SY0-701 | Rebirth SY0-701 Exam For CompTIA Security+ Exam Certification
It is more faster and easier to pass the CompTIA SY0-701 exam by using 100% Correct CompTIA CompTIA Security+ Exam questuins and answers. Immediate access to the Far out SY0-701 Exam and find the same core area SY0-701 questions with professionally verified answers, then PASS your exam with a high score now.
Online SY0-701 free questions and answers of New Version:
NEW QUESTION 1
A company would like to protect credit card information that is stored in a database from being exposed and reused. However, the current POS system does not support encryption. Which of the following would be BEST suited to secure this information?
(Give me related explanation and references from CompTIA Security+ SY0-601 documents for Correct answer option)
- A. Masking
- B. Tokenization
- C. DLP
- D. SSL/TLS
Answer: B
Explanation:
Tokenization replaces sensitive data with non-sensitive data, such as a unique identifier. This means that the data is still present in the system, but the sensitive information itself is replaced with the token. Tokenization is more secure than masking, which only obscures the data but does not eliminate it. DLP is not suitable for this task, as it is designed to prevent the loss or leakage of data from the system. SSL/TLS can be used to secure the transmission of data, but it cannot prevent the data itself from being exposed or reused. For more information, please refer to CompTIA Security+ SY0-601 Exam Objectives, Section 3.3: Explain the security purpose of authentication, authorization and accounting (AAA) services, and Section 4.7: Explain the purpose and characteristics of various types of encryption.
NEW QUESTION 2
Which of the following BEST describes the method a security analyst would use to confirm a file that is downloaded from a trusted security website is not altered in transit or corrupted using a verified checksum?
- A. Hashing
- B. Salting
- C. Integrity
- D. Digital signature
Answer: A
Explanation:
Hashing is a cryptographic function that produces a unique fixed-size output (i.e., hash value) from an input (i.e., data). The hash value is a digital fingerprint of the data, which means that if the data changes, so too does the hash value. By comparing the hash value of the downloaded file with the hash value provided by the security website, the security analyst can verify that the file has not been altered in transit or corrupted.
NEW QUESTION 3
Which of the following should a Chief Information Security Officer consider using to take advantage of industry standard guidelines?
- A. SSAE SOC 2
- B. GDPR
- C. PCI DSS
- D. NIST CSF
Answer: D
Explanation:
NIST CSF (National Institute of Standards and Technology Cybersecurity Framework) is a set of guidelines and best practices for managing cybersecurity risks. It is based on existing standards, guidelines, and practices that are widely recognized and applicable across different sectors and organizations. It provides a common language and framework for understanding, communicating, and managing cybersecurity risks. References: 1
CompTIA Security+ Certification Exam Objectives, page 7, Domain 1.0: Attacks, Threats, and
Vulnerabilities, Objective 1.4: Explain the techniques used in security assessments 2
CompTIA Security+ Certification Exam Objectives, page 8, Domain 2.0: Architecture and Design, Objective 2.1: Explain the importance of secure staging deployment concepts 3 https://www.nist.gov/cyberframework
NEW QUESTION 4
A company would like to provide flexibility for employees on device preference. However, the company is concerned about supporting too many different types of hardware. Which of the following deployment models will provide the needed flexibility with the GREATEST amount of control and security over company data and infrastructure?
- A. BYOD
- B. VDI
- C. COPE
- D. CYOD
Answer: D
Explanation:
Choose Your Own Device (CYOD) is a deployment model that allows employees to select from a predefined list of devices. It provides employees with flexibility in device preference while allowing the company to maintain control and security over company data and infrastructure. CYOD deployment model provides a compromise between the strict control provided by Corporate-Owned, Personally Enabled (COPE) deployment model and the flexibility provided by Bring Your Own Device (BYOD) deployment model. References: CompTIA Security+ Study Guide, Chapter 6: Securing Application, Data, and Host Security, 6.5 Implement Mobile Device Management, pp. 334-335
NEW QUESTION 5
A security architect is working on an email solution that will send sensitive data. However, funds are not currently available in the budget for building additional infrastructure. Which of the following should the architect choose?
- A. POP
- B. IPSec
- C. IMAP
- D. PGP
Answer: D
Explanation:
PGP (Pretty Good Privacy) is a commonly used encryption method for email communications to secure the sensitive data being sent. It allows for the encryption of the entire message or just the sensitive parts. It would be an appropriate solution in this case as it doesn't require additional infrastructure to implement.
