SSCP | The Secret Of ISC2 SSCP Exam Dumps
Passleader SSCP Questions are updated and all SSCP answers are verified by experts. Once you have completely prepared with our SSCP exam prep kits you will be ready for the real SSCP exam without a problem. We have Abreast of the times ISC2 SSCP dumps study guide. PASSED SSCP First attempt! Here What I Did.
Free SSCP Demo Online For ISC2 Certifitcation:
NEW QUESTION 1
In a hierarchical PKI the highest CA is regularly called Root CA, it is also referred to by which one of the following term?
- A. Subordinate CA
- B. Top Level CA
- C. Big CA
- D. Master CA
Answer: B
Explanation:
Reference: Arsenault, Turner, Internet X.509 Public Key Infrastructure: Roadmap, Chapter "Terminology".
Also note that sometimes other terms such as Certification Authority Anchor (CAA) might be used within some government organization, Top level CA is another common term to indicate the top level CA, Top Level Anchor could also be used.
NEW QUESTION 2
As a result of a risk assessment, your security manager has determined that your organization needs to implement an intrusion detection system that can detect unknown attacks and can watch for unusual traffic behavior, such as a new service appearing on the network. What type of intrusion detection system would you select?
- A. Protocol anomaly based
- B. Pattern matching
- C. Stateful matching
- D. Traffic anomaly-based
Answer: D
Explanation:
Traffic anomaly-based is the correct choice. An anomaly based IDS can detect unknown attacks. A traffic anomaly based IDS identifies any unacceptable deviation from expected behavior based on network traffic.
Protocol anomaly based is not the best choice as while a protocol anomaly based IDS can identify unknown attacks, this type of system is more suited to identifying deviations from established protocol standards such as HTTP. This type of IDS faces problems in analyzing complex or custom protocols.
Pattern matching is not the best choice as a pattern matching IDS cannot identify unknown attacks. This type of system can only compare packets against signatures of known attacks.
Stateful matching is not the best choice as a statful matching IDS cannot identify unknown attacks. This type of system works by scanning traffic streams for patterns or signatures of attacks.
Reference:
Official guide to the CISSP CBK. pages 198 to 201
NEW QUESTION 3
Compared to RSA, which of the following is true of Elliptic Curve Cryptography(ECC)?
- A. It has been mathematically proved to be more secure.
- B. It has been mathematically proved to be less secure.
- C. It is believed to require longer key for equivalent security.
- D. It is believed to require shorter keys for equivalent security.
Answer: D
Explanation:
The following answers are incorrect: It has been mathematically proved to be less secure. ECC has not been proved to be more or less secure than RSA. Since ECC is newer than RSA, it is considered riskier by some, but that is just a general assessment, not based on mathematical arguments.
It has been mathematically proved to be more secure. ECC has not been proved to be more or less secure than RSA. Since ECC is newer than RSA, it is considered riskier by some, but that is just a general assessment, not based on mathematical arguments.
It is believed to require longer key for equivalent security. On the contrary, it is believed to require shorter keys for equivalent security of RSA.
Shon Harris, AIO v5 pg719 states:
"In most cases, the longer the key, the more protection that is provided, but ECC can provide the same level of protection with a key size that is shorter that what RSA requires"
The following reference(s) were/was used to create this question: ISC2 OIG, 2007 p. 258
Shon Harris, AIO v5 pg719
NEW QUESTION 4
Which of the following server contingency solutions offers the highest availability?
- A. System backups
- B. Electronic vaulting/remote journaling
- C. Redundant arrays of independent disks (RAID)
- D. Load balancing/disk replication
Answer: D
Explanation:
Of the offered technologies, load balancing/disk replication offers the highest availability, measured in terms of minutes of lost data or server downtime.
A Network-Attached Storage (NAS) or a Storage Area Network (SAN) solution combined with virtualization would offer an even higher availability.
Source: SWANSON, Marianne, & al., National Institute of Standards and Technology (NIST), NIST Special Publication 800-34, Contingency Planning Guide for Information Technology Systems, December 2001 (page 49).
