GCIH | All About Practical GCIH Test Question
Your success in GIAC GCIH is our sole target and we develop all our GCIH braindumps in a way that facilitates the attainment of this target. Not only is our GCIH study material the best you can find, it is also the most detailed and the most updated. GCIH Practice Exams for GIAC GCIH are written to the highest standards of technical accuracy.
Also have GCIH free dumps questions for you:
NEW QUESTION 1
Maria works as a professional Ethical Hacker. She has been assigned the project of testing the security of www.gentech.com. She is using dumpster diving to gather information about Gentech Inc.
In which of the following steps of malicious hacking does dumpster diving come under?
- A. Multi-factor authentication
- B. Role-based access control
- C. Mutual authentication
- D. Reconnaissance
Answer: D
NEW QUESTION 2
Which of the following statements about Ping of Death attack is true?
- A. In this type of attack, a hacker sends more traffic to a network address than the buffer can handle.
- B. This type of attack uses common words in either upper or lower case to find a password.
- C. In this type of attack, a hacker maliciously cuts a network cable.
- D. In this type of attack, a hacker sends ICMP packets greater than 65,536 bytes to crash a system.
Answer: D
NEW QUESTION 3
910 ms 15 0.so-7-0-0.XL1.MIA4.ALTER.NET (152.63.86.189) 51.165 ms 49.935 ms
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 4
John works as a Professional Ethical Hacker for NetPerfect Inc. The company has a Linux-based network. All client computers are running on Red Hat 7.0 Linux. The Sales Manager of the company complains to John that his system contains an unknown package named as tar.gz and his documents are exploited. To resolve the problem, John uses a Port scanner to enquire about the open ports and finds out that the HTTP server service port on 27374 is open. He suspects that the other computers on the network are also facing the same problem. John discovers that a malicious application is using the synscan tool to randomly generate IP addresses.
Which of the following worms has attacked the computer?
- A. Code red
- B. Ramen
- C. LoveLetter
- D. Nimda
Answer: B
NEW QUESTION 5
Choose the correct six -step process of threat modeling from the list of different steps.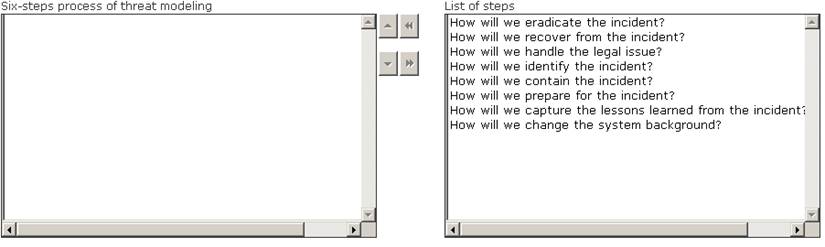
Solution:
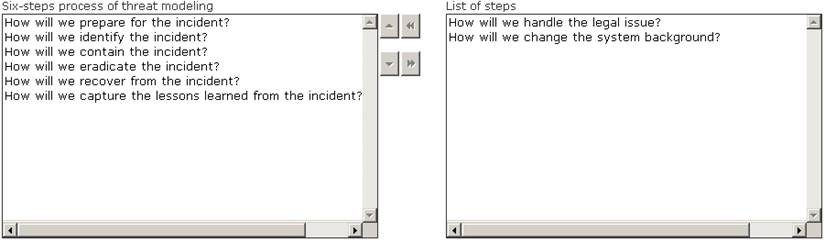
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 6
In which of the following attacks does an attacker create the IP packets with a forged (spoofed) source IP address with the purpose of concealing the identity of the sender or impersonating another computing system?
- A. Rainbow attack
- B. IP address spoofing
- C. Cross-site request forgery
- D. Polymorphic shell code attack
Answer: B
NEW QUESTION 7
Rick works as a Professional Ethical Hacker for Exambible Inc. The company has opened a new branch that uses Windows-based computers. Rick has been assigned a project to check the network security of the new branch office. He wants to ensure that the company is free from remote hacking attacks.
Choose the appropriate steps that Rick should perform to accomplish the task. 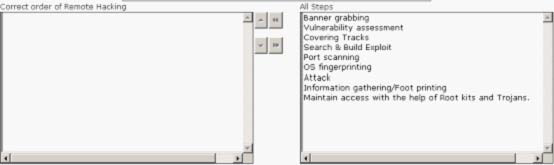
Solution:
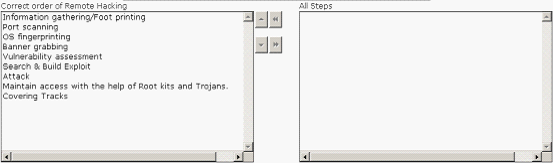
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
Adam works as a Network Administrator for Exambible Inc. He wants to prevent the network from DOS attacks. Which of the following is most useful against DOS attacks?
- A. SPI
- B. Distributive firewall
- C. Honey Pot
- D. Internet bot
Answer: A
NEW QUESTION 9
Which of the following is a process of searching unauthorized modems?