NEW QUESTION 6
Which of the following describes business units that purchase and implement scripting software without approval from an organization's technology Support staff?
- A. Shadow IT
- B. Hacktivist
- C. Insider threat
- D. script kiddie
Answer: A
Explanation:
shadow IT is the use of IT-related hardware or software by a department or individual without the knowledge or approval of the IT or security group within the organization12. Shadow IT can encompass cloud services, software, and hardware. The main area of concern today is the rapid adoption of cloud-based service1s.
According to one source3, shadow IT helps you know and identify which apps are being used and what your risk level is. 80% of employees use non-sanctioned apps that no one has reviewed, and may not be compliant with your security and compliance policies.
NEW QUESTION 7
Which of the following procedures would be performed after the root cause of a security incident has been identified to help avoid future incidents from occurring?
- A. Walk-throughs
- B. Lessons learned
- C. Attack framework alignment
- D. Containment
Answer: B
Explanation:
After the root cause of a security incident has been identified, it is important to take the time to analyze what went wrong and how it could have been prevented. This process is known as “lessons learned” and allows organizations to identify potential improvements to their security processes and protocols. Lessons learned typically involve a review of the incident and the steps taken to address it, a review of the security systems and procedures in place, and an analysis of any potential changes that can be made to prevent similar incidents from occurring in the future.
NEW QUESTION 8
A company is launching a website in a different country in order to capture user information that a marketing business can use. The company itself will not be using the information. Which of the following roles is the company assuming?
- A. Data owner
- B. Data processor
- C. Data steward
- D. Data collector
Answer: D
Explanation:
A data collector is a person or entity that collects personal data from individuals for a specific purpose. A data collector may or may not be the same as the data controller or the data processor, depending on who determines the purpose and means of processing the data and who actually processes the data.
NEW QUESTION 9
A company recently experienced a significant data loss when proprietary information was leaked to a competitor. The company took special precautions by using proper labels; however, email filter logs do not have any record of the incident. An investigation confirmed the corporate network was not breached, but documents were downloaded from an employee's COPE tablet and passed to the competitor via cloud storage. Which of the following is the best mitigation strategy to prevent this from happening in the future?
- A. User training
- B. CAsB
- C. MDM
- D. EDR
Answer: C
Explanation:
MDM stands for mobile device management, which is a solution that allows organizations to manage and secure mobile devices used by employees. MDM can help prevent data loss and leakage by enforcing policies and restrictions on the devices, such as encryption, password, app installation, remote wipe, and so on. MDM can also monitor and audit the device activity and compliance status. MDM can be the best mitigation strategy to prevent data leakage from an employee’s COPE tablet via cloud storage, as it can block or limit the access to cloud services, or apply data protection measures such as containerization or encryption. References: https://www.blackberry.com/us/en/solutions/corporate-owned-personally-enabled
https://www.blackberry.com/us/en/solutions/corporate-owned-personally-enabled https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/mobile-device-management/
https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/mobile-device-management/
NEW QUESTION 10
Historically, a company has had issues with users plugging in personally owned removable media devices into corporate computers. As a result, the threat of malware incidents is almost constant. Which of the following would best help prevent the malware from being installed on the computers?
- A. AUP
- B. NGFW
- C. DLP
- D. EDR
Answer: D
Explanation:
EDR stands for Endpoint Detection and Response, which is a technology that monitors, detects, and responds to cyber threats on endpoint devices, such as laptops, desktops, servers, or mobile devices. EDR collects and analyzes data from endpoints to identify suspicious or malicious activities, such as malware installation, file modification, registry changes, network connections, or user actions. EDR also provides tools and capabilities to respond to threats, such as isolating infected devices, blocking malicious processes, removing malware, or restoring files.
Historically, a company has had issues with users plugging in personally owned removable media devices into corporate computers. As a result, the threat of malware incidents is almost constant. EDR would best help prevent the malware from being installed on the computers by detecting the insertion of removable media devices and scanning them for any malicious code or files. EDR would also alert the security team of any potential infection and enable them to take immediate action to contain and remediate the threat.
NEW QUESTION 11
Which of the technologies is used to actively monitor for specific file types being transmitted on the network?
- A. File integrity monitoring
- B. Honeynets
- C. Tcpreplay
- D. Data loss prevention
Answer: D
Explanation:
Data loss prevention (DLP) is a technology used to actively monitor for specific file types being transmitted on the network. DLP solutions can prevent the unauthorized transfer of sensitive information, such as credit card numbers and social security numbers, by monitoring data in motion.