NEW QUESTION 5
Which of the following firewall rules found on a firewall installed between an organization's internal network and the Internet would present the greatest danger to the internal network?
- A. Permit all traffic between local hosts.
- B. Permit all inbound ssh traffic.
- C. Permit all inbound tcp connections.
- D. Permit all syslog traffic to log-server.abc.org.
Answer: C
Explanation:
Any opening of an internal network to the Internet is susceptible of creating a new vulnerability.
Of the given rules, the one that permits all inbound tcp connections is the less likely to be used since it amounts to almost having no firewall at all, tcp being widely used on the Internet.
Reference(s) used for this question:
ALLEN, Julia H., The CERT Guide to System and Network Security Practices, Addison- Wesley, 2001, Appendix B, Practice-Level Policy Considerations (page 409).
NEW QUESTION 6
Which of the following is NOT a system-sensing wireless proximity card?
- A. magnetically striped card
- B. passive device
- C. field-powered device
- D. transponder
Answer: A
Explanation:
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, page 342.
NEW QUESTION 7
Risk reduction in a system development life-cycle should be applied:
- A. Mostly to the initiation phase.
- B. Mostly to the development phase.
- C. Mostly to the disposal phase.
- D. Equally to all phases.
Answer: D
Explanation:
Risk is defined as the combination of the probability that a particular threat source will exploit, or trigger, a particular information system vulnerability and the resulting mission impact should this occur. Previously, risk avoidance was a common IT security goal. That changed as the nature of the risk became better understood. Today, it is recognized that elimination of all risk is not cost-effective. A cost-benefit analysis should be conducted for each proposed control. In some cases, the benefits of a more secure system may not justify the direct and indirect costs. Benefits include more than just prevention of monetary loss; for example, controls may be essential for maintaining public trust and confidence. Direct costs include the cost of purchasing and installing a given technology; indirect costs include decreased system performance and additional training. The goal is to enhance mission/business capabilities by managing mission/business risk to an acceptable level.
Source: STONEBURNER, Gary & al, National Institute of Standards and Technology (NIST), NIST Special Publication 800-27, Engineering Principles for Information Technology Security (A Baseline for Achieving Security), June 2001 (page 8).
NEW QUESTION 8
Which of the following floors would be most appropriate to locate information processing facilities in a 6-stories building?
- A. Basement
- B. Ground floor
- C. Third floor
- D. Sixth floor
Answer: C
Explanation:
You data center should be located in the middle of the facility or the core of a building to provide protection from natural disasters or bombs and provide easier access to emergency crewmembers if necessary. By being at the core of the facility the external wall would act as a secondary layer of protection as well.
Information processing facilities should not be located on the top floors of buildings in case of a fire or flooding coming from the roof. Many crimes and theft have also been conducted by simply cutting a large hole on the roof.
They should not be in the basement because of flooding where water has a natural tendancy to flow down :-) Even a little amount of water would affect your operation
considering the quantity of electrical cabling sitting directly on the cement floor under under your raise floor.
The data center should not be located on the first floor due to the presence of the main entrance where people are coming in and out. You have a lot of high traffic areas such as the elevators, the loading docks, cafeteria, coffee shopt, etc.. Really a bad location for a data center.
So it was easy to come up with the answer by using the process of elimination where the top, the bottom, and the basement are all bad choices. That left you with only one possible answer which is the third floor.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, 5th Edition, Page 425.
NEW QUESTION 9
A confidential number used as an authentication factor to verify a user's identity is called a:
- A. PIN
- B. User ID
- C. Password
- D. Challenge
Answer: A
Explanation:
PIN Stands for Personal Identification Number, as the name states it is a combination of numbers.
The following answers are incorrect:
User ID This is incorrect because a Userid is not required to be a number and a Userid is only used to establish identity not verify it.
Password. This is incorrect because a password is not required to be a number, it could be any combination of characters.
Challenge. This is incorrect because a challenge is not defined as a number, it could be anything.