- A. Espionage
- B. Wardialing
- C. System auditing
- D. Scavenging
Answer: B
NEW QUESTION 10
Which of the following tools are used as a network traffic monitoring tool in the Linux operating system?
Each correct answer represents a complete solution. Choose all that apply.
- A. Netbus
- B. IPTraf
- C. MRTG
- D. Ntop
Answer: BCD
NEW QUESTION 11
Maria works as a professional Ethical Hacker. She recently got a project to test the security of www.we-are-secure.com. Arrange the three pre -test phases of the attack to test the security of weare-secure.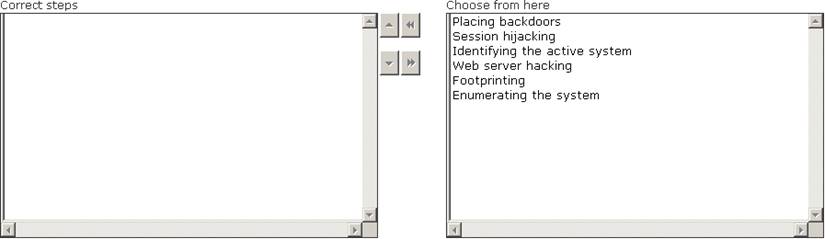
Solution:
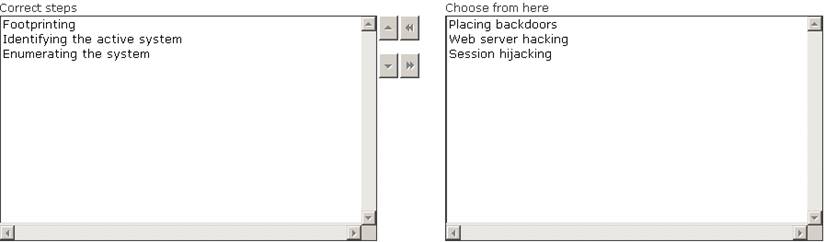
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 12
Which of the following programs can be used to detect stealth port scans performed by a malicious hacker?
Each correct answer represents a complete solution. Choose all that apply.
- A. nmap
- B. scanlogd
- C. libnids
- D. portsentry
Answer: BCD
NEW QUESTION 13
Which of the following statements about a Trojan horse are true?
Each correct answer represents a complete solution. Choose two.
- A. It is a macro or script that attaches itself to a file or template.
- B. The writers of a Trojan horse can use it later to gain unauthorized access to a computer.
- C. It is a malicious software program code that resembles another normal program.
- D. It infects the boot record on hard disks and floppy disks.
Answer: BC
NEW QUESTION 14
OutGuess is used for __________ attack.
- A. Steganography
- B. Web password cracking
- C. SQL injection
- D. Man-in-the-middle
Answer: A
NEW QUESTION 15
5.2.92:4079 ---------FIN--------->192.5.2.110:23192.5.2.92:4079 <----NO RESPONSE---
---192.5.2.110:23
Scan directed at closed port:
ClientServer
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
Which of the following describes network traffic that originates from the inside of a network perimeter and progresses towards the outside?
- A. Ingress network
- B. Inwards network
- C. Egress network
- D. Outwards network
Answer: C
NEW QUESTION 17
Choose the items from the given list that are required to be in the response kit of an Incident Handler.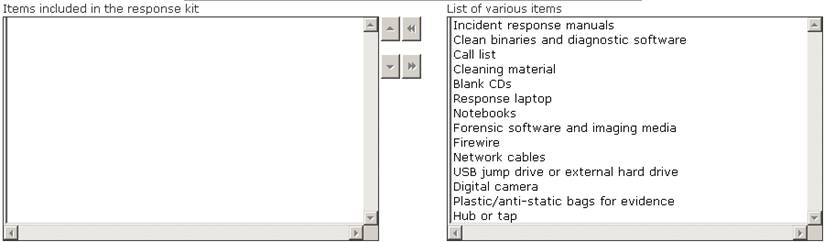
Solution:
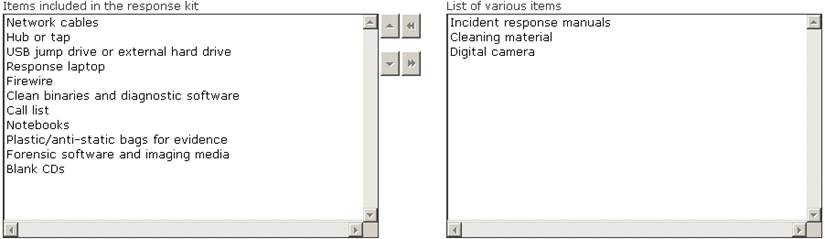
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 18
......
P.S. Easily pass GCIH Exam with 328 Q&As Certshared Dumps & pdf Version, Welcome to Download the Newest Certshared GCIH Dumps: https://www.certshared.com/exam/GCIH/ (328 New Questions)