70-346 | High value 70-346 Exam Questions and Answers 2021
70 346 pdf for Microsoft certification, Real Success Guaranteed with Updated exam ref 70 346 pdf. 100% PASS 70-346 Managing Office 365 Identities and Requirements exam Today!
Check 70-346 free dumps before getting the full version:
NEW QUESTION 1
You are the Office 365 administrator for your company.
Users report that their passwords expire too frequently, and they do not receive adequate notice of password expiration.
Account passwords must remain active for the longest duration allowed. Users must receive password expiration notifications as early as possible.
You need to configure the password expiration policy.
How should you set the policy on the password page of the Office 365 admin center? To answer, drag the appropriate duration to the correct location. Each duration may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.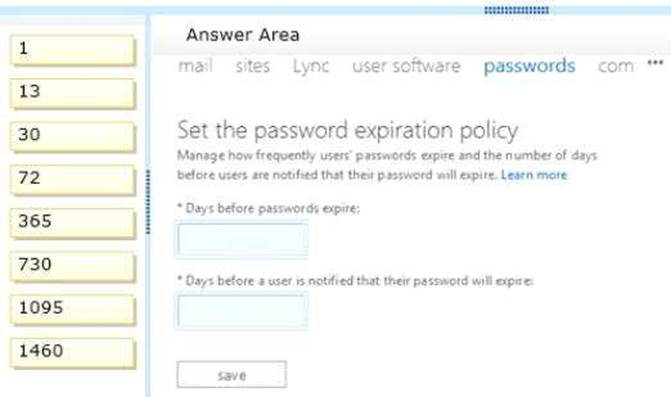
Answer:
Explanation: The maximum number of days you can set the 'Days before password expire' to is 730. This will make the
password valid for the longest duration.
To be notified as early as possible on that the password is about to expire, we should set the maximum value, which is 30, to the ' days before users are notified that their password will expire' setting.
Note: Set a user's password expiration policy References:
https://support.office.com/en-us/article/Set-a-users-password-expiration-policy-0f54736f-eb22-414c-8273-498a
NEW QUESTION 2
You deploy Office 365.
You need to activate Rights Management. Which method should you use?
- A. the set-xdsconf iguration Windows PowerShell cmdlet
- B. the Active Directory Administrative Center console
- C. the Office 365 admin center
- D. the Enable-AadrmDevicePlatform Windows PowerShell Cmdlet
Answer: C
Explanation: Once you have signed up for an Office 365 plan that includes Rights Management, sign in to Office 365 with a work or school account that has the global administrator role for your Office 365 deployment. You should then navigate to the rights management page via Settings > Services & add-ins > Microsoft Azure Information Protection > Manage Microsoft Azure Information Protection settings. On the rights management page, click activate.
References: https://docs.microsoft.com/en-us/information-protection/deploy-use/activate-office365
NEW QUESTION 3
Your company has a main office and a branch office. Both offices are directly connected to the Internet. The branch office connection to the Internet has limited bandwidth.
The company deploys Microsoft Skype for Business Online.
You need to ensure that users in the branch office can only use instant messaging (IM) while using Skype for Business Online. The users must be prevented from connecting to audio or video conferences.
What should you do?
- A. On the firewall at the branch office, block all of the outbound traffic on port 5061.
- B. From the Office 365 portal, modify the user properties of each user in the branch office.
- C. From the Office 365 portal, configure the license settings of each user in the branch office.
- D. Deploy only the Skype for Business Attendee client to all of the users in the branch office.
Answer: B
NEW QUESTION 4
You are the Office 365 administrator for your company. The environment must support single sign-on.
You need to install the required certificates.
Which two certificates should you install? Each correct answer presents part of the solution.
- A. Secure Sockets Layer (SSL)
- B. Privacy-enhanced mail (PEM)
- C. Token signing
- D. Personal
- E. Software publisher
Answer: AC
Explanation: Certificates are used to secure communications between federation servers, Web Application Proxies, federation server proxies, the cloud service, and web clients.
A: A Secure Sockets Layer (SSL) certificate is used to secure communications between federation servers, clients, Web Application Proxy, and federation server proxy computers.
