protect intellectual property. It can help to improve user trust.
It can help to improve user trust.
NEW QUESTION 11
A business is looking for a cloud service provider that offers a la carte services, including cloud backups, VM elasticity, and secure networking. Which of the following cloud service provider types should business engage?
- A. A laaS
- B. PaaS
- C. XaaS
- D. SaaS
Answer: A
Explanation:
Infrastructure as a Service (IaaS) providers offer a la carte services, including cloud backups, VM elasticity, and secure networking. With IaaS, businesses can rent infrastructure components such as virtual machines, storage, and networking from a cloud service provider. References: CompTIA Security+ Study Guide, pages 233-234
NEW QUESTION 12
Which of the following environments utilizes dummy data and is MOST likely to be installed locally on a system that allows code to be assessed directly and modified easily with each build?
- A. Production
- B. Test
- C. Staging
- D. Development
Answer: D
Explanation:
A development environment is the environment that is used to develop and test software. It is typically installed locally on a system that allows code to be assessed directly and modified easily with each build. In this environment, dummy data is often utilized to test the software's functionality.
Reference: CompTIA Security+ Study Guide, Exam SY0-601, Chapter 3: Architecture and Design
NEW QUESTION 13
Which of the following involves the inclusion of code in the main codebase as soon as it is written?
- A. Continuous monitoring
- B. Continuous deployment
- C. Continuous Validation
- D. Continuous integration
Answer: D
Explanation:
Detailed
Continuous Integration (CI) is a practice where developers integrate code into a shared repository frequently, preferably several times a day. Each integration is verified by an automated build and automated tests. CI allows for the detection of errors early in the development cycle, thereby reducing overall development costs.
NEW QUESTION 14
A security analyst reviews web server logs and notices the following line: 104.35. 45.53 [22/May/2020:07 : 00:58 +0100] "GET . UNION ALL SELECT
user login, user _ pass, user email from wp users—— HTTP/I.I" 200 1072
http://www.example.com/wordpress/wp—admin/
Which of the following vulnerabilities is the attacker trying to exploit?
- A. SSRF
- B. CSRF
- C. xss
- D. SQLi
Answer: D
Explanation:
SQLi stands for SQL injection, which is a type of web security vulnerability that allows an attacker to execute malicious SQL statements on a database server. SQLi can result in data theft, data corruption, denial of service, or remote code execution.
The attacker in the web server log is trying to exploit a SQLi vulnerability by sending a malicious GET request that contains a UNION ALL SELECT statement. This statement is used to combine the results of two or more SELECT queries into a single result set. The attacker is attempting to retrieve user login, user pass, and user email from the wp users table, which is a WordPress database table that stores user information. The attacker may use this information to compromise the WordPress site or the users’ accounts.
NEW QUESTION 15
An organization's corporate offices were destroyed due to a natural disaster, so the organization is now setting up offices in a temporary work space. Which of the following will the organization most likely consult?
- A. The business continuity plan
- B. The risk management plan
- C. The communication plan
- D. The incident response plan
Answer: A
Explanation:
A business continuity plan is a document or a process that outlines how an organization can continue its critical operations and functions in the event of a disruption or disaster. It can include strategies and procedures for recovering or relocating resources, personnel, data, etc., to ensure minimal downtime and impact. The organization will most likely consult the business continuity plan when setting up offices in a temporary work space after its corporate offices were destroyed due to a natural disaster.
NEW QUESTION 16
......
100% Valid and Newest Version SY0-701 Questions & Answers shared by Dumps-hub.com, Get Full Dumps HERE: https://www.dumps-hub.com/SY0-701-dumps.html (New 0 Q&As)