NEW QUESTION 10
Which of the following is defined as an Internet, IPsec, key-establishment protocol, partly based on OAKLEY, that is intended for putting in place authenticated keying material for use with ISAKMP and for other security associations?
- A. Internet Key exchange (IKE)
- B. Security Association Authentication Protocol (SAAP)
- C. Simple Key-management for Internet Protocols (SKIP)
- D. Key Exchange Algorithm (KEA)
Answer: A
Explanation:
RFC 2828 (Internet Security Glossary) defines IKE as an Internet, IPsec, key-establishment protocol (partly based on OAKLEY) that is intended for putting in place authenticated keying material for use with ISAKMP and for other security associations, such as in AH and ESP.
The following are incorrect answers:
SKIP is a key distribution protocol that uses hybrid encryption to convey session keys that are used to encrypt data in IP packets.
The Key Exchange Algorithm (KEA) is defined as a key agreement algorithm that is similar to the Diffie-Hellman algorithm, uses 1024-bit asymmetric keys, and was developed and formerly classified at the secret level by the NSA.
Security Association Authentication Protocol (SAAP) is a distracter. Reference(s) used for this question:
SHIREY, Robert W., RFC2828: Internet Security Glossary, may 2000.
NEW QUESTION 11
The DES algorithm is an example of what type of cryptography?
- A. Secret Key
- B. Two-key
- C. Asymmetric Key
- D. Public Key
Answer: A
Explanation:
DES is also known as a Symmetric Key or Secret Key algorithm.
DES is a Symmetric Key algorithm, meaning the same key is used for encryption and decryption.
For the exam remember that:
DES key Sequence is 8 Bytes or 64 bits (8 x 8 = 64 bits)
DES has an Effective key length of only 56 Bits. 8 of the Bits are used for parity purpose only.
DES has a total key length of 64 Bits. The following answers are incorrect:
Two-key This is incorrect because DES uses the same key for encryption and decryption.
Asymmetric Key This is incorrect because DES is a Symmetric Key algorithm using the same key for encryption and decryption and an Asymmetric Key algorithm uses both a Public Key and a Private Key.
Public Key. This is incorrect because Public Key or algorithm Asymmetric Key does not use the same key is used for encryption and decryption.
References used for this question: http://en.wikipedia.org/wiki/Data_Encryption_Standard
NEW QUESTION 12
One purpose of a security awareness program is to modify:
- A. employee's attitudes and behaviors towards enterprise's security posture
- B. management's approach towards enterprise's security posture
- C. attitudes of employees with sensitive data
- D. corporate attitudes about safeguarding data
Answer: A
Explanation:
The Answer security awareness training is to modify employees behaviour and attitude towards towards enterprise's security posture.
Security-awareness training is performed to modify employees?? behavior and attitude toward security. This can best be achieved through a formalized process of security- awareness training.
It is used to increase the overall awareness of security throughout the company. It is targeted to every single employee and not only to one group of users.
Unfortunately you cannot apply a patch to a human being, the only thing you can do is to educate employees and make them more aware of security issues and threats. Never underestimate human stupidity.
Reference(s) used for this question:
TIPTON, Hal, (ISC)2, Introduction to the CISSP Exam presentation. also see:
Harris, Shon (2012-10-18). CISSP All-in-One Exam Guide, 6th Edition (p. 130). McGraw- Hill. Kindle Edition.
NEW QUESTION 13
Which layer of the DoD TCP/IP model controls the communication flow between hosts?
- A. Internet layer
- B. Host-to-host transport layer
- C. Application layer
- D. Network access layer
Answer: B
Explanation:
Whereas the host-to-host layer (equivalent to the OSI's transport layer) provides end-to-end data delivery service, flow control, to the application layer.
The four layers in the DoD model, from top to bottom, are:
The Application Layer contains protocols that implement user-level functions, such as mail delivery, file transfer and remote login.
The Host-to-Host Layer handles connection rendez vous, flow control, retransmission of lost data, and other generic data flow management between hosts. The mutually exclusive TCP and UDP protocols are this layer's most important members.
