SY0-701 | All About Verified SY0-701 Actual Test
It is more faster and easier to pass the CompTIA SY0-701 exam by using Simulation CompTIA CompTIA Security+ Exam questuins and answers. Immediate access to the Renewal SY0-701 Exam and find the same core area SY0-701 questions with professionally verified answers, then PASS your exam with a high score now.
Online SY0-701 free questions and answers of New Version:
NEW QUESTION 1
A security analyst notices several attacks are being blocked by the NIPS but does not see anything on the boundary firewall logs. The attack seems to have been thwarted Which of the following resiliency techniques was applied to the network to prevent this attack?
- A. NIC Teaming
- B. Port mirroring
- C. Defense in depth
- D. High availability
- E. Geographic dispersal
Answer: C
Explanation:
Defense in depth is a resiliency technique that involves implementing multiple layers of security controls to protect against different types of threats. In this scenario, the NIPS likely provided protection at a different layer than the boundary firewall, demonstrating the effectiveness of defense in depth. References: CompTIA Security+ Certification Exam Objectives (SY0-601)
NEW QUESTION 2
A security architect at a large, multinational organization is concerned about the complexities and overhead of managing multiple encryption keys securely in a multicioud provider environment. The security architect is looking for a solution with reduced latency to allow the incorporation of the organization's existing keys and to maintain consistent, centralized control and management regardless of the data location. Which of the following would best meet the architect's objectives?
- A. Trusted Platform Module
- B. laaS
- C. HSMaas
- D. PaaS
Answer: C
Explanation:
HSMaas stands for Hardware Security Module as a Service, which is a cloud-based service that provides secure and scalable key management and cryptographic operations for data encryption and decryption. HSMaas allows the organization to use its own keys or generate new ones, and to control and manage them centrally regardless of where the data is stored or processed. HSMaas also reduces the latency and complexity of managing multiple encryption keys across different cloud providers, as well as the cost and maintenance of deploying physical HSM devices.
* A. Trusted Platform Module. This is not the correct answer, because a Trusted Platform Module (TPM) is a hardware chip that provides secure storage and generation of cryptographic keys on a device, such as a laptop or a server. A TPM does not offer a cloud-based solution for key management and encryption across multiple cloud providers.
* B. laaS. This is not the correct answer, because laaS stands for Infrastructure as a Service, which is a cloud computing model that provides virtualized computing resources, such as servers, storage, and networks, over the internet. laaS does not provide a specific solution for key management and encryption across multiple cloud providers.
* C. HSMaas. This is the correct answer, because HSMaas stands for Hardware Security Module as a Service, which is a cloud-based service that provides secure and scalable key management and cryptographic operations for data encryption and decryption across multiple cloud providers.
* D. PaaS. This is not the correct answer, because PaaS stands for Platform as a Service, which is a cloud computing model that provides a platform for developing and deploying applications over the internet. PaaS does not provide a specific solution for key management and encryption across multiple cloud providers.
Reference: HSM as a Service (HSMaaS) | Encryption Consulting, What Is Hardware Security Module (HSM
| Thales.
NEW QUESTION 3
A dynamic application vulnerability scan identified code injection could be performed using a web form. Which of the following will be BEST remediation to prevent this vulnerability?
- A. Implement input validations
- B. Deploy MFA
- C. Utilize a WAF
- D. Configure HIPS
Answer: A
Explanation:
Implementing input validations will prevent code injection attacks by verifying the type and format of user input. References: CompTIA Security+ Study Guide: Exam SY0-601, Chapter 8
NEW QUESTION 4
Which of the following biometric authentication methods is the MOST accurate?
- A. Gait
- B. Retina
- C. Signature
- D. Voice
Answer: B
Explanation:
Retina authentication is the most accurate biometric authentication method. Retina authentication is based on recognizing the unique pattern of blood vessels and other features in the retina. This makes it virtually impossible to duplicate or bypass, making it the most secure form of biometric authentication currently available.
NEW QUESTION 5
While researching a data exfiltration event, the security team discovers that a large amount of data was transferred to a file storage site on the internet. Which of the following controls would work best to reduce the risk of further exfiltration using this method?