C: A Token-signing certificate is a standard X.509 certificate that is used to securely sign all tokens that the federation server issues and that the cloud service will accept and validate.
NEW QUESTION 5
You deploy Office 365. You purchase 50 Office 365 Enterprise E1 licenses and assign the licenses to users. A sales department user leaves the company and is replaced.
You need to ensure that the new user has a valid license and can access email.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.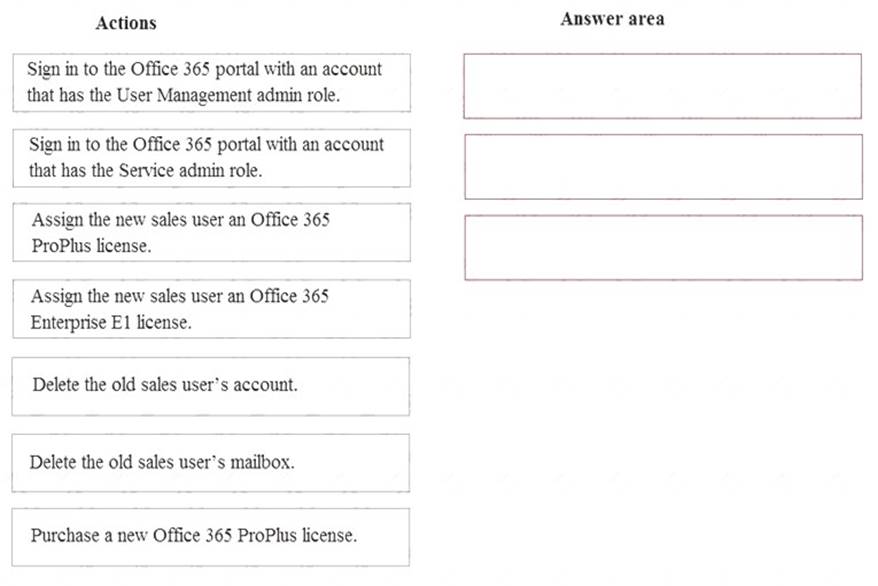
Answer:
Explanation: 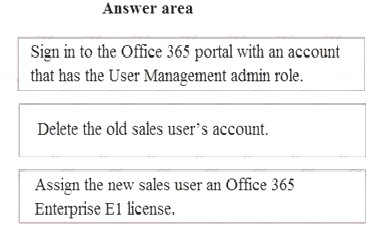
NEW QUESTION 6
Your company uses Office 365.
You need to prevent users from initiating remote wipes of mobile devices by using the Office 365 portal. What should you modify?
- A. the Outlook Web App mailbox policy
- B. the Exchange ActiveSync device policy
- C. the default role assignment policy
- D. the Exchange ActiveSync Access settings
Answer: B
Explanation: References: https://technet.microsoft.com/en-us/library/dn792010.aspx
NEW QUESTION 7
You need to gather the required report information for your email users. What should you do?
- A. In the Security & Compliance admin center, use the Top Mail Senders report.
- B. In the Exchange admin center, use the spam filter.
- C. In the Office 365 Admin center, use the Email Activity Usage report
- D. In the Office 365 Admin center, use the Top Rule Matches for Mail report.
- E. In the Security & Compliance admin center, use the Spam Detections report
Answer: A
Explanation: References:
https://docs.microsoft.com/en-us/office365/securitycompliance/view-email-security-reports#top-senders-and-rec
NEW QUESTION 8
You are the Office 365 administrator for a company. All employees have Active Directory Domain Services (AD DS) user accounts. All users accounts are part of an organizational unit (OU) and are members of a security group.
You deploy Azure Active Directory (Azure AD) Connect by using the Express Settings.
You plan to provision user accounts to Office 365. Only employee user accounts should be synchronized to Office 365.
You need to enable filtering for Azure AD Connect.
Which two types of filtering can you use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A. Domain-based
- B. OU-based
- C. Group-based
- D. Attribute-based
Answer: BD
Explanation: All four types of filtering can be used. However, domain-based and group-based filtering can only be configured on installation.
References:
https://docs.microsoft.com/en-us/azure/active-directory/connect/active-directory-aadconnectsync-configure-filte
NEW QUESTION 9
An organization has an Office 365 tenant. You use multi-factor authentication for all privileged accounts. User1 is on an extended leave of absence
You must configure the mailbox for User1 to forward to User2. You need to configure forwarding for User1’s mailbox.