The Internet Layer is responsible for delivering data across a series of different physical networks that interconnect a source and destination machine. Routing protocols are most closely associated with this layer, as is the IP Protocol, the Internet's fundamental protocol.
The Network Access Layer is responsible for delivering data over the particular hardware media in use. Different protocols are selected from this layer, depending on the type of physical network
The OSI model organizes communication services into seven groups called layers. The layers are as follows:
Layer 7, The Application Layer: The application layer serves as a window for users and application processes to access network services. It handles issues such as network transparency, resource allocation, etc. This layer is not an application in itself, although some applications may perform application layer functions.
Layer 6, The Presentation Layer: The presentation layer serves as the data translator for a network. It is usually a part of an operating system and converts incoming and outgoing data from one presentation format to another. This layer is also known as syntax layer. Layer 5, The Session Layer: The session layer establishes a communication session between processes running on different communication entities in a network and can
support a message-mode data transfer. It deals with session and connection coordination. Layer 4, The Transport Layer: The transport layer ensures that messages are delivered in the order in which they are sent and that there is no loss or duplication. It ensures complete data transfer. This layer provides an additional connection below the Session layer and assists with managing some data flow control between hosts. Data is divided into packets on the sending node, and the receiving node's Transport layer reassembles the message from packets. This layer is also responsible for error checking to guarantee error-free data delivery, and requests a retransmission if necessary. It is also responsible for sending acknowledgments of successful transmissions back to the sending host. A number of protocols run at the Transport layer, including TCP, UDP, Sequenced Packet Exchange (SPX), and NWLink.
Layer 3, The Network Layer: The network layer controls the operation of the subnet. It determines the physical path that data takes on the basis of network conditions, priority of service, and other factors. The network layer is responsible for routing and forwarding data packets.
Layer 2, The Data-Link Layer: The data-link layer is responsible for error free transfer of data frames. This layer provides synchronization for the physical layer. ARP and RARP would be found at this layer.
Layer 1, The Physical Layer: The physical layer is responsible for packaging and transmitting data on the physical media. This layer conveys the bit stream through a network at the electrical and mechanical level.
See a great flash animation on the subject at: http://www.maris.com/content/applets/flash/comp/fa0301.swf
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the
Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 85).
Also: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, chapter 7: Telecommunications and Network Security (page 344).
NEW QUESTION 14
Which xDSL flavour can deliver up to 52 Mbps downstream over a single copper twisted pair?
- A. VDSL
- B. SDSL
- C. HDSL
- D. ADSL
Answer: A
Explanation:
Very-high data-rate Digital Subscriber Line (VDSL) can deliver up to 52 Mbps downstream over a single copper twisted pair over a relatively short distance (1000 to 4500 feet).
DSL (Digital Subscriber Line) is a modem technology for broadband data access over ordinary copper telephone lines (POTS) from homes and businesses. xDSL refers collectively to all types of DSL, such as ADSL (and G.Lite), HDSL, SDSL, IDSL and VDSL
etc. They are sometimes referred to as last-mile (or first mile) technologies because they are used only for connections from a telephone switching station to a home or office, not between switching stations.
xDSL is similar to ISDN in as much as both operate over existing copper telephone lines (POTS) using sophisticated modulation schemes and both require the short runs to a central telephone office
Graphic below from: http://computer.howstuffworks.com/vdsl3.htm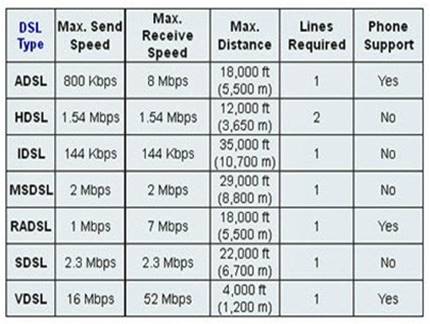
C:\Users\MCS\Desktop\1.jpg DSL speed chart
The following are incorrect answers:
Single-line Digital Subscriber Line (SDSL) deliver 2.3 Mbps of bandwidth each way. High-rate Digital Subscriber Line (HDSL) deliver 1.544 Mbps of bandwidth each way.