- A. Data loss prevention
- B. Blocking IP traffic at the firewall
- C. Containerization
- D. File integrity monitoring
Answer: A
Explanation:
Data loss prevention (DLP) is a set of tools and processes that aim to prevent unauthorized access, use, or transfer of sensitive data. DLP can help reduce the risk of further exfiltration using file storage sites on the internet by monitoring and controlling data flows across endpoints, networks, and cloud services. DLP can also detect and block attempts to copy, upload, or download sensitive data to or from file storage sites based on predefined policies and rules.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://www.microsoft.com/en-us/security/business/security-101/what-is-data-loss-prevention-dlp
NEW QUESTION 6
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.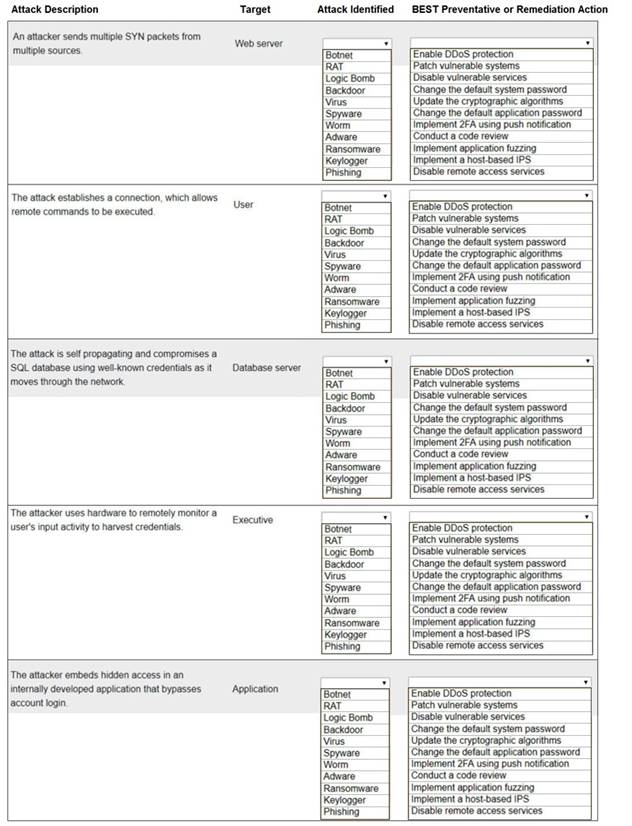
Solution:
Web serverBotnet Enable DDoS protectionUser RAT Implement a host-based IPSDatabase server Worm Change the default application passwordExecutive KeyloggerDisable vulnerable servicesApplication Backdoor Implement 2FA using push notification
A screenshot of a computer program Description automatically generated with low confidence
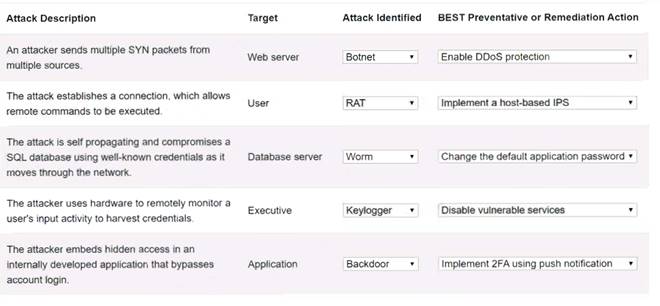
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 7
A cybersecurity administrator needs to allow mobile BYOD devices to access network resources. As the devices are not enrolled to the domain and do not have policies applied to them, which of the following are best practices for authentication and infrastructure security? (Select TWO).
- A. Create a new network for the mobile devices and block the communication to the internal network and servers
- B. Use a captive portal for user authentication.
- C. Authenticate users using OAuth for more resiliency
- D. Implement SSO and allow communication to the internal network
- E. Use the existing network and allow communication to the internal network and servers.
- F. Use a new and updated RADIUS server to maintain the best solution
Answer: BC
Explanation:
When allowing mobile BYOD devices to access network resources, using a captive portal for user authentication and authenticating users using OAuth are both best practices for authentication and infrastructure security. A captive portal requires users to authenticate before accessing the network and can be used to enforce policies and restrictions. OAuth allows users to authenticate using third-party providers, reducing the risk of password reuse and credential theft. References: CompTIA Security+ Study Guide, pages 217-218, 225-226
NEW QUESTION 8
Which of the following environment utilizes dummy data and is MOST to be installed locally on a system that allows to be assessed directly and modified easily wit each build?
- A. Production
- B. Test
- C. Staging
- D. Development
Answer: D
Explanation:
The environment that utilizes dummy data and is most likely to be installed locally on a system that allows it to be assessed directly and modified easily with each build is the development environment. The development environment is used for developing and testing software and applications. It is typically installed on a local system, rather than on a remote server, to allow for easy access and modification. Dummy data can be used in the development environment to simulate real-world scenarios and test the software's functionality. References: https://www.techopedia.com/definition/27561/development-environment
NEW QUESTION 9
Which of the following would satisfy three-factor authentication requirements?
- A. Password, PIN, and physical token
- B. PIN, fingerprint scan, and ins scan
- C. Password, fingerprint scan, and physical token
- D. PIN, physical token, and ID card
Answer: C
Explanation:
Three-factor authentication combines three types of authentication methods: something you know (password), something you have (physical token), and something you are (fingerprint scan). Option C satisfies these requirements, as it uses a password (something you know), a physical token (something you have), and a fingerprint scan (something you are) for authentication.