Which two Actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A. Create an app password for the administrator account.
- B. Launch the Exchange Admin Center.
- C. Connect to Exchange Online by using Remote PowerShell.
- D. Launch Windows PowerShell as an administrator.
Answer: A
NEW QUESTION 10
Fabrikam Inc. plans to use the domain fabrikam.com for Office 365 user identities, email addresses, Session Initiation Protocol (SIP) addresses, and a public-facing home page.
Single sign-on (SSO) between Office 365 and the on-premises Active Directory is NOT required. You need to configure the Office 365 plan.
Which four Windows PowerShell cmdlets should you run in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.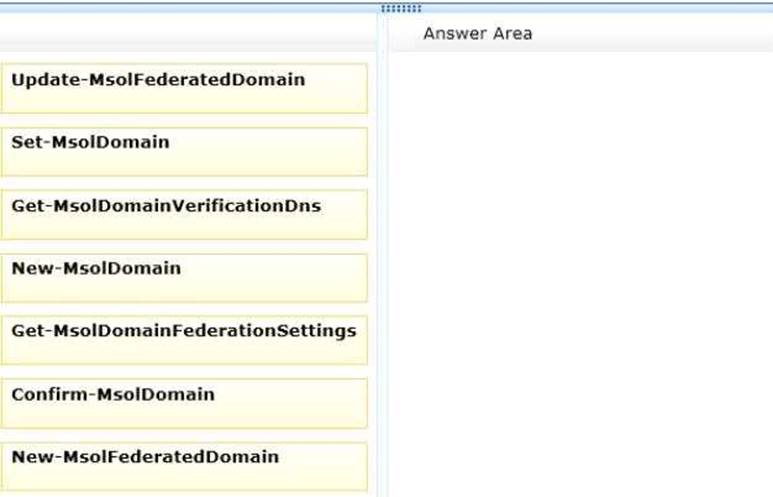
Answer:
Explanation: Box1. First we need to add the domain.
The New-MsolDomain cmdlet is used to create a new domain object. This cmdlet can be used to create a
domain with managed or federated identities.
Box2. Next we need to check the DNS before the domain can be confirmed.
The Get-MsolDomainVerificationDns cmdlet is used to return the DNS records that need to be set to verify a domain.
Box3. Now we can confirm the domain.
The Confirm-MsolDomain cmdlet is used to confirm ownership of a domain. In order to confirm ownership, a custom TXT or MX DNS record must be added for the domain. The domain must first be added using the New-MsolDomain cmdlet (step 1), and then the Get-MsolDomainVerificationDNS cmdlet (step 2) should be called to retrieve the details of the DNS record that must be set.
Box4. Next we can set fabrikam.com as the default domain.
The Set-MsolDomain cmdlet is used to update settings for a domain. This cmdlet can be used to change the default domain setting for the company.
NEW QUESTION 11
A company deploys an Office 365 tenant. All employees use Skype for Business Online. You need to configure the network firewall to support Skype for Business Online.
Which ports must you open? To answer, drag the appropriate port number to the correct feature or features. Each port number may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.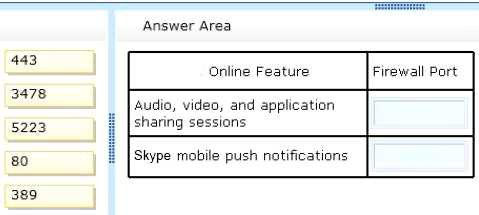
Answer:
Explanation: Transport Control Protocol(TCP), User Datagram Protocol(UDP) ports, and Protocol Numbers are important to TCP/IP networking, intranets, and the Internet. Ports and protocol numbers provide access to a host computer. However, they also create a security hazard by allowing uninvited access. Therefore, knowing which port to allow or disable increases a network's security. If the wrong ports or protocol numbers are disabled on a firewall, router, or proxy server as a security measure, essential services might become unavailable.
Port 443 is used for Audio, video and application sharing sessions as well as data sharing sessions - For HTTPS.
