SY0-701 | What Breathing SY0-701 Test Question Is
Pass4sure offers free demo for SY0-701 exam. "CompTIA Security+ Exam", also known as SY0-701 exam, is a CompTIA Certification. This set of posts, Passing the CompTIA SY0-701 exam, will help you answer those questions. The SY0-701 Questions & Answers covers all the knowledge points of the real exam. 100% real CompTIA SY0-701 exams and revised by experts!
CompTIA SY0-701 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
A company is auditing the manner in which its European customers’ personal information is handled. Which of the following should the company consult?
- A. GDPR
- B. ISO
- C. NIST
- D. PCI DSS
Answer: A
Explanation:
GDPR stands for General Data Protection Regulation, which is a legal framework that sets guidelines for the collection and processing of personal information of individuals within the European Union (EU). GDPR also applies to organizations outside the EU that offer goods or services to, or monitor the behavior of, EU data subjects. GDPR aims to protect the privacy and rights of EU citizens and residents regarding their personal data. GDPR defines personal data as any information relating to an identified or identifiable natural person, such as name, identification number, location data, online identifiers, or any factors specific to the physical, physiological, genetic, mental, economic, cultural, or social identity of that person. A company that is auditing the manner in which its European customers’ personal information is handled should consult GDPR to ensure compliance with its rules and obligations. References: https://www.gdpreu.org/the-regulation/key-concepts/personal-data/
https://www.gdpreu.org/the-regulation/key-concepts/personal-data/ https://ico.org.uk/for-organisations-2/guide-to-data-protection/guide-to-the-general-data-protection-regula
https://ico.org.uk/for-organisations-2/guide-to-data-protection/guide-to-the-general-data-protection-regula
NEW QUESTION 2
A security analyst is investigating a report from a penetration test. During the penetration test, consultants were able to download sensitive data from a back-end server. The back-end server was exposing an API that should have only been available from the companVs mobile application. After reviewing the back-end server logs, the security analyst finds the following entries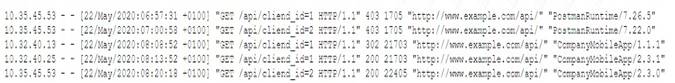
Which of the following is the most likely cause of the security control bypass?
- A. IP address allow list
- B. user-agent spoofing
- C. WAF bypass
- D. Referrer manipulation
Answer: B
Explanation:
User-agent spoofing is a technique that allows an attacker to modify the user-agent header of an HTTP request to impersonate another browser or device12. User-agent spoofing can be used to bypass security controls that rely on user-agent filtering or validation12. In this case, the attacker spoofed the user-agent header to match the company’s mobile application, which was allowed to access the back-end server’s API2.
NEW QUESTION 3
A company purchased cyber insurance to address items listed on the risk register. Which of the following strategies does this represent?
- A. Accept
- B. Transfer
- C. Mitigate
- D. Avoid
Answer: B
Explanation:
A company purchased cyber insurance to address items listed on the risk register. This represents a transfer strategy. A transfer strategy involves transferring or sharing some or all of the responsibility or impact of a risk to another party, such as an insurer, a supplier, or a partner. A transfer strategy can help to reduce the financial liability or exposure of the company in case of a security incident or breach. References: https://www.comptia.org/blog/what-is-cyber-insurance
https://www.certblaster.com/wp-content/uploads/2020/11/CompTIA-Security-SY0-601-Exam-Objectives-1.0.pd
NEW QUESTION 4
A security administrator examines the ARP table of an access switch and sees the following output: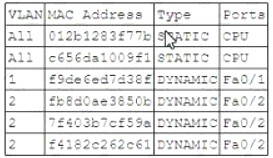
Which of the following is a potential threat that is occurring on this access switch?
- A. DDoSonFa02 port
- B. MAG flooding on Fa0/2 port
- C. ARP poisoning on Fa0/1 port
- D. DNS poisoning on port Fa0/1
Answer: C
Explanation:
ARP poisoning is a type of attack that exploits the ARP protocol to associate a malicious MAC address with a legitimate IP address on a network1. This allows the attacker to intercept, modify or drop traffic between the victim and other hosts on the same network. In this case, the ARP table of the access switch shows that the same MAC address (00-0c-29-58-35-3b) is associated with two different IP addresses (192.168.1.100 and 192.168.1.101) on port Fa0/12. This indicates that an attacker has poisoned the ARP table to redirect traffic intended for 192.168.1.100 to their own device with MAC address 00-0c-29-58-35-3b. The other options are not related to this scenario. DDoS is a type of attack that overwhelms a target with excessive traffic from multiple sources3. MAC flooding is a type of attack that floods a switch with fake MAC addresses to exhaust its MAC table and force it to operate as a hub4. DNS poisoning is a type of attack that corrupts the DNS cache with fake entries to redirect users to malicious websites.