Reference: CompTIA Security+ Study Guide (SY0-601) 7th Edition by Emmett Dulaney, Chuck Easttom Note: There could be other options as well that could satisfy the three-factor authentication requirements as
per the organization's security policies.
NEW QUESTION 10
An organization is concerned that ils hosted web servers are not running the most updated version of the software. Which of the following would work best to help identify potential vulnerabilities?
- A. hping3 -S compcia.org -p 80
- B. nc -1 -v comptia.crg -p 80
- C. nmap comptia.org -p 80 -sv
- D. nslookup -port«80 comptia.org
Answer: C
Explanation:
nmap is a network scanning tool that can perform various tasks such as port scanning, service detection, version detection, OS detection, vulnerability scanning, etc… nmap comptia.org -p 80 -sv is a command that scans port 80 (the default port for HTTP) on comptia.org domain name and tries to identify the service name and version running on that port. This can help identify potential vulnerabilities in the web server software by comparing the version with known exploits or patches.
NEW QUESTION 11
The Chief information Security Officer has directed the security and networking team to retire the use of shared passwords on routers and switches. Which of the following choices BEST meets the requirements?
- A. SAML
- B. TACACS+
- C. Password vaults
- D. OAuth
Answer: B
Explanation:
TACACS+ is a protocol used for remote authentication, authorization, and accounting (AAA) that can be used to replace shared passwords on routers and switches. It provides a more secure method of authentication that allows for centralized management of access control policies. References: CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 6
NEW QUESTION 12
An attacker was eavesdropping on a user who was shopping online. The attacker was able to spoof the IP address associated with the shopping site. Later, the user received an email regarding credit card statement with unusual purchases. Which of the following attacks took place?
- A. On-path attack
- B. Protocol poisoning
- C. Domain hijacking
- D. Bluejacking
Answer: A
Explanation:
An on-path attack is an attack that took place when an attacker was eavesdropping on a user who was shopping online and was able to spoof the IP address associated with the shopping site. An on-path attack is a type of network attack that involves intercepting or modifying traffic between two parties by placing oneself in the communication path. An on-path attack can also be called a man-in-the-middle attack or a session hijacking attack. An on-path attacker can steal sensitive information, such as credit card details, or redirect the user to a malicious website. References: https://www.comptia.org/blog/what-is-a-man-in-the-middle-attack
https://www.certblaster.com/wp-content/uploads/2020/11/CompTIA-Security-SY0-601-Exam-Objectives-1.0.pd
NEW QUESTION 13
An employee received multiple messages on a mobile device. The messages instructing the employee to pair the device to an unknown device. Which of the following BEST describes What a malicious person might be doing to cause this issue to occur?
- A. Jamming
- B. Bluesnarfing
- C. Evil twin
- D. Rogue access point
Answer: B
Explanation:
Bluesnarfing is a hacking technique that exploits Bluetooth connections to snatch data from a wireless device. An attacker can perform bluesnarfing when the Bluetooth function is on and your device is discoverable by other devices within range. In some cases, attackers can even make calls from their victim’s phon1e.
NEW QUESTION 14
Security engineers are working on digital certificate management with the top priority of making administration easier. Which of the following certificates is the best option?
- A. User
- B. Wildcard
- C. Self-signed
- D. Root
Answer: B
Explanation:
A wildcard certificate is a type of digital certificate that can be used to secure multiple subdomains under a single domain name. For example, a wildcard certificate for *.example.com can be used to secure www.example.com, mail.example.com, blog.example.com, etc. A wildcard certificate can make administration easier by reducing the number of certificates that need to be issued, managed, and renewed. It can also save costs and simplify configuration.
NEW QUESTION 15
A security architect is designing a remote access solution for a business partner. The business partner needs to access one Linux server at the company. The business partner wants to avid managing a password for authentication and additional software installation. Which of the following should the architect recommend?
- A. Soft token
- B. Smart card
- C. CSR
- D. SSH key
Answer: D
Explanation:
SSH key is a pair of cryptographic keys that can be used for authentication and encryption when connecting to a remote Linux server via SSH protocol. SSH key authentication does not require a password and is more secure than password-based authentication. SSH key authentication also does not require additional software installation on the client or the server, as SSH is a built-in feature of most Linux distributions. A business partner can generate an SSH key pair on their own computer and send the public key to the company, who can then add it to the authorized_keys file on the Linux server. This way, the business partner can access the Linux server without entering a password or installing any software
NEW QUESTION 16
......
100% Valid and Newest Version SY0-701 Questions & Answers shared by Dumps-hub.com, Get Full Dumps HERE: https://www.dumps-hub.com/SY0-701-dumps.html (New 0 Q&As)