References: CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 2: Technologies and Tools, pp. 99-102.
NEW QUESTION 12
The Chief Technology Officer of a local college would like visitors to utilize the school's WiFi but must be able to associate potential malicious activity to a specific person. Which of the following would BEST allow this objective to be met?
- A. Requiring all new, on-site visitors to configure their devices to use WPS
- B. Implementing a new SSID for every event hosted by the college that has visitors
- C. Creating a unique PSK for every visitor when they arrive at the reception area
- D. Deploying a captive portal to capture visitors' MAC addresses and names
Answer: D
Explanation:
A captive portal is a web page that requires visitors to authenticate or agree to an acceptable use policy before allowing access to the network. By capturing visitors' MAC addresses and names, potential malicious activity can be traced back to a specific person.
NEW QUESTION 13
An audit report indicates multiple suspicious attempts to access company resources were made. These attempts were not detected by the company. Which of the following would be the best solution to implement on the company's network?
- A. Intrusion prevention system
- B. Proxy server
- C. Jump server
- D. Security zones
Answer: A
Explanation:
An intrusion prevention system (IPS) is the best solution to implement on the company’s network to detect and prevent suspicious attempts to access company resources. An IPS is a network security technology that continuously monitors network traffic for malicious or anomalous activity and takes automated actions to block or mitigate it. An IPS can also alert the system administrators of any potential threats and provide detailed logs and reports of the incidents. An IPS can help the company to improve its security posture and prevent data breaches, unauthorized access, or denial-of-service attacks. References: https://www.paloaltonetworks.com/cyberpedia/what-is-an-intrusion-prevention-system-ips
https://www.paloaltonetworks.com/cyberpedia/what-is-an-intrusion-prevention-system-ips  https://www.forcepoint.com/cyber-edu/intrusion-prevention-system-ips
https://www.forcepoint.com/cyber-edu/intrusion-prevention-system-ips
NEW QUESTION 14
A local server recently crashed, and the team is attempting to restore the server from a backup. During the restore process, the team notices the file size of each daily backup is large and will run out of space at the current rate.
The current solution appears to do a full backup every night. Which of the following would use the least amount of storage space for backups?
- A. A weekly, incremental backup with daily differential backups
- B. A weekly, full backup with daily snapshot backups
- C. A weekly, full backup with daily differential backups
- D. A weekly, full backup with daily incremental backups
Answer: D
Explanation:
A weekly, full backup with daily incremental backups would use the least amount of storage space for backups, as it would only store the changes made since the last backup, whether it is a full or incremental backup. Incremental backups are faster and use less storage space than full or differential backups, but they require more time and media to restore data. A full backup is a complete copy of all data, which requires more time and storage space to perform, but allows a faster and easier recovery. A differential backup is a copy of the data that changed since the last full backup, which requires less time and storage space than a full backup, but more than an incremental backup. A differential backup allows a faster recovery than an incremental backup, but slower than a full backup. References: https://www.nakivo.com/blog/backup-types-explained/
https://www.nakivo.com/blog/backup-types-explained/
NEW QUESTION 15
A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
Perform the following steps:
* 1. Configure the RADIUS server.
* 2. Configure the WiFi controller.
* 3. Preconfigure the client for an incoming guest. The guest AD credentials are:
User: guest01 Password: guestpass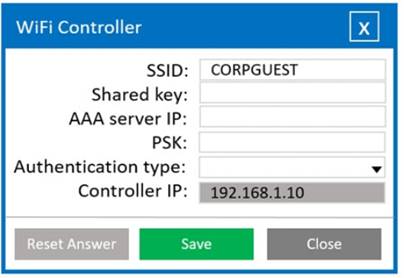
Solution:
Wifi Controller SSID: CORPGUEST
SHARED KEY: Secret
AAA server IP: 192.168.1.20
PSK: Blank
Authentication type: WPA2-EAP-PEAP-MSCHAPv2 Controller IP: 192.168.1.10
Radius Server Shared Key: Secret
Client IP: 192.168.1.10
Authentication Type: Active Directory Server IP: 192.168.1.20
Wireless Client SSID: CORPGUEST
Username: guest01 Userpassword: guestpass PSK: Blank
Authentication type: WPA2-Enterprise
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
......
P.S. Easily pass SY0-701 Exam with 0 Q&As Dumps-hub.com Dumps & pdf Version, Welcome to Download the Newest Dumps-hub.com SY0-701 Dumps: https://www.dumps-hub.com/SY0-701-dumps.html (0 New Questions)