References: 1: https://www.imperva.com/learn/application-security/arp-spoofing/ 2:
https://community.cisco.com/t5/networking-knowledge-base/network-tables-mac-routing-arp/ta-p/4184148 3:
https://www.imperva.com/learn/application-security/ddos-attack/ 4: https://www.imperva.com/learn/application-security/mac-flooding/ : https://www.imperva.com/learn/application-security/dns-spoofing-poisoning/
NEW QUESTION 5
A company's help desk has received calls about the wireless network being down and users being unable to connect to it The network administrator says all access points are up and running One of the help desk technicians notices the affected users are working in a building near the parking lot. Which of the following is the most likely reason for the outage?
- A. Someone near the building is jamming the signal
- B. A user has set up a rogue access point near the building
- C. Someone set up an evil twin access point in the affected area.
- D. The APs in the affected area have been unplugged from the network
Answer: A
Explanation:
Jamming is a type of denial-of-service attack that involves interfering with or blocking the wireless signal using a device that emits radio waves at the same frequency as the wireless network. It can cause the wireless network to be down and users to be unable to connect to it, especially if they are working in a building near the parking lot where someone could easily place a jamming device.
NEW QUESTION 6
A data cento has experienced an increase in under-voltage events Mowing electrical grid maintenance outside the facility These events are leading to occasional losses of system availability Which of the following would be the most cost-effective solution for the data center 10 implement''
- A. Uninterruptible power supplies with battery backup
- B. Managed power distribution units lo track these events
- C. A generator to ensure consistent, normalized power delivery
- D. Dual power supplies to distribute the load more evenly
Answer: A
Explanation:
Uninterruptible power supplies with battery backup would be the most cost-effective solution for the data center to implement to prevent under-voltage events following electrical grid maintenance outside the facility. An uninterruptible power supply (UPS) is a device that provides emergency power to a load when the main power source fails or drops below an acceptable level. A UPS with battery backup can help prevent under-voltage events by switching to battery power when it detects a voltage drop or outage in the main power source. A UPS with battery backup can also protect the data center equipment from power surges or spikes.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://www.apc.com/us/en/faqs/FA158852/
NEW QUESTION 7
A security administrator is compiling information from all devices on the local network in order to gain better visibility into user activities. Which of the following is the best solution to meet this objective?
- A. SIEM
- B. HIDS
- C. CASB
- D. EDR
Answer: A
Explanation:
SIEM stands for Security Information and Event Management, which is a solution that can collect, correlate, and analyze security logs and events from various devices on a network. SIEM can provide better visibility into user activities by generating reports, alerts, dashboards, and metrics. SIEM can also help detect and respond to security incidents, comply with regulations, and improve security posture.
NEW QUESTION 8
A security operations center wants to implement a solution that can execute files to test for malicious activity. The solution should provide a report of the files' activity against known threats.
Which of the following should the security operations center implement?
- A. theHarvester
- B. Nessus
- C. Cuckoo
- D. Sn1per
Answer: C
Explanation:
Cuckoo is a sandbox that is specifically written to run programs inside and identify any malware. A sandbox is a virtualized environment that isolates the program from the rest of the system and monitors its behavior. Cuckoo can analyze files of various types, such as executables, documents, URLs, and more. Cuckoo can provide a report of the files’ activity against known threats, such as network traffic, file operations, registry changes, API calls, and so on.
A security operations center can implement Cuckoo to execute files to test for malicious activity and generate a report of the analysis. Cuckoo can help the security operations center to detect and prevent malware infections, investigate incidents, and perform threat intelligence.
NEW QUESTION 9
A software company is analyzing a process that detects software vulnerabilities at the earliest stage possible. The goal is to scan the source looking for unsecure practices and weaknesses before the application is deployed in a runtime environment. Which of the following would BEST assist the company with this objective?
- A. Use fuzzing testing
- B. Use a web vulnerability scanner
- C. Use static code analysis
- D. Use a penetration-testing OS
Answer: C
Explanation:
Using static code analysis would be the best approach to scan the source code looking for unsecure practices and weaknesses before the application is deployed in a runtime environment. This method involves analyzing the source code without actually running the software, which can identify security vulnerabilities that may not be detected by other testing methods. References: CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 6: Risk Management, pp. 292-295
NEW QUESTION 10
A
candidate attempts to go to but accidentally visits http://comptiia.org. The malicious website looks exactly like the legitimate website. Which of the following best describes this type of attack?
- A. Reconnaissance
- B. Impersonation
- C. Typosquatting
- D. Watering-hole
Answer: C
Explanation:
Typosquatting is a type of cyberattack that involves registering domains with deliberately misspelled names of well-known websites. The attackers do this to lure unsuspecting visitors to alternative websites, typically for malicious purposes. Visitors may end up at these alternative websites by inadvertently mistyping the name of popular websites into their web browser or by being lured by a phishing scam. The attackers may emulate the look and feel of the legitimate websites and trick users into entering sensitive information or downloading malware.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives
https://www.kaspersky.com/resource-center/definitions/what-is-typosquatting
NEW QUESTION 11
A systems analyst determines the source of a high number of connections to a web server that were initiated by ten different IP addresses that belong to a network block in a specific country. Which of the following techniques will the systems analyst MOST likely implement to address this issue?