Port 5223 is used for mobile push notifications - Extensible Messaging and Presence Protocol (XMPP) client connection over SSL.
NEW QUESTION 12
You are the Microsoft Skype for Business administrator for a company that uses Skype for Business Online. The company has mandated that employees may use Skype for Business Online to communicate with contacts from approved external domains.
You need to configure Skype for Business Online to allow Skype for Business federation with only three specific domains.
You must achieve this goal by using the least amount of administrative effort.
Which two actions should you perform? Each correct answer presents part of the solution.
- A. In the Skype for Business admin center, set the External Access option to On except for blocked domains.
- B. In the Office 365 admin center, add the three domains to the domain list and set the domain intent for each domain to Skype for Business Online.
- C. In the Skype for Business admin center, set the External Access option to Off completely.
- D. In the Skype for Business admin center, set the External Access option to On only for allowed domains.
- E. In the Skype for Business admin center, configure the Presence Privacy Mode option to display presence information only to the users' contacts.
- F. In the Skype for Business admin center, add the three domains to the Blocked Or Allowed Domains list.
Answer: DF
Explanation: References:
http://technet.microsoft.com/en-us/library/hh852512.aspx http://
technet.microsoft.com/enus/library/jj205126.aspx
NEW QUESTION 13
A company has an Office 365 tenant.
You must reset the password for an account named User1.
You need to ensure that the new password for the account meets complexity rules. Which two passwords can you use? Each correct answer presents a complete solution.
- A. Summer2015
- B. May2015
- C. User1User1
- D. summer2015
- E. May 2015
- F. summer!@#$
- G. M1crosoft
Answer: AG
Explanation: If the user is set to require a strong password, then all of the following rules must be met:  The password must contain at least one lowercase letter.
The password must contain at least one lowercase letter. The password must contain at least one uppercase letter.
The password must contain at least one uppercase letter. The password must contain at least one non-alphanumeric character.
The password must contain at least one non-alphanumeric character.  The password cannot contain any spaces, tabs, or line breaks.
The password cannot contain any spaces, tabs, or line breaks. The length of the password must be 8-16 characters.
The length of the password must be 8-16 characters.  The user name cannot be contained in the password.
The user name cannot be contained in the password.
References:
https://docs.microsoft.com/en-us/azure/active-directory/active-directory-passwords-policy
NEW QUESTION 14
An organization uses Exchange Online.
You enable mailbox audit logging for all mailboxes.
User1 reports that her mailbox has been accessed by someone else.
You need to determine whether someone other than the mailbox owner has accessed the mailbox.
What should you do?
- A. Run the following Windows PowerShell command:Search-MailboxAuditLog -Identity User1-LogonTypes Owner -ShowDetails
- B. In the Exchange Admin Center, navigate to the Auditing section of the Protection page.Run a non-owner mailbox access report
- C. Run the following Windows PowerShell command:New-AdminAuditLogSearch -Identity User1-LogonTypes Owner -ShowDetails
- D. In the Exchange Admin Center, navigate to the Auditing section of the Compliance Management page.Run a non-owner mailbox access report.
Answer: D
Explanation: References: https://technet.microsoft.com/en-us/library/jj150575(v=exchg.150).aspx
NEW QUESTION 15
The legal department in your organization creates standardized disclaimers for all of their email messages. The disclaimers explain that any transmissions that are received in error should be reported back to the sender. You track any confidential documents that are attached to email messages.
Your security team reports that an employee may have mistakenly sent an email message that contained confidential information.
You need to identify whether the email message included the disclaimer and whether it contained confidential information.