ADSL delivers a maximum of 8 Mbps downstream for a total combined speed of almost 9 Mbps up and down.
Reference used for this question:
http://computer.howstuffworks.com/vdsl3.htm and http://www.javvin.com/protocolxDSL.html and
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 115).
NEW QUESTION 15
The fact that a network-based IDS reviews packets payload and headers enable which of the following?
- A. Detection of denial of service
- B. Detection of all viruses
- C. Detection of data corruption
- D. Detection of all password guessing attacks
Answer: A
Explanation:
Because a network-based IDS reviews packets and headers, denial of service attacks can also be detected.
This question is an easy question if you go through the process of elimination. When you see an answer containing the keyword: ALL It is something a give away that it is not the proper answer. On the real exam you may encounter a few question where the use of the work ALL renders the choice invalid. Pay close attention to such keyword.
The following are incorrect answers:
Even though most IDSs can detect some viruses and some password guessing attacks, they cannot detect ALL viruses or ALL password guessing attacks. Therefore these two answers are only detractors.
Unless the IDS knows the valid values for a certain dataset, it can NOT detect data corruption.
Reference used for this question:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 48.
NEW QUESTION 16
ICMP and IGMP belong to which layer of the OSI model?
- A. Datagram Layer.
- B. Network Layer.
- C. Transport Layer.
- D. Data Link Layer.
Answer: B
Explanation:
The network layer contains the Internet Protocol (IP), the Internet Control Message Protocol (ICMP), and the Internet Group Management Protocol (IGMP)
The following answers are incorrect:
Datagram Layer. Is incorrect as a distractor as there is no Datagram Layer.
Transport Layer. Is incorrect because it is used to data between applications and uses the TCP and UDP protocols.
Data Link Layer. Is incorrect because this layer deals with addressing hardware.
NEW QUESTION 17
Which conceptual approach to intrusion detection system is the most common?
- A. Behavior-based intrusion detection
- B. Knowledge-based intrusion detection
- C. Statistical anomaly-based intrusion detection
- D. Host-based intrusion detection
Answer: B
Explanation:
There are two conceptual approaches to intrusion detection. Knowledge- based intrusion detection uses a database of known vulnerabilities to look for current attempts to exploit them on a system and trigger an alarm if an attempt is found. The other approach, not as common, is called behaviour-based or statistical analysis-based. A host- based intrusion detection system is a common implementation of intrusion detection, not a conceptual approach.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 63).
Also: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, chapter 4: Access Control (pages 193-194).
NEW QUESTION 18
Which expert system operating mode allows determining if a given hypothesis is valid?
- A. Blackboard
- B. Lateral chaining
- C. Forward chaining
- D. Backward chaining
Answer: D
Explanation:
Backward-chaining mode - the expert system backtracks to determine if a given hypothesis is valid. Backward-chaining is generally used when there are a large number of possible solutions relative to the number of inputs.
Incorrect answers are:
In a forward-chaining mode, the expert system acquires information and comes to a conclusion based on that information. Forward-chaining is the reasoning approach that can be used when there is a small number of solutions relative to the number of inputs.
Blackboard is an expert system-reasoning methodology in which a solution is generated by the use of a virtual blackboard, wherein information or potential solutions are placed on the blackboard by a plurality of individuals or expert knowledge sources. As more information is placed on the blackboard in an iterative process, a solution is generated.
Lateral-chaining mode - No such expert system mode. Sources:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 7: Applications and Systems Development (page 259).
KRUTZ, Ronald & VINES, Russel, The CISSP Prep Guide: Gold Edition, Wiley Publishing Inc., 2003, Chapter 7: Expert Systems (page 354).
NEW QUESTION 19
......
P.S. Thedumpscentre.com now are offering 100% pass ensure SSCP dumps! All SSCP exam questions have been updated with correct answers: https://www.thedumpscentre.com/SSCP-dumps/ (1074 New Questions)