- A. Content filter
- B. SIEM
- C. Firewall rules
- D. DLP
Answer: C
Explanation:
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. The systems analyst can use firewall rules to block connections from the ten IP addresses in question, or from the entire network block in the specific country. This would be a quick and effective way to address the issue of high connections to the web server initiated by these IP addresses.
Reference: CompTIA Security+ SY0-601 Official Text Book, Chapter 5: "Network Security".
NEW QUESTION 12
An attacker is targeting a company. The attacker notices that the company’s employees frequently access a particular website. The attacker decides to infect the website with malware and hopes the employees’ devices will also become infected. Which of the following techniques is the attacker using?
- A. Watering-hole attack
- B. Pretexting
- C. Typosquatting
- D. Impersonation
Answer: A
Explanation:
a watering hole attack is a form of cyberattack that targets a specific group of users by infecting websites that they commonly visit123. The attacker seeks to compromise the user’s computer and gain access to the network at the user’s workplace or personal data123. The attacker observes the websites often visited by the victim or the group and infects those sites with malware14. The attacker may also lure the user to a malicious site4. A watering hole attack is difficult to diagnose and poses a significant threat to websites and users2.
NEW QUESTION 13
A company recently experienced an attack during which 5 main website was directed to the atack-er’s web server, allowing the attacker to harvest credentials from unsuspecting customers. Which of the following should the company Implement to prevent this type of attack from occurring in the future?
- A. IPSec
- B. SSL/TLS
- C. DNSSEC
- D. S/MIME
Answer: C
Explanation:
The attack described in the question is known as a DNS hijacking attack. In this type of attack, an attacker modifies the DNS records of a domain name to redirect traffic to their own server. This allows them to intercept traffic and steal sensitive information such as user credentials.
To prevent this type of attack from occurring in the future, the company should implement C. DNSSEC.
DNSSEC (Domain Name System Security Extensions) is a security protocol that adds digital signatures to DNS records. This ensures that DNS records are not modified during transit and prevents DNS hijacking attacks.
NEW QUESTION 14
An account was disabled atter several failed and successful login connections were made from various parts of the Word at various times. A security analysts investigating the issue. Which of the following account policies most likely triggered the action to disable the
- A. Time based logins
- B. Password history
- C. Geofencing
- D. Impossible travel time
Answer: D
Explanation:
Impossible travel time is a policy that detects and blocks login attempts from locations that are geographically impossible to reach from the previous login location within a certain time frame. For example, if a user logs in from New York and then tries to log in from Tokyo within an hour, the policy would flag this as impossible travel time and disable the account. This policy helps prevent unauthorized access from compromised credentials or attackers using proxy servers. References: 1
CompTIA Security+ Certification Exam Objectives
page 6, Domain 1.0: Attacks, Threats, and Vulnerabilities, Objective 1.2: Compare and contrast different types of social engineering techniques 2
CompTIA Security+ Certification Exam Objectives, page 14, Domain 3.0:
Implementation, Objective 3.4: Implement identity and account management controls 3
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-sign-in-risk-policy#impossi
NEW QUESTION 15
The application development team is in the final stages of developing a new healthcare application. The team has requested copies of current PHI records to perform the final testing.
Which of the following would be the best way to safeguard this information without impeding the testing process?
- A. Implementing a content filter
- B. Anonymizing the data
- C. Deploying DLP tools
- D. Installing a FIM on the application server
Answer: B
Explanation:
Anonymizing the data is the process of removing personally identifiable information (PII) from data sets, so that the people whom the data describe remain anonymous12. Anonymizing the data can safeguard the PHI records without impeding the testing process, because it can protect the privacy of the patients while
preserving the data integrity and statistical accuracy for the application development team12. Anonymizing the data can be done by using techniques such as data masking, pseudonymization, generalization, data swapping, or data perturbation12.
Implementing a content filter is not the best way to safeguard the information, because it is a technique that blocks or allows access to certain types of content based on predefined rules or policies3. A content filter does not remove or encrypt PII from data sets, and it may not prevent unauthorized access or leakage of PHI records.
Deploying DLP tools is not the best way to safeguard the information, because it is a technique that monitors and prevents data exfiltration or transfer to unauthorized destinations or users. DLP tools do not remove or encrypt PII from data sets, and they may not be sufficient to protect PHI records from internal misuse or negligence.
Installing a FIM on the application server is not the best way to safeguard the information, because it is a technique that detects and alerts changes to files or directories on a system. FIM does not remove or encrypt PII from data sets, and it may not prevent unauthorized access or modification of PHI records.
NEW QUESTION 16
......
Thanks for reading the newest SY0-701 exam dumps! We recommend you to try the PREMIUM Dumpscollection.com SY0-701 dumps in VCE and PDF here: https://www.dumpscollection.net/dumps/SY0-701/ (0 Q&As Dumps)