Which two options should you configure? To answer, select the appropriate objects in the answer area.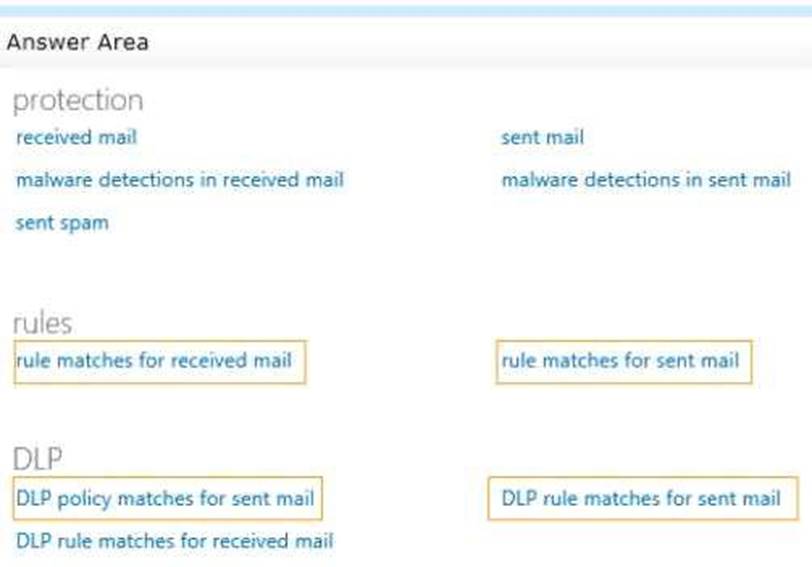
Answer:
Explanation: DLP stands for DataLossPrevention. A DLP policy is used to define exactly what constitutes a confidential email. For example: any email that has a credit card number of bank account number would be deemed to be confidential.
The DLP policy matches for sent mail report is used to display which emails contained content that matched a condition defined in a DLP policy. The DLP policy matches for sent mail report can be downloaded as a table that lists every single email that matched a DLP policy. This would identify in this question if the email did actually contain confidential information.
To identify whether the email message included the disclaimer, we need to view the “rule matches for sent mail” report. The disclaimer is added to an email by a transport rule. The rule defines which emails should have the disclaimer appended. A common example of this is all email sent to recipients outside the organization. By viewing the rule matches for sent mail, we can verify if the email in this question did match a rule and therefore did have the disclaimer appended.
NEW QUESTION 16
You have a SharePoint Online tenant. A user named User1 manages several site collections. User1 must be able to view the following information for the site collections: a list of side administrators
a list of side administrators the number of subsites in a site collection
the number of subsites in a site collection  storage and usage quotas
storage and usage quotas
You need to ensure that User1 can view the requested reports while minimizing the privileges that you grant to User1.
Which two permission levels can you assign to User1? Each correct answer presents a complete solution.
- A. Global admin
- B. SharePoint Online admin
- C. Site Collection admin
- D. Site admin
- E. User management admin
- F. Service admin
Answer: BC
Explanation: C: The Site collection administrator has permissions to manage a site collection.
B: Here are some of the key tasks users can do when they are assigned to the SharePoint Online admin role:  Create site collections
Create site collections Manage site collections and global settings
Manage site collections and global settings Assign site collection administrators to manage site collections
Assign site collection administrators to manage site collections  Manage site collection storage limits
Manage site collection storage limits Manage SharePoint Online user profiles
Manage SharePoint Online user profiles
References:
https://support.office.com/en-us/article/About-the-SharePoint-Online-admin-role-f08144d5-9d50-4922-8e77-4e
NEW QUESTION 17
Yen are the Office 365 administrator for your company.
You must use Windows PowerShell to manage cloud identities in Office 365. You must use a computer that runs Windows 10 to perform the management tasks.
You need to ensure that the Windows 10 computer has the necessary software installed. What should you install first?
- A. Windows PowerShell 4.0
- B. Azure Active Directory Rights Management Service
- C. Microsoft Online Services Sign-in Assistant
- D. Azure Identity Service
Answer: A
NEW QUESTION 18
You have an Office 365 environment. Synchronization between the on-premises Active Directory and Office 365 is enabled.
You need to deactivate directory synchronization. Which Windows PowerShell cmdlet should you run?
- A. Update-MsolFederatedDomain
- B. Remove-MsolDomain
- C. Remove-MsolFederatedDomain
- D. Set-MsolDirSyncEnabled
Answer: D
Explanation: The Set-MsolDirSyncEnabled cmdlet is used to enable or disable directory synchronization for a company. The complete command to disable directory Sync is Set-MsolDirSyncEnabled –EnableDirSync $false
References:
http://support.microsoft.com/kb/2619062
P.S. Easily pass 70-346 Exam with 356 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam 70-346 Dumps: https://www.surepassexam.com/70-346-exam-dumps.html (356 